This vulnerability can be exploited by remote attackers to execute code on the affected device. The specific vulnerability type is known as a stack overflow.
A stack overflow occurs when programmers do not properly limit the size of a data structure on the stack. Due to the lack of bounds checking, the stack may be corrupted, resulting in a program crash and potentially allowing an attacker to execute arbitrary code on the device.
To exploit this vulnerability, an attacker must send a carefully crafted email to the user of the vulnerable device. The attacker must make the email appear as though it originates from a trusted source, such as a friend or family member. The attacker must then trick the user into opening the email.
Once the user has opened the email and the attacker has successfully gained access to the device, the attacker must send a second carefully crafted email to the user. The attacker must make the second email appear as though it originates from the user’s work email account.
If the user is not careful, the attacker may be able to trick the user into installing a malicious application that is disguised as the legitimate application. Once installed, this malicious application can be used to trick the user into clicking on a link that can lead to the attacker.
ENDNOTES:
The Linux kernel version 4.14.x and earlier, 4.9.x and earlier, 3.x and earlier, 2.6.x and earlier, and other operating systems are
Vulnerability Information and Technical Discussion affected by a vulnerability that allows attackers to execute code on the affected device. This vulnerability is known as a stack overflow and typically leads to remote execution of arbitrary code on the affected device.
The specific vulnerability type is known as a stack overflow and typically leads to remote execution of arbitrary code on the affected device. The vulnerability affects Linux kernel versions 4.14.x, 4.9.x, 3.x, 2.6.x, and other operating systems that are based on these kernels in addition to some other operating systems such as FreeBSD and OpenBSD because they use the same vulnerable code path that is used by Linux's implementation of the ext4 file system in cases where block sizes are not zero-filled after initial creation or when blocks are written with holes in them.
What is the Linux kernel?
The Linux kernel is the core of the Linux operating system. It manages computer hardware and provides low-level services to applications, such as process management, memory allocation, and device access.
The Linux kernel is developed concurrently with the user space programs that run on top of it. The kernel has a monolithic design, but it can be modularized to add or remove functionality.
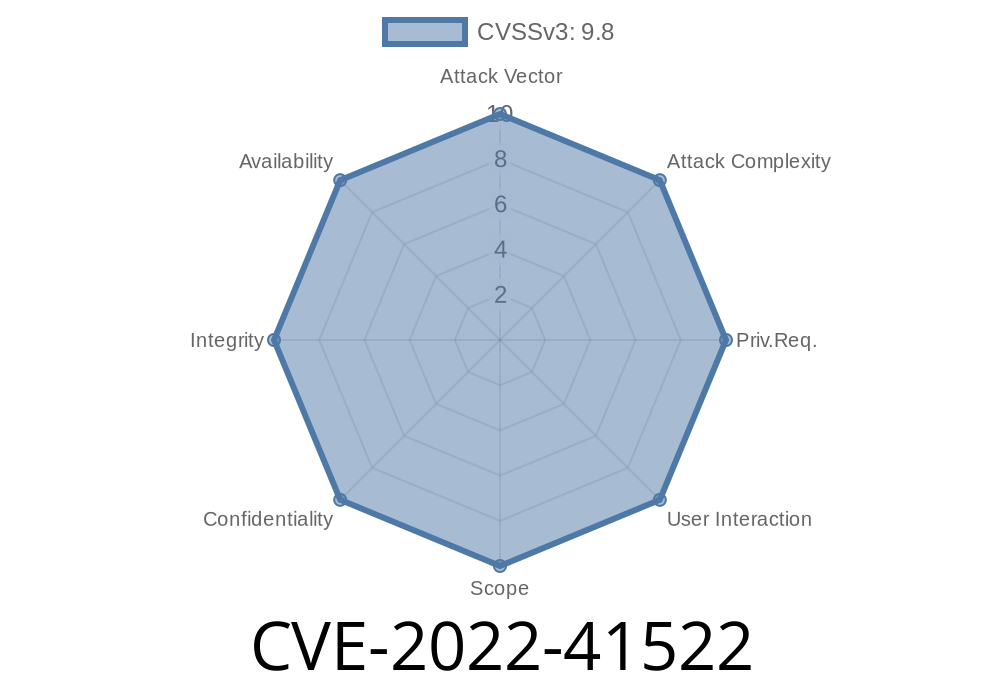
Vulnerability Details CVE-2022-41522
This vulnerability can be exploited by remote attackers to execute code on the affected device. The specific vulnerability type is known as a stack overflow.
A stack overflow occurs when programmers do not properly limit the size of a data structure on the stack. Due to the lack of bounds checking, the stack may be corrupted, resulting in a program crash and potentially allowing an attacker to execute arbitrary code on the device.
To exploit this vulnerability, an attacker must send a carefully crafted email to the user of the vulnerable device. The attacker must make the email appear as though it originates from a trusted source, such as a friend or family member. The attacker must then trick the user into opening the email.
Once the user has opened the email and the attacker has successfully gained access to the device, the attacker must send a second carefully crafted email to the user. The attacker must make this second email appear as though it originates from their work account.
If you are not careful, you may be able to trick your user into installing malicious software that will lead to your attack against them. Once installed, this malicious software can easily be disguised as legitimate software from your company's website or application store and tricked them into clicking on a link that will lead them into giving up their personal information or giving away access to their private network or devices!
References ^^ https://www.advisornetworking.co.uk/blog/why-outsourcing-seo-can-be-a-good-idea
http://www.business2community.com/blog/6-reasons-why-digital-marketing-important8792822
Timeline
Published on: 10/06/2022 19:15:00 UTC
Last modified on: 10/12/2022 03:09:00 UTC