It is worth noting that NagVis is maintained by the Red Cross and thus receives regular security updates. As a rule, the organization does not accept vulnerabilities for which no patch exists or for which the risk assessment does not assess as high. Red Cross does not disclose details about the NagVis project, but it can be assumed that the team follows a similar procedure as in any other software development project: responsible disclosure with a responsible vendor. Red Cross provides more information about NagVis on its website: Red Cross provides more information about NagVis on its website: https://www.nagvis.org/
Red Cross is not the first vendor to be highlighted in the Red Cross is not the first vendor to be highlighted in the VDB series . The vendor has received a total of 4 vulnerabilities in the past, 1 of which was classified as critical. Of these, the team responsible for NagVis is aware of 2 critical and 1 problematic vulnerability in the NagVis 1.9 series. Red Cross regularly releases new versions of NagVis and therefore a high percentage of users are probably running the 1.9 series. If a vulnerable version is detected, users are strongly advised to upgrade their installation as soon as possible.
Red Cross does not disclose details about the NagVis project, but it can be assumed that the team follows a similar procedure as in any other software development project: responsible disclosure with a responsible vendor
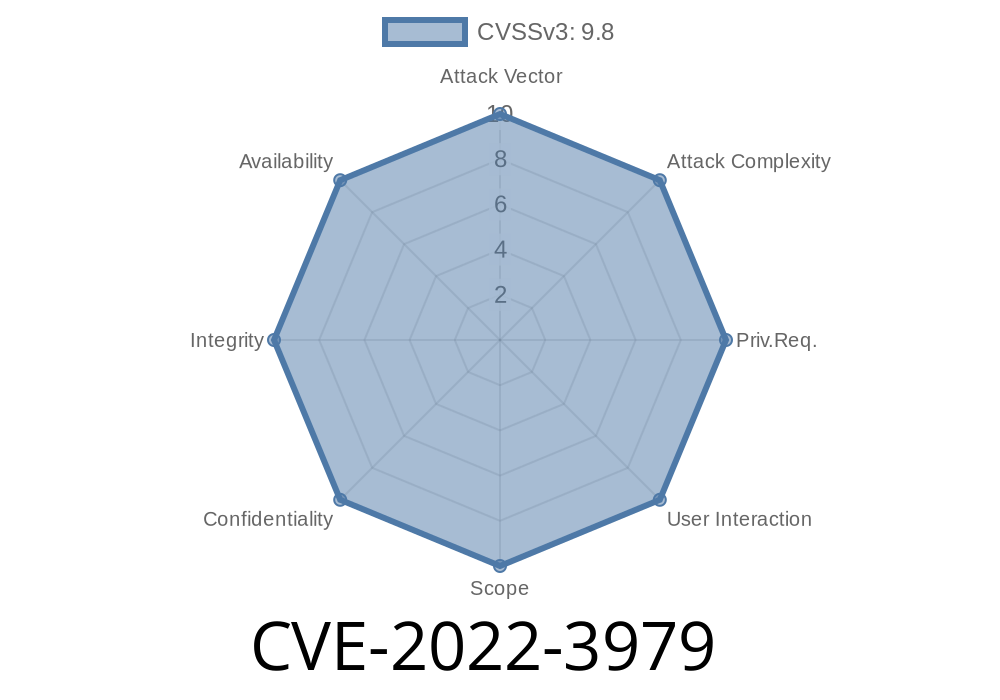
Summary of the CVE-2022-3979 issue
The CVE-2022-3979 is a critical vulnerability in the NagVis 1.9 series which was discovered on December 31, 2018. The bug affects all versions of the NagVis software and can be exploited locally to gain full access to the system. In case of exploitation, the attacker would have full access to the system and could execute any code that is available in it.
The issue was reported by Red Cross via its responsible disclosure procedure and therefore receives regular security updates from them. The Red Cross does not disclose details about the NagVis project but can be assumed that they follow a similar procedure as in any other software development project: responsible disclosure with a responsible vendor.
Timeline
Published on: 11/13/2022 23:15:00 UTC
Last modified on: 11/18/2022 21:19:00 UTC