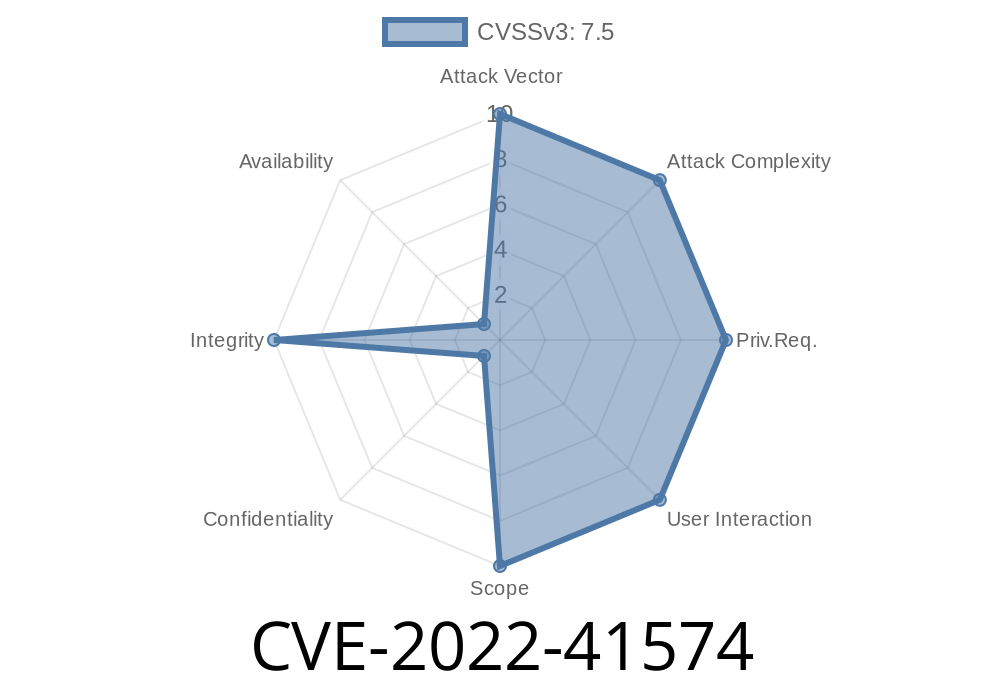
The affected code is located in the configuration of the Gradle Enterprise installation process, and is used to allow remote administrators to perform backups of the system. However, the vulnerability allows attackers to perform remote backups, and sign them with a bogus installation-administrator password, which can be sent to the configured installation-administrator email address. This allows attackers to potentially remove critical data from the cloud server, and make it unavailable to other users. The installation-administrator password is stored in a configuration file, which is readable only by root. As a result, only attackers with root privileges on the system can exploit this vulnerability. This issue affects all versions of Gradle Enterprise, including the latest version, which is 2022.3.2. Affected versions include 2022.4 through 2022.3.1. The advised workaround is to immediately upgrade to the latest version of Gradle Enterprise, which resolves this issue.
Vulnerability overview
A vulnerability in the Gradle Enterprise installation process allows attackers to perform remote backups and sign them with a bogus installation-administrator password. This can potentially remove critical data from the cloud server and make it unavailable to other users. The installation-administrator password is stored in a configuration file which is readable only by root. As a result, only attackers with root privileges on the system can exploit this vulnerability. The advised workaround is to upgrade to the latest version of Gradle Enterprise, which resolves this issue.
This CVE ID was found at: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-41574
Summary
The Gradle Enterprise installation process allows remote administrators to perform backups of the system, which can be sent to an email address on file. This issue affects all versions of Gradle Enterprise, including the latest version, which is 2022.3.2. The advised workaround is to immediately upgrade to the latest version of Gradle Enterprise, which resolves this issue.
Timeline
Published on: 10/07/2022 21:15:00 UTC
Last modified on: 10/11/2022 15:21:00 UTC