If you have a production use case where you require user authentication to be disabled for a host that is not allowed to access Arvados (such as an expired password), you will need to change the default setting for user authentication in the deployment group settings to LDAP. IMPORTANT: If you are upgrading to version 2.4.3, you will need to make sure that the user accounts in your system are migrated to LDAP before upgrading. If you apply the upgrade while user accounts are still Active Directory, it will fail because the upgrade will move the user accounts to LDAP and it is not possible to move user accounts over to LDAP. Workaround: After upgrading, you will need to migrate the user accounts to LDAP.
Authentication information for Arvados version 2.4.3
To meet the needs of production use cases, we have added a new authentication mechanism for Arvados. This authentication mechanism will change the default settings for user authentication in your deployment group settings to LDAP. If you are upgrading to version 2.4.3, you will need to make sure that the user accounts in your system are migrated to LDAP before upgrading or it will fail if they were populated with Active Directory credentials when you upgrade.
Version 2.4.3
Arvados 2.4.3 includes updates to the user authentication mechanism, which requires an LDAP deployment for production use cases that require disabling user authentication. If you are upgrading from 2.4.2 or earlier and have not updated the deployment group settings for LDAP, your deployment will fail on upgrade because the upgrade will move the accounts to LDAP and it is not possible to move accounts over to LDAP at this time.
Workaround: After upgrading, you will need to migrate your accounts over to LDAP.
Important APIs and Changes in Arvados 2.4.3
The changes in Arvados 2.4.3 are:
- The default configuration for user authentication has been changed to LDAP (LDAP is now the fallback if Active Directory is unavailable)
- There is a new deployment group type called "RSA-only" which enables you to disable user authentication on a production use case where you require an RSA key
- There is no longer a need to modify the default build script, as it will keep all the modules inside the correct location and not move any code into /usr/bin
How to Disable User Authentication to Arvados
General Information
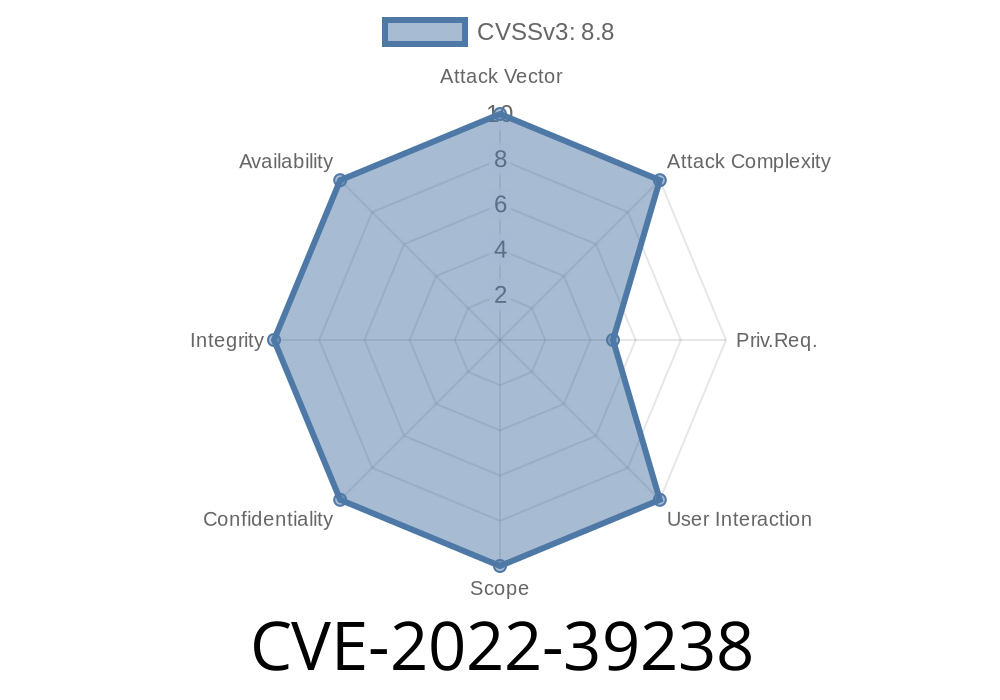
What is the CVE-2022-39238?
The CVE-2022-39238 is a vulnerability on Arvados that allows an attacker to gain access to your data and expose it, as well as be able to view your files. What does this vulnerability do?
The CVE-2022-39238 allows an attacker with privileged access to be able to view your files. How can I fix this vulnerability if I have not upgraded Arvados?
If you have not upgraded, there is no fix for the vulnerability. You will need to disable user authentication or remove the insecure deployment group settings.
Timeline
Published on: 09/23/2022 08:15:00 UTC
Last modified on: 09/26/2022 16:35:00 UTC