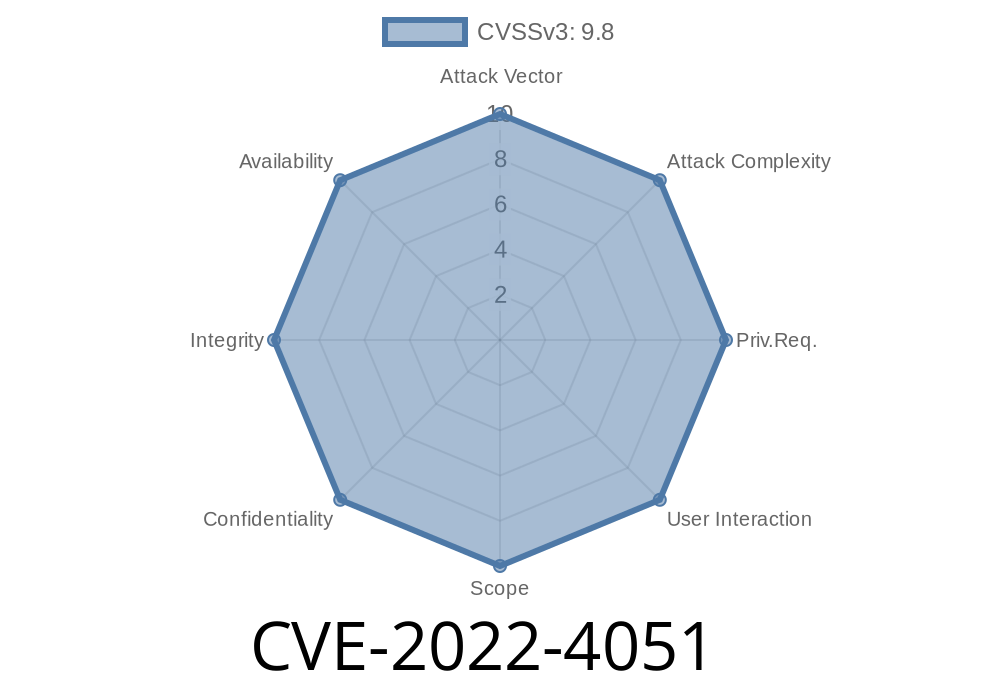
The attacker needs to be in contact with the victim in order to exploit this vulnerability. The victim does not have to visit a specific website or open a specific malicious file in order to be exploited. An attacker needs to be in contact with the victim in order to exploit this vulnerability. The victim does not have to visit a specific website or open a specific malicious file in order to be exploited. The exploit can be executed on website visitors by placing malicious files on web server and/or by installing malware on the user’s computer and then accessing a malicious website. The exploit can also be executed via email to the user who is likely to open the email. In most cases, the exploit could be found on the attacker’s server and is delivered by email. End users need to be aware of the risk of visiting untrusted websites and of emailing unknown people.
Vulnerability Details
The vulnerability is caused by unvalidated user input on the website, which is an SQL injection. The attacker can exploit the vulnerability by injecting their own query into the database, allowing them to execute arbitrary SQL commands. This could be used for many purposes such as executing a shell command that will allow the attacker to gain access and control of the system or even exfiltrate sensitive data from it.
Vulnerability Information and Description
The vulnerability can be exploited by attackers to gain remote access to the victim’s computer. The attacker needs to be in contact with the victim in order to exploit this vulnerability. This vulnerability is a cross-site scripting (XSS) vulnerability that affects Microsoft Internet Explorer and Microsoft Edge browsers.
The vulnerability is exploitable via XSS and leads to remote code execution on the victim’s machine.
A web server hosting malicious files or malware could also exploit this vulnerability by serving malicious code to a website visitor and/or an end user of a web browser who is likely to open an email containing the malicious code.
CWE-404: Improper Neutralization of Input During Web Page Development
This vulnerability can lead to a remote code execution (RCE) if exploited. This vulnerability could lead to the attacker gaining control of the victim’s computer, network or other device. The exploit is available on the attacker’s server and delivered by email or web download. End users need to be aware of the risk of visiting untrusted websites and of emailing unknown people.
Timeline
Published on: 11/17/2022 17:15:00 UTC
Last modified on: 11/21/2022 15:04:00 UTC