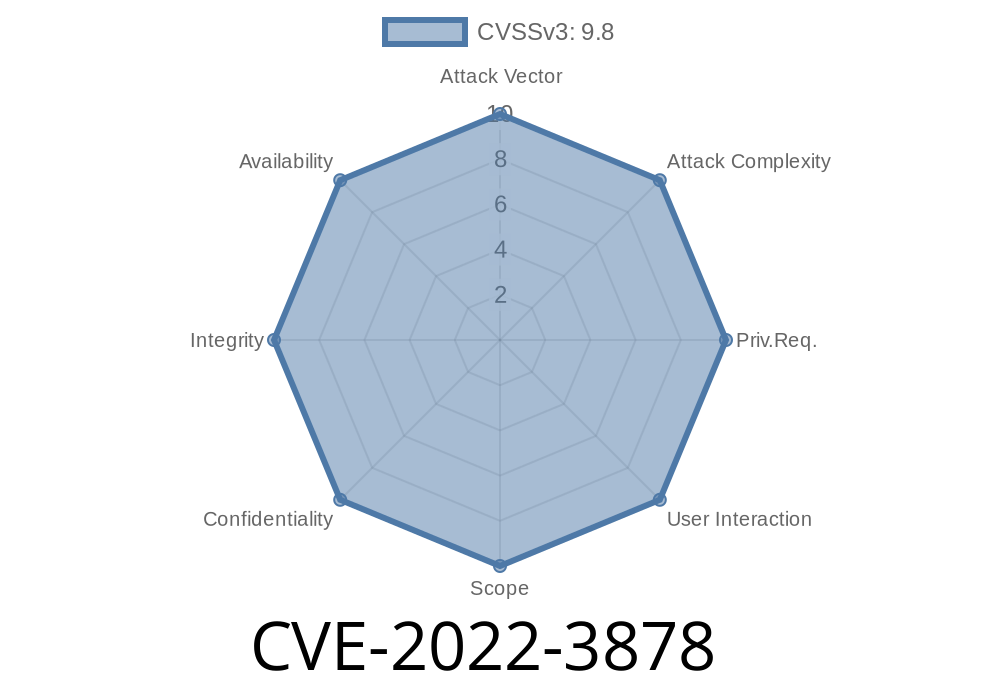
This bug affects Maxon ERP 2019 version 14.5.0 to 14.5.5. This bug was discovered by a hacker named Thomas, who published details on exploitations and the exploit code he used on his website. This bug can be exploited by remote attackers. The issue is related to the lack of input validation. This can lead to data manipulation and ultimately, remote code execution. An attacker can exploit this vulnerability to install malicious code on the targeted server. What Did We Learn? A critical vulnerability has been found in Maxon ERP. This affects an unknown part of the file /index.php/purchase_order/browse_data. The manipulation of the argument tb_search leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Critical ERP Vulnerability - CVE ID: 2022-3878
A critical vulnerability has been found in Maxon ERP. This affects an unknown part of the file /index.php/purchase_order/browse_data. The manipulation of the argument tb_search leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
This bug affects Maxon ERP 2019 version 14.5.0 to 14.5.5, but this issue also exists in older versions, like 13.4 and earlier as well as newer versions, like 15 and 16, so it’s best if you check your software for this bug ASAP!
Summary of the bug
A critical vulnerability has been found in Maxon ERP. This affects an unknown part of the file /index.php/purchase_order/browse_data. The manipulation of the argument tb_search leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Timeline
Published on: 11/07/2022 16:15:00 UTC
Last modified on: 11/09/2022 20:15:00 UTC