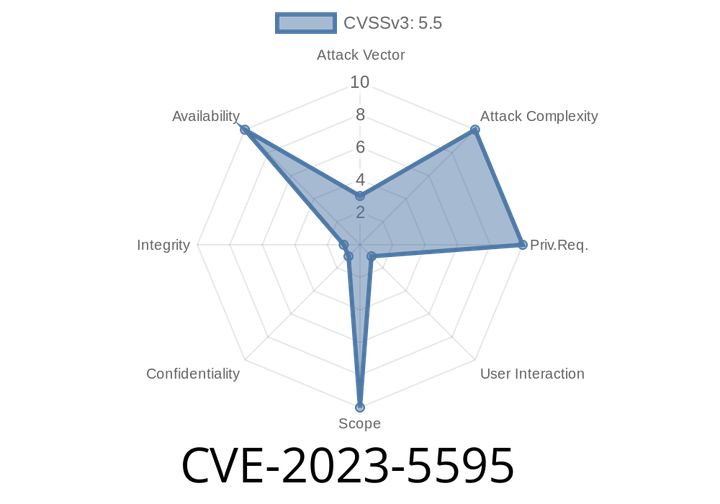
CVE-2023-5595 - Denial of Service in GPAC Media Framework (Before 2.3.-DEV) – Analysis, Exploit Demo, and Fix
The world of open-source multimedia software thrives on transparency and collaboration, but sometimes vulnerabilities slip through unnoticed. One such example is CVE-2023-5595, a Denial of
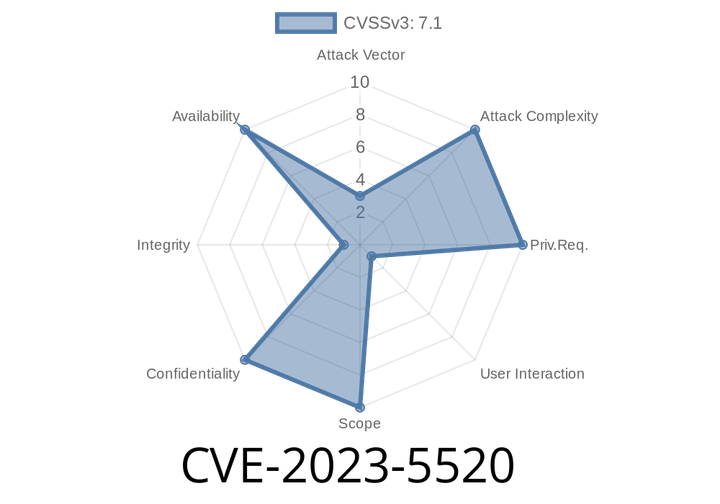
CVE-2023-5520 - Out-of-bounds Read Vulnerability in gpac/gpac prior to 2.2.2: Exploit Details, Code Snippet, and References
A newly discovered vulnerability, dubbed CVE-2023-5520, has recently been identified in the popular GitHub repository gpac/gpac. The issue relates to an out-of-bounds read in
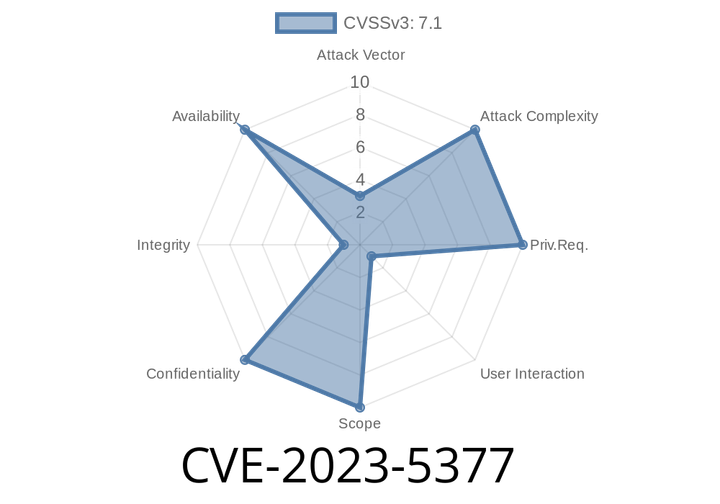
CVE-2023-5377 - Out-of-bounds Read Vulnerability in GPAC (gpac/gpac) Before v2.2.2-DEV—What You Need to Know, How It Works, and How to Stay Safe
GPAC is a popular open-source multimedia framework used for packaging, streaming, and playing multimedia content. It’s used in various industry projects and even in
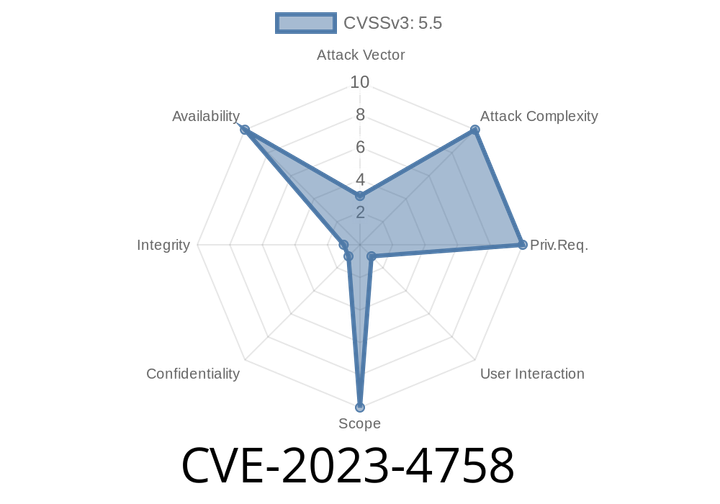
CVE-2023-4758 - Buffer Over-read in GPAC (gpac/gpac) Before 2.3-DEV — How it Works and Exploitation Details
The open-source multimedia framework GPAC (GitHub: gpac/gpac) is a flexible toolbox for media packaging and streaming. In 2023, the GPAC project reported CVE-2023-4758—a
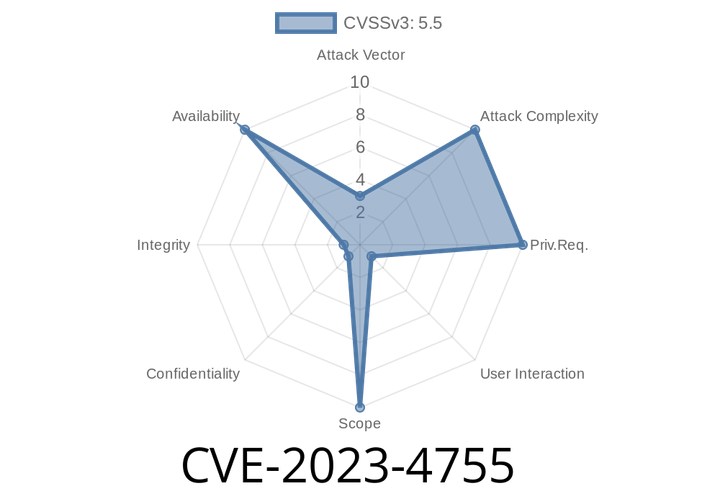
CVE-2023-4755 - How the Use-After-Free Bug in gpac/gpac <2.3-DEV Was Found and Exploited
In September 2023, a critical software bug was discovered in the popular open-source multimedia framework, gpac/gpac. Labeled CVE-2023-4755, this vulnerability is a Use-After-Free flaw
Episode
00:00:00
00:00:00