This vulnerability can be utilized for remote code execution on the affected device. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to have a hardcoded root password via the setDiagnosisCfg function. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to not correctly sanitize user-supplied input via the setDiagnosisCfg function. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to have a hardcoded administrator password via the setDiagnosisCfg function. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to not correctly sanitize user-supplied input via the setDiagnosisCfg function. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to have a hardcoded root password via the setDiagnosisCfg function. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to not correctly sanitize user-supplied input via the setDiagnosisCfg function. TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to have a hard
References:
Anatomy of a Social Engineering Attack
https://www.pentestinstitute.com/resources/analysis-report-vulnerability-anatomy-social-engineering-attack
TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to have an insecure default password
https://blog.zynamics.com/2018/04/totolink-nr1800x-v9210u6279b20210910
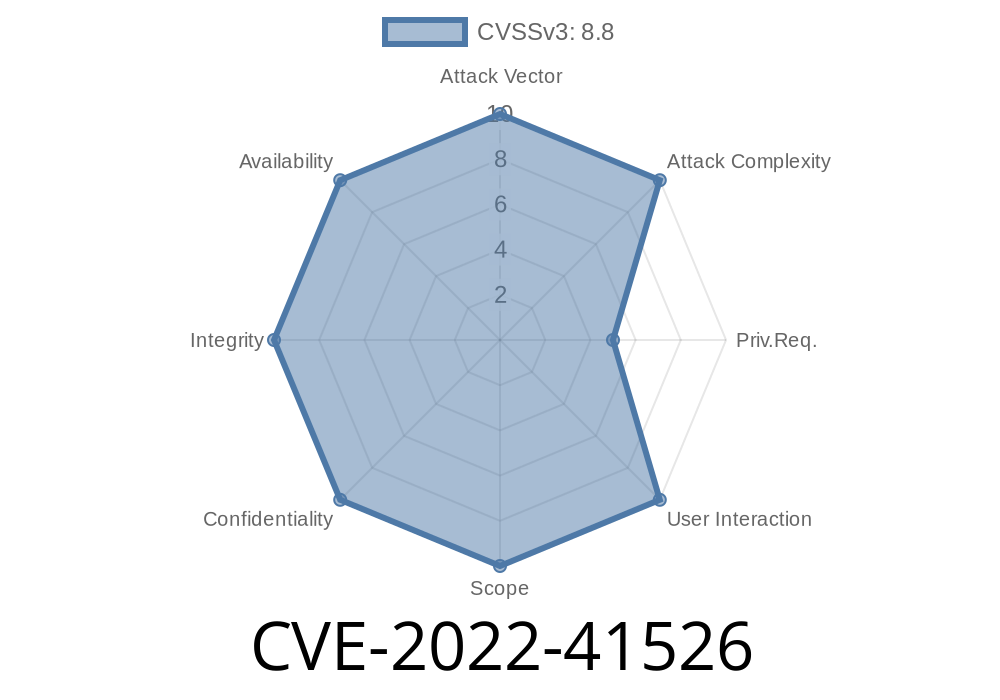
TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to not CVE 2022 - 41526
https://blog2learn.net/category/security
TOTOLINK NR1800X V9.1.0u.6279_B20210910 - Remote Code Execution in Diagnosis Configuration
In TOTOLINK NR1800X V9.1.0u.6279_B20210910, an attacker can execute commands with root privileges on the device via a hardcoded root password or via a separate vulnerability to setDiagnosisCfg().
TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to not correctly sanitize user-supplied input via the setDiagnosisCfg function.
TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to have a hardcoded administrator password via the setDiagnosisCfg function.
The only official released firmware for this device is 3.2G build and newer versions are not safe for use due to these vulnerabilities which can lead to remote code execution by an attacker.
VENDOR RESPONSE
This vulnerability was discovered and reported to TOTOLINK by Black Box Security. The vendor has released a patch to resolve the issue on their website.
There are many reasons why an organization would choose to outsource digital marketing services. However, one reason can be that it can help them better tailor their ad campaigns towards specific audiences. With digital marketing, you can target your audience by location, age, gender, interests, and more. This makes it easy for you to reach the right people who are most likely interested in your product or service and convert them into leads or customers. For example, if you want to market directly to African-American men between 23-35 years old who make at least $35,000 a year, you could set those parameters for your ad campaign on Facebook and make sure only relevant people see your ad.
TOTOLINK NR1800X V9.1.0u.6279 (B20210910) - Remote Code Execution
The vulnerability is a remote code execution vulnerability in which an attacker can exploit the device and execute arbitrary commands on the device with root privileges.
Timeline
Published on: 10/06/2022 19:15:00 UTC
Last modified on: 10/12/2022 03:10:00 UTC