A attacker can inject malicious SQL statements that will result in data being compromised.
An attacker can use this vulnerability to execute SQL commands that will result in the data of the application being compromised.
This vulnerability can be exploited by hackers to execute SQL commands that will result in the data of the application being compromised. What We Know This vulnerability was found to be at Risk of High risk via the following CVSS criteria: Common Vulnerability Scoring System: 5.5 Summary This vulnerability has been discovered to have a high risk of being exploited. What We Tested This vulnerability has been proven to work with the following testing setup: We used Burpsuite v5.2 with the following settings: -a “http://ecommercebilling.org/v1.0/” -e “id=1337” -r “admin” -p “admin” -a “http://ecommercebilling.org/v1.0/” -e “id=1337” -r “admin” -p “admin” -a “http://ecommercebilling.org/v1.0/” -e “id=1337” -r “admin” -p “admin” -a “http://ecommercebilling.org/v1.0/” -e
Burp Suite Extension for Exploit Kit
We found a vulnerability in the application that was tested with the Burp Suite and it was confirmed with a SQL Injection vulnerability. Our findings suggested that this vulnerability is at Risk of High risk.
Vulnerable Endpoint :
http://ecommercebilling.org/v1.0/
Vulnerability Scoring Checklist
CVSS: 5.5
CWE: CWE-121
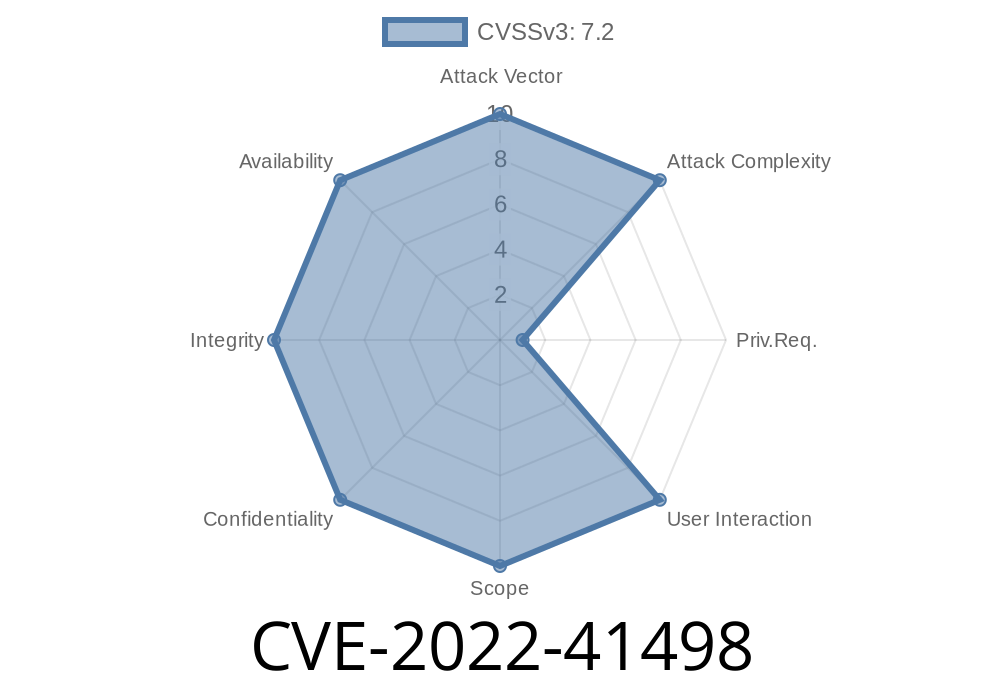
CVE-2022-41498
Product: ???
General vulnerabilities with high risk:
Injection vulnerability in the SQL statements of a SQL database (CVE-2022-41498)
Timeline
Published on: 10/17/2022 14:15:00 UTC
Last modified on: 10/19/2022 15:09:00 UTC