It is a common scenario when memory is corrupted. This is a critical and dangerous situation that can lead to complete system crash and may result in data breach. One of the most common vectors for such attacks is the received email with a .dwg file attached. Such a file may be embedded with malicious code or infected with a virus. In such cases, it is very likely that the user will open the file and cause a system crash. Another vector for such attacks are malicious websites. It is very likely that a user will receive a link to an untrusted website. It is also likely that the user will open such a link and cause a system crash. Another common vector are malicious files sent as a malicious attachment to a user’s email. Such a file may be embedded with malicious code or infected with a virus. In such cases, it is very likely that the user will open the file and cause a system crash.
Vulnerability Scoring System
A vulnerability scoring system can help to determine the potential impact of a vulnerability. This will be done by assigning points to severity, exploitability, and usability. A scoring system is beneficial for both developers and other groups with an interest in security. Developers can use the scoring system to know what resources they should allocate for developing a solution to fix a particular problem. An external party, such as a security firm or government agency, also uses the scoring system to determine whether or not they should invest in mitigating the problem or if it is not worth their time and effort.
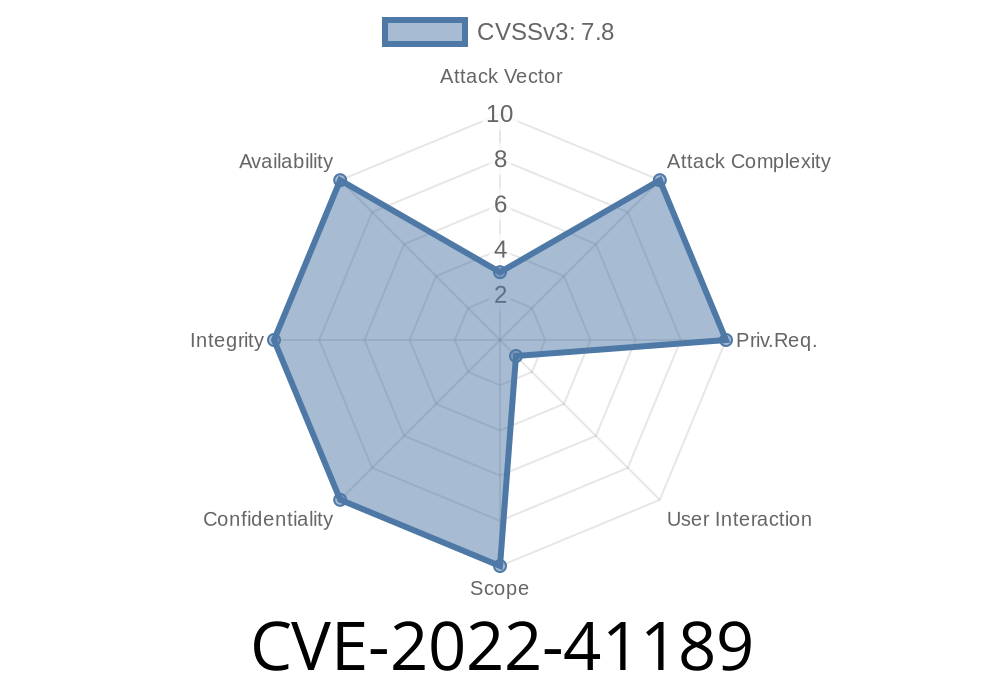
CVE-2022-41189 – Apple Final Cut Pro X Denial of Service
A vulnerability in Apple Final Cut Pro X could allow a remote attacker to crash the application, resulting in a denial of service. This vulnerability affects all versions of software prior to 10.3.2 and 10.4.0 on OSX Lion and OS X Mountain Lion systems running any version of Mac OS X. It is not known if this vulnerability also affects other versions of Mac software.
File types that can be used as a starting point for an attack
.dwg file: This file type is used for CAD drawings in AutoCAD and some other applications.
.docx, .docm, .ppt, .pptm, .xlsx: These are files that are used to create Microsoft Office documents (WordPad, Excel)
.jpg, .jpeg: These are image files that may contain malicious code or infected with a virus
.pdf: This is a document that can be viewed using Acrobat Reader
Vulnerability details CVE-2022-41189
A vulnerability was found in the way that certain applications handle .dwg files. This vulnerability allows an attacker to cause a system crash by sending a specially crafted file to a victim's computer without their knowledge.
The vulnerability exists due to the way that applications process .dwg files. An attacker can send a malicious .dwg file to trigger this vulnerability.
The vulnerability affects all versions of Microsoft Office and may affect other products.
Vulnerability Assessment Overview
Vulnerability assessment involves scanning the system for security vulnerabilities. The goal of such a scan is to find any vulnerabilities that may cause system crashes. Once found, the vulnerabilities can be fixed. Vulnerability assessment is important because it helps in identifying and fixing vulnerabilities before they lead to a system crash.
The following are some suggestions that can help your business avoid these common mistakes:
1) Avoid using generic messages in your ads:
- Trying to use advertising that's too generic will not generate interest and may result in low conversions. Generic language like "Buy now" or "Don't miss this opportunity" won't inspire user engagement and will likely result in low click-through rates.
- Custom messages with useful information about your company or product will get people to click through instead of just scrolling past them without much thought. This information can also help you craft an ad campaign that's more targeted to what you're trying to achieve with your ad campaign.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:20:00 UTC