To fix this vulnerability, we strongly recommend users upgrade to Apache Calcite 1.32.0 or a newer version. In case you are currently using a previous version, then you should disable any of the operators mentioned above (which are enabled by default) in your application configuration. If you have enabled any of the operators mentioned above and are using a user under which the application is running that is vulnerable to this attack, then you should consider updating that user to a newer version of Apache Calcite. You can also restrict XML External Entity references in your application configuration.
References
The Apache Software Foundation released a security update for an XSS vulnerability in Apache Calcite. The vulnerability was discovered to be present in Apache Calcite version 1.30.0 or earlier and could allow an attacker to inject JavaScript code into the application's response.
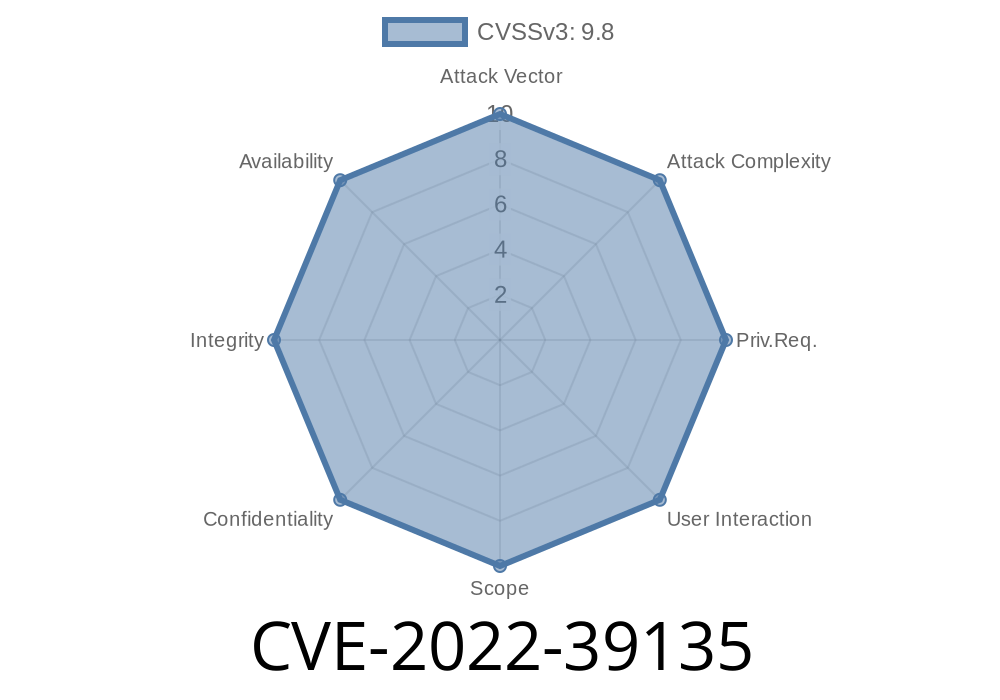
This vulnerability is CVE-2022-39135 and it has been assigned to the Apache Software Foundation by the vendor through MITRE.
A detailed report about this vulnerability can be found at https://issues.apache.org/jira/browse/CALCITE-465
To fix this vulnerability, we strongly recommend users upgrade to Apache Calcite 1.32.0 or a newer version
Introduction
This vulnerability is only triggered when the application uses an XML External Entity reference in unserializable state. As such, it impacts any user who has been authenticated and is using the vulnerable version of Apache Calcite.
The vulnerability can be mitigated by upgrading to a newer version of Apache Calcite.
If you have enabled any of the operators mentioned above, then you should consider updating those users to a newer version of Apache Calcite or disabling them from your application configuration.
Timeline
Published on: 09/11/2022 12:15:00 UTC
Last modified on: 09/15/2022 03:41:00 UTC