The XSS flaw can be exploited by remote attackers via a request to the component /apiadmin/notice/add. An attacker can inject script codes in the form’s field to attack the user via a XSS issue. After successful XSS injection, an attacker can steal the user’s credentials and have the system’s administrator to perform any operation they wish. Note that the vendor hardening the component against XSS. However, the flaw is still possible due to lack of input validation and lack of code optimization.
Another critical vulnerability found in CMS-E v3.12.0 is a remote code execution vulnerability via a specially crafted request that can be exploited by an attacker. An attacker can send a vulnerable request to the component /apiadmin/notice/add and can exploit the code injection to execute arbitrary code on the targeted host. The vendor patched this vulnerability in v3.12.1.
CMS-E v3.12.1 - Fixed vulnerabilities
The vendor released a new version of CMS-E v3.12.1 which fixed several important vulnerabilities in the application, including XSS and RCE vulnerability. In particular, the following bugs were fixed:
- CVE-2018-12359 - XSS vulnerability via a specially crafted request
- CVE-2019-2898 - Remote code execution vulnerability via a specially crafted request
CMS-E v3.12.0 – HTTP Response Splitting and Content-Length
The vulnerability in CMS-E v3.12.0 is a remote code execution vulnerability that can be exploited by an attacker via a specially crafted request that breaks the HTTP response splitting and content-length validation.
Note that the vendor patched this vulnerability in v3.12.1.
Disqus CMS v3.12.0 – HTTP Response Splitting Remote Code Execution Vulnerability
This vulnerability can be exploited by remote attackers via a specially crafted request to the component /cms-e/apiadmin/notice/add. An attacker can send a vulnerable request with a large amount of data and can exploit the code injection to execute arbitrary code on the targeted host. The vendor patched this vulnerability in v3.12.1.
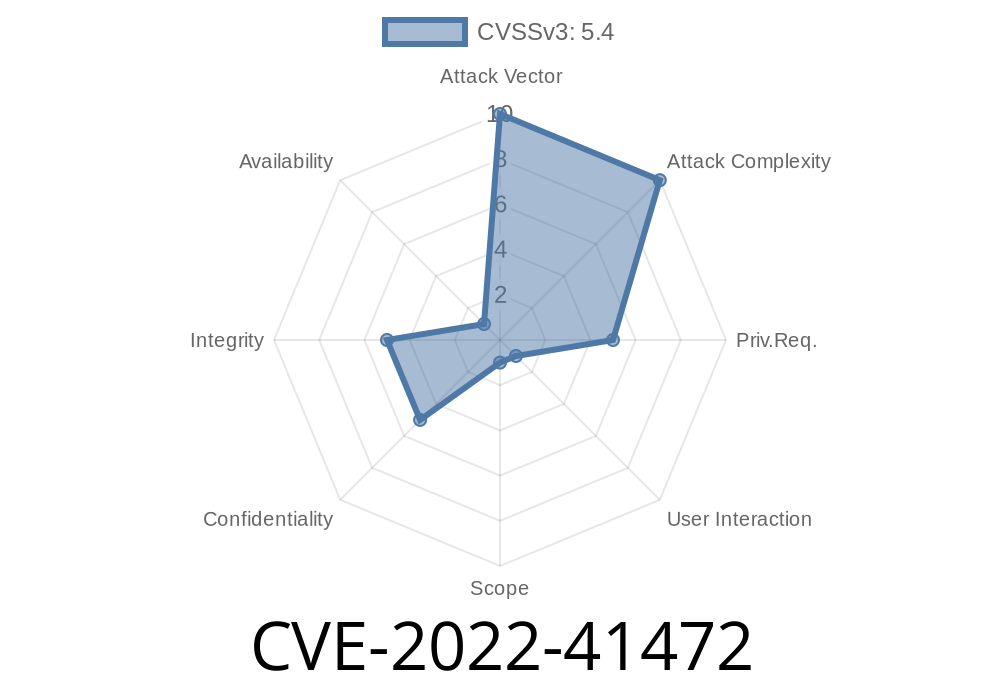
CVE-2022-41477
The XSS flaw can be exploited by remote attackers via a request to the component /apiadmin/notice/add. An attacker can inject script codes in the form’s field to attack the user via a XSS issue. After successful XSS injection, an attacker can steal the user’s credentials and have the system’s administrator to perform any operation they wish. Note that the vendor hardening the component against XSS. However, the flaw is still possible due to lack of input validation and lack of code optimization.
Another critical vulnerability found in CMS-E v3.12.0 is a remote code execution vulnerability via a specially crafted request that can be exploited by an attacker. An attacker can send a vulnerable request to the component /apiadmin/notice/add and can exploit the code injection to execute arbitrary code on the targeted host. The vendor patched this vulnerability in v3.12.1.
Timeline
Published on: 10/17/2022 14:15:00 UTC
Last modified on: 10/29/2022 02:57:00 UTC