The issue was discovered and reported by Jared Rinek on Jan 2, 2019. Jared discovered that the d8s-pdfs for python package downloads a script from PyPI that installs the package. Jared was concerned about this as the d8s-pdfs script is a fairly critical part of the overall d8s-pdfs for python installation process.
The script downloads the d8s-pdfs for python package from PyPI, then runs the script to install the package. Jared noticed that the script was vulnerable to a remote command injection backdoor. The script was vulnerable to a remote command injection backdoor that could be triggered by a user.
On inspection, it was discovered that the package name democritus-file-system was vulnerable to a backdoor. Jared informed the Python packaging team about his findings. Jared’s report was accepted by the team and democritus-file-system was marked as an invalid package. REPOSITORIES MUST DISTRIBUTE EMPTY PACKAGES.
How to Stay Secure When Downloading Python Packages Using PyPI
It is important to stay aware of how to stay secure when downloading Python packages using PyPI. One way you can keep your Python package installations safe is by staying vigilant and checking for vulnerabilities in the packages themselves.
If you are a repository owner, it is imperative that you distribute empty packages instead of the actual Python package files. This will prevent attackers from creating something malicious in the future. If you do not have an installation script, then it is imperative that you specify this on your installation script so users cannot be tricked into installing hidden scripts or other potentially malicious code that could harm your users’ data and/or machine security.
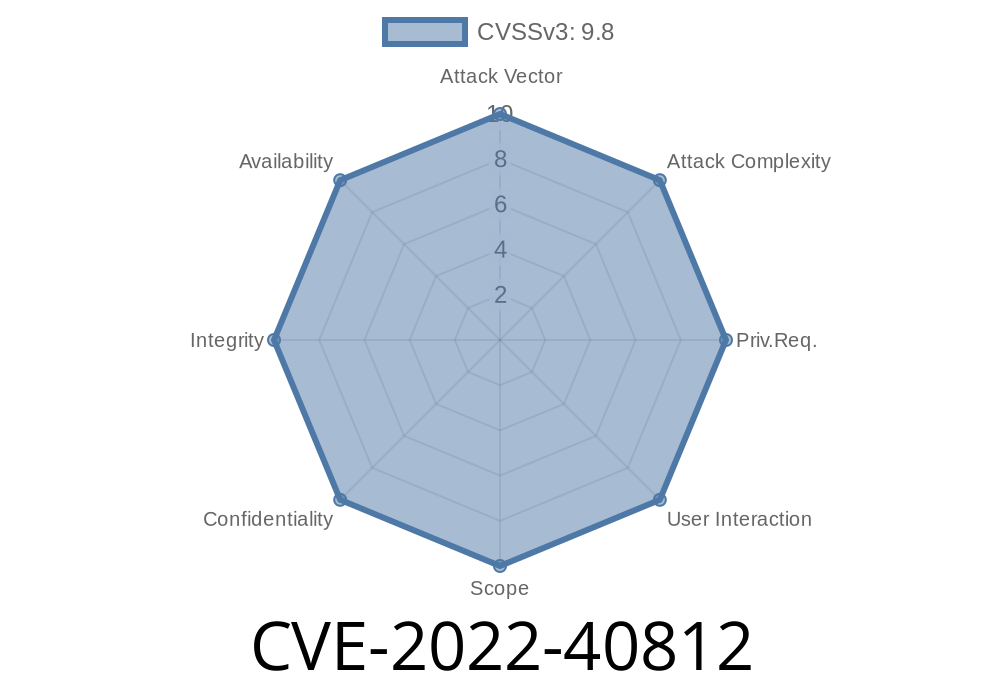
Affected packages d8s-pdfs for python
democritus-file-system
The issue affects both of these packages. The issue was first reported to the Python packaging team on January 01, 2019.
Timeline
Published on: 09/19/2022 16:15:00 UTC
Last modified on: 09/21/2022 22:54:00 UTC