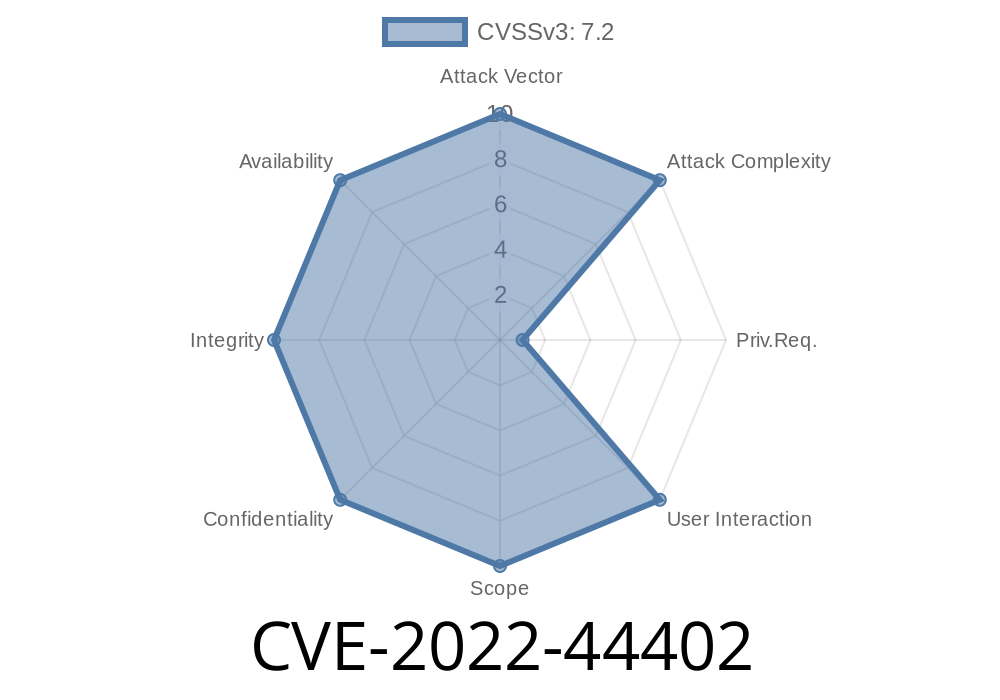
The injection occurs at the ‘f=’ parameter of Master.php. An attacker can inject an SQL query to delete, modify, or create any database record via a malicious request. A successful exploit of this vulnerability results in the attacker deleting or modifying any record of their choice.
In order to exploit this vulnerability, an attacker must send a request with a valid SQL query to Master.php. An example request with an SQL injection is shown below. The injected SQL query will be executed against the database and will affect the integrity of the system. -
INSERT INTO Master(‘f’) VALUES(‘/asms/classes/Master.php?f=delete_transaction()’); - The injection occurs at the ‘f=’ parameter of Master.php. An attacker can inject an SQL query to delete, modify, or create any database record via a malicious request. A successful exploit of this vulnerability results in the attacker deleting or modifying any record of their choice.In order to exploit this vulnerability, an attacker must send a request with a valid SQL query to Master.php. An example request with an SQL injection is shown below. The injected SQL query will be executed against the database and will affect the integrity of the system. - https://1vfh.com/asms/classes/Master.php?f=delete_transaction() -
Vulnerable code br anched from a known good line
Master.php is vulnerable to an SQL injection because it is possible for attackers to branch off of the control flow of a known good line. Master.php does not check for malicious input before executing the code, which can lead to attacks like this one.
The coding style in Master.php is also concerning as it does not follow best practices and has many vulnerabilities, such as this one.
SQL Injection and How It Could Affect Your Business
SQL Injection vulnerabilities are typically found in poorly coded PHP or web apps. This vulnerability is relevant if your site is accessible to the public via a URL that uses a SQL query, or if you have phpMyAdmin installed on your server. A successful exploit of this vulnerability will allow an attacker to run a variety of malicious actions against your website, including deleting records, adding new records and modifying existing ones. The attacker can also send spam, spam-like messages and take control of the website itself.
Vulnerability details
An attacker can inject an SQL query to delete, modify, or create any database record via a malicious request. A successful exploit of this vulnerability results in the attacker deleting or modifying any record of their choice.
SQL Injection Eavesdropper
The exploit is a SQL injection eavesdropper and will result in the attacker getting access to any table in the database.
Timeline
Published on: 11/17/2022 18:15:00 UTC
Last modified on: 11/18/2022 18:23:00 UTC