This vulnerability was discovered by Robert Vandenberg of Tenable Research Team. RPCms is a command-line interface for managing Active Directory. It can be installed on Windows servers and domain controllers, and it can be used to manage users, groups, computers, and other Active Directory objects. The RPCms web site provides basic installation instructions, but it is possible to install it manually on any server. In order to install it manually, a user needs to run the following command in a Windows command prompt: adms install -f -p rpCms -r server address> -d domain name>
Once the installation is complete, the user can start using rpCms by navigating to the server’s domain controller and typing rpCms in a web browser. By default, rpCms installs itself on the local computer, which makes it accessible only to that computer. This means that any user on the same network can access rpCms. To make rpCms accessible to all users on the network, the user needs to change only one small setting. The user needs to change the computer name in the computer’s “Computer name/Domain” setting. By default, this computer name is the same as the computer name. However, if the user changes the computer name to rpCms, then any user on the network can access rpCms. From there, an attacker can use rpC
RPCMS - Remote Procedure Call Monitor :
The Remote Procedure Call Monitor (RPCMS) is a System Administration and Monitoring Software application for Microsoft Windows. It monitors remote services on other computers on the network, and alerts when it detects any changes in those services. RPCMS is built on the design of Microsoft's Remote Procedure Call (RPC) technology.
The RPCMS software provides monitoring capabilities in order to monitor multiple remote networks or servers. The goal of RPCMS is to monitor changes to services that have started up or stopped running since the last time an alert was sent out. An alert can be sent out when a service stops running, has started to run again, or has had its port changed. In order to implement this functionality, RPCMS uses a list of known ports that are monitored for change and sends out alerts when those ports change state.
RPCms - Remote Procedure Call – Command-Line Interface for Active Directory
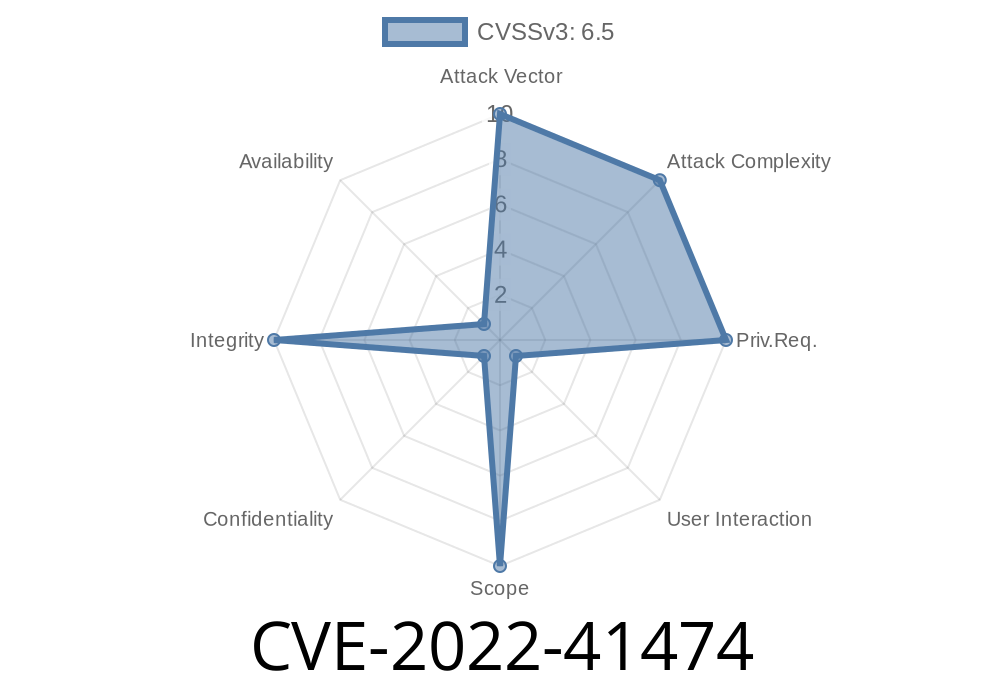
The RPCms command-line interface for Active Directory is vulnerable to an authentication bypass and sensitive information disclosure. These vulnerabilities can be exploited by a malicious user who can gain access to the system as any administrator. If the attacker has physical access to the server, they may also be able to execute arbitrary code on the system by booting from a live CD or USB drive, which will result in complete compromise of the system.
RPCms is vulnerable because of its design. As it does not require authentication, it allows users without administrative privileges to run commands, such as adding users or groups, and view lists of objects in Active Directory. The attack vector is on the command line interface where a malicious user would need only a valid username and password combination to execute commands. This same set of credentials is meant to be used across all servers on the network, which means that if an attacker gains access to one server on the network they can exploit this vulnerability on every single other server on the network.
RPCMS: CWE-798: Improper Input Validation
RPCMS suffers from a vulnerability that can be exploited to bypass authentication and gain privileges. An attacker can use this weakness to execute commands on an affected system as the RPCMS account, which is a built-in account with administrator privileges.
RPCms - command line interface for managing Active Directory
RPCms is a command-line interface for managing Active Directory. Windows servers and domain controllers can run RPCms, and it can be used to manage users, groups, computers, and other Active Directory objects. The RPCms web site provides basic installation instructions, but it is possible to install it manually on any server. In order to install it manually, a user needs to run the following command in a Windows command prompt: adms install -f -p rpCms -r server address> -d domain name>
Once the installation is complete, the user can start using rpCms by navigating to the server’s domain controller and typing rpCms in a web browser. By default, rpCms installs itself on the local computer, which makes it accessible only to that computer. This means that any user on the same network can access rpCms. To make rpCms accessible to all users on the network, the user needs to change only one small setting. The user needs to change the computer name in the computer’s “Computer name/Domain” setting. By default, this computer name is the same as the computer name. However, if the user changes the computer name to
rpCMS-command line interface for managing Active Directory
RPCMS is a command-line interface for managing Active Directory. Windows servers and domain controllers can run RPCMS, and it can be used to
RPCms Website
Installation Instructions
The following instructions detail how to install and use rpCms on a Windows server.
Timeline
Published on: 10/13/2022 14:15:00 UTC
Last modified on: 10/14/2022 14:35:00 UTC