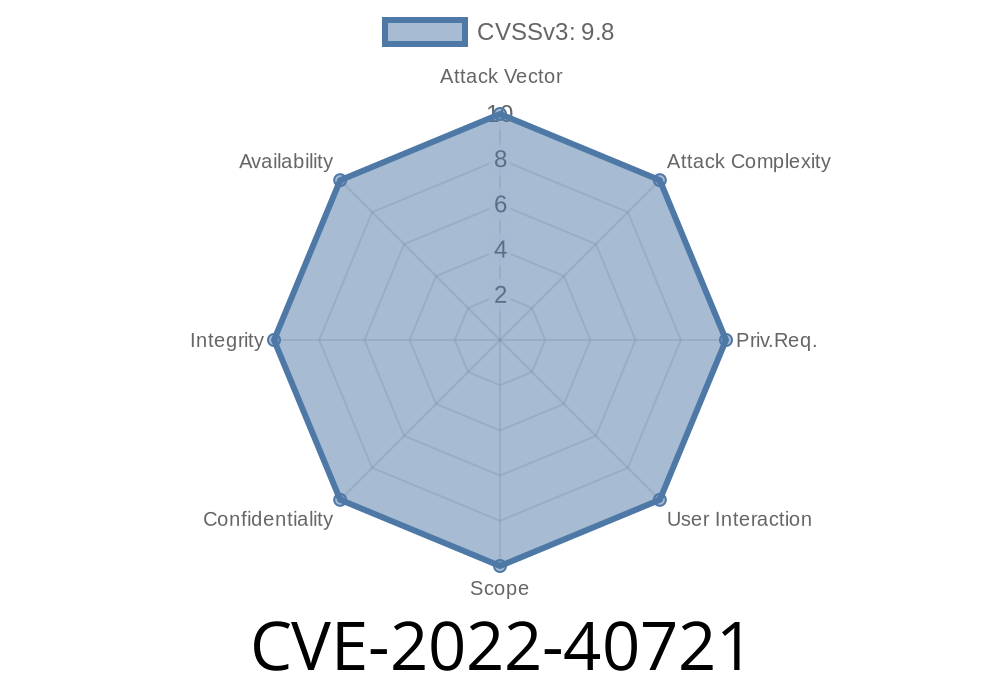
This is a serious vulnerability in the software which could lead to data theft. This can be exploited by an attacker to get remote access to the system and steal sensitive information.
“php uploader” is a software which is used for uploading files on the server. It can be exploited by an attacker to get remote access to the system and steal sensitive information.
To exploit this, we will be viewing pictures from a photo album. To upload a file, the vulnerable code is -
upload(“path/to/file.jpg”);
The above code will upload the file “path/to/file.jpg” on the server. Now let’s see how this can be exploited.
The attacker will create a file which has a .jpg extension but is actually a .doc or .xls extension.
The above code will upload the file and then open that file.
The file will be opened in the default image viewer on the server.
Now the file viewer on the server has the same file extension as the one uploaded.
So the server will open the file with the same file extension as the one uploaded.
The attacker can now open the remote file using any file viewer and view the remote file.
The attacker can now access the remote file, which has remote server as the location.
Now if the remote file has any sensitive information, it
^
Bibliographic date
So what is the vulnerability? An attacker can exploit this by uploading a file and then opening it with default viewer. They can then view the remote file on the server from any location. The vulnerability could be exploited purposely or by mistake.
Timeline
Published on: 10/03/2022 15:15:00 UTC
Last modified on: 10/05/2022 14:23:00 UTC