An attacker would need to be in a position where they have access to the local system. This can be achieved by compromising another system on the same network, or by using remote access tools such as Team Viewer or VNC. Once a remote attacker has access to a vulnerable system, they could exploit the local privilege escalation vulnerability to run low-privileged code with elevated privileges. This could allow the attacker to install malicious software, view or change sensitive information, or even gain remote access to the target system. Note: Trend Micro products are designed to monitor the behaviour of the systems running these products, identifying suspicious activity and alerting administrators to take action. However, even if an attacker is not detected, this does not mean that the attack does not occur.
Vulnerability details
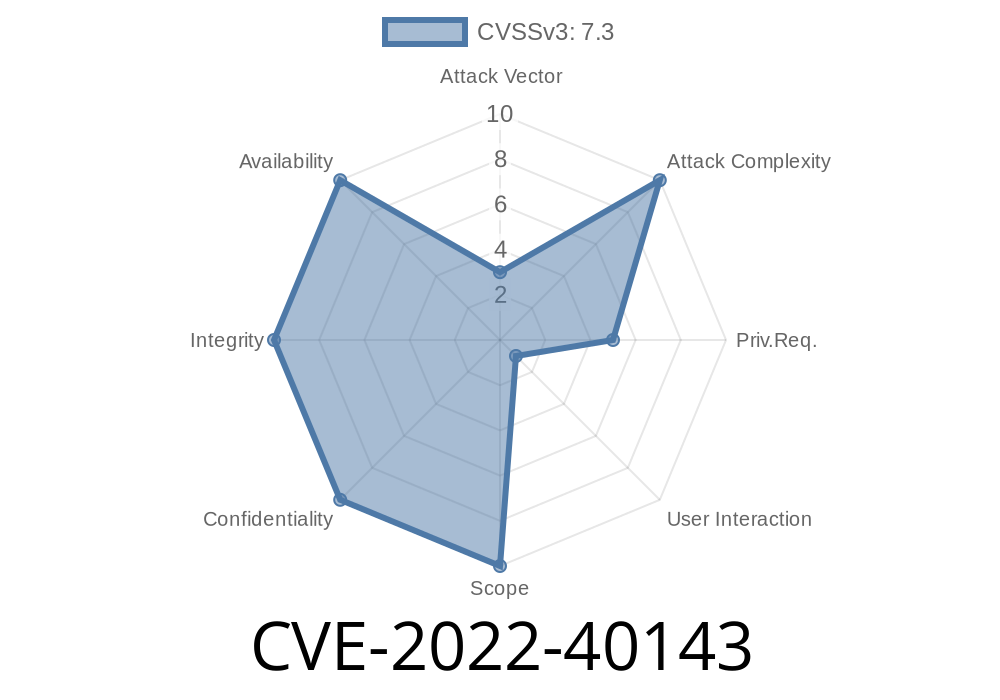
CVE-2022-40143 is a local privilege escalation vulnerability that affects Trend Micro products. An attacker would need to be in a position where they have access to the local system. This can be achieved by compromising another system on the same network, or by using remote access tools such as Team Viewer or VNC. Once a remote attacker has access to a vulnerable system, they could exploit the local privilege escalation vulnerability to run low-privileged code with elevated privileges. This could allow the attacker to install malicious software, view or change sensitive information, or even gain remote access to the target system. Note: Trend Micro products are designed to monitor the behaviour of the systems running these products, identifying suspicious activity and alerting administrators to take action. However, even if an attacker is not detected, this does not mean that the attack does not occur.
Vulnerability caused by a missing permission check
The vulnerability exists because the script fails to check whether the user has been granted access to the directory or file they are trying to access. If a local attacker had access to the system, they could use the vulnerability to elevate their privileges and run low-privileged code with elevated privileges.
Timeline
Published on: 09/19/2022 18:15:00 UTC
Last modified on: 09/21/2022 13:32:00 UTC