This is a type of vulnerability that can be exploited by malicious users to gain elevated privileges on the system. This can be done by tricking the system into thinking that a specific printer is active, when it is not.
In order to exploit this vulnerability, a hacker needs to trick a victim into installing a printer on a system. This can be done in a variety of ways, such as sending an email that contains a malicious attachment, or convincing the victim to visit a malicious website. After the printer has been installed, the hacker can start to manipulate the printer to have it print a special file that contains the attacker’s code.
How does One-Click Printing work?
One-click printing is a feature that allows you to print documents without having to open the document first. These documents are then saved in the user’s local hard drive. This means that no data would be sent across the network, and malicious users wouldn’t be able to intercept and hijack these print jobs.
When using One-Click Printing, you should make sure that the device you’re setting up is capable of accepting connections from the printer server. The device should also be able to stop sending data when it receives a “stop request from printer server response” message from the computer. If your device doesn't meet these requirements, then your system won't be protected against one-click printing attacks.
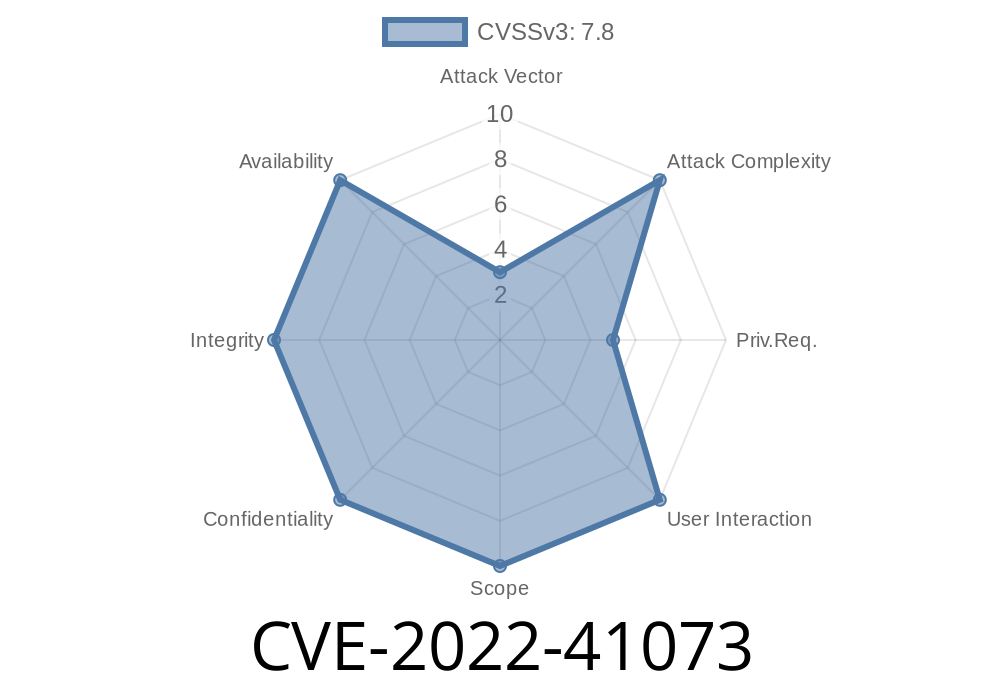
How to detect if your system is vulnerable to CVE-2022-41073?
To detect if your system is vulnerable to CVE-2022-41073, the following steps should be taken:
The printer's status should be checked. If the printer has been manually configured, it is possible that the malicious code was installed on the system and is still active. In this case, it would be necessary to manually delete the file from the printer's memory.
If a printer has not been manually set up but an administrator has added a new shared network printer in their client application, it may have been installed on their system.
If an update for Windows or Mac OS X has been recently downloaded, it is possible that a malicious installer file was inadvertently downloaded with it and is still active on their computer.
If you have access to your operating system's event logs, these can provide additional information about specific attempts made to exploit this vulnerability.
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/10/2022 00:33:00 UTC