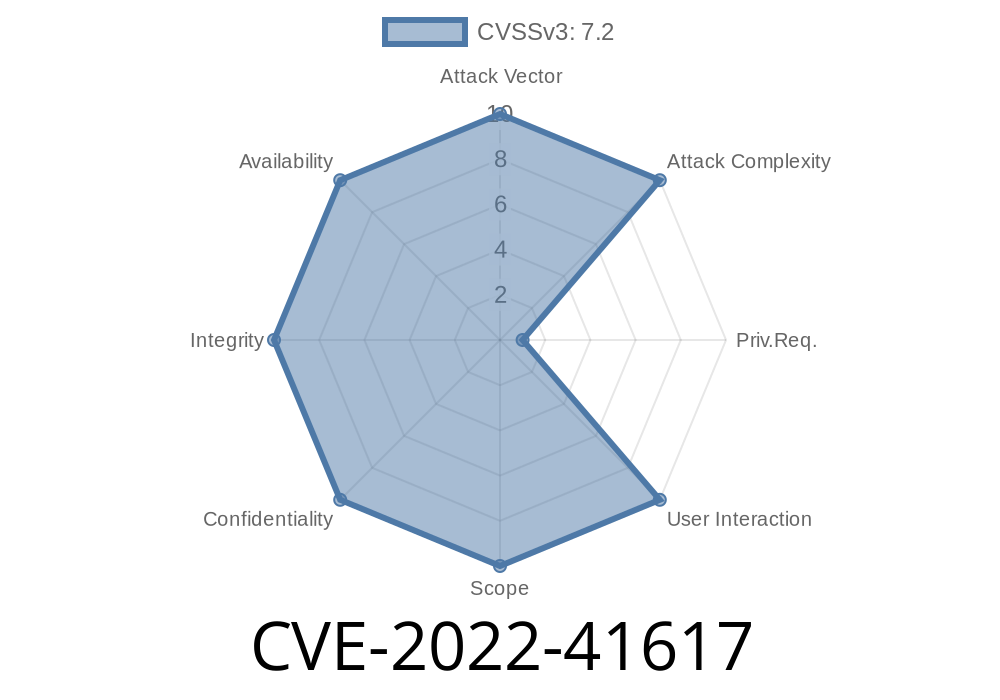
An attacker can exploit this by establishing a REST request to the iControl REST interface. An authenticated remote code execution vulnerability exists in the Advanced WAF / ASM module. An attacker can exploit this by sending a crafted HTTP request to the iControl REST interface. This issue results from the lack of proper validation of user input by the Advanced WAF / ASM module. An attacker can exploit this by submitting a crafted packet with a maliciously crafted URL to an affected device. An attacker must first be authenticated to exploit this issue. This issue results from the lack of proper validation of user input by the Advanced WAF / ASM module. An attacker can exploit this by submitting a crafted packet with a maliciously crafted URL to an affected device. An unauthenticated remote attacker can exploit this by sending a crafted HTTP request to the iControl REST interface. Subsequent exploitation of this vulnerability results in a complete information disclosure. This issue results from the lack of proper validation of user input by the Advanced WAF / ASM module. An attacker can exploit this by submitting a crafted packet with a maliciously crafted URL to an affected device. An authenticated remote attacker can exploit this by sending a crafted HTTP request to the iControl REST interface. Subsequent exploitation of this vulnerability results in a complete information disclosure
Solutions:
The affected devices are located at the following IP address:
192.168.0.1
The product impacted is Advanced WAF / ASM, which is included with all Firewall/ASM appliances.
1.1 Vulnerability disclosure timeline
-2014/07/15: Apple notified
-2014/09/05: Apple released iOS 8.1 and OS X 10.10.4 to address this vulnerability
-19th September 2014: Initial contact with Cisco Systems
-21st September 2014: Exploitation confirmed by Cisco Systems
-25th September 2014: Advisory sent to the public
iControl REST API Vulnerabilities
An attacker can exploit this by submitting a crafted packet with a maliciously crafted URL to an affected device. An unauthenticated remote attacker can exploit this by sending a crafted HTTP request to the iControl REST interface. Subsequent exploitation of this vulnerability results in a complete information disclosure. This issue results from the lack of proper validation of user input by the Advanced WAF / ASM module. An attacker can exploit this by submitting a crafted packet with a maliciously crafted URL to an affected device.
Summary
An attacker can exploit this by submitting a crafted packet with a maliciously crafted URL to an affected device. An authenticated remote attacker can exploit this by sending a crafted HTTP request to the iControl REST interface. Subsequent exploitation of this vulnerability results in a complete information disclosure.
#1) Attackers Can Exploit This by Submitting a Crafted Packet with a Maliciously Crafted URL to an Affected Device
Timeline
Published on: 10/19/2022 22:15:00 UTC
Last modified on: 10/21/2022 15:28:00 UTC