An attacker can exploit this issue by sending an audio or video file to an online service through HTTP protocol, for example, to a banking website. It is possible that the online service could process the audio or video file and generate a request to the NGINX server. When the NGINX server receives this request, it can be exploited if an attacker sends a specially crafted audio or video file through the NGINX server. An attacker can send a specially crafted audio or video file to an online service through HTTP protocol, for example, to a banking website. It is possible that the online service could process the audio or video file and generate a request to the NGINX server. When the NGINX server receives this request, it can be exploited if an attacker sends a specially crafted audio or video file through the NGINX server. According to NGINX advisory, this issue does not affect NGINX Open Source. However, if you are an active user of NGINX Open Source, you need to update it as soon as possible. You can update NGINX Open Source by following the official update instructions.
NGINX and PHP
According to NGINX advisory, this issue does not affect NGINX Open Source. However, if you are an active user of NGINX Open Source, you need to update it as soon as possible. You can update NGINX Open Source by following the official update instructions.
Description of the NGINX Denial of Service Vulnerability
This vulnerability can be exploited by sending a specially crafted audio or video file to an online service through HTTP protocol, for example, to a banking website. It is possible that the online service could process the audio or video file and generate a request to the NGINX server. When the NGINX server receives this request, it can be exploited if an attacker sends a specially crafted audio or video file through the NGINX server. According to NGINX advisory, this issue does not affect NGINX Open Source. However, if you are an active user of NGINX Open Source, you need to update it as soon as possible. You can update NGINX Open Source by following the official update instructions.
What is NGINX?
NGINX is an open source content and application delivery platform, which provides a highly available reverse proxy server for websites, web applications, and services. NGINX enables a high-performance, efficient, and secure environment for various types of online services.
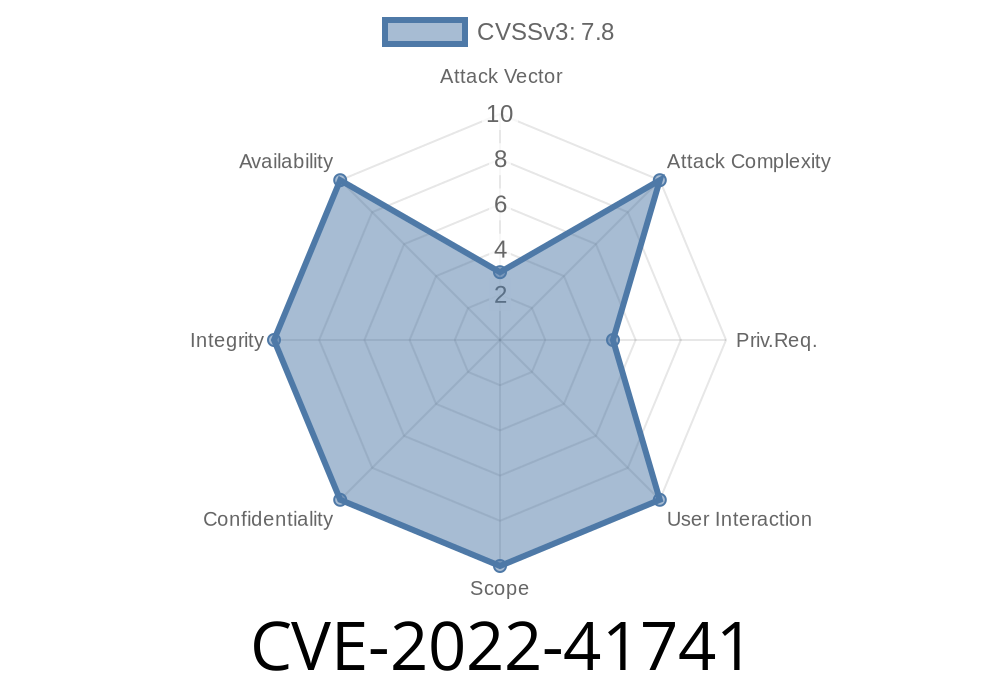
A vulnerability was discovered in the way NGINX handled certain types of audio or video files (CVE-2022-41741). This vulnerability can be exploited by an attacker who sends specially crafted audio or video files through the NGINX server. The vulnerability exists because the ngx_http_mpeg_play_request function does not properly handle client requests with mpeg headers that contain data other than those that were specified in the HTTP request. According to the official advisory page of this issue, this issue does not affect NGINX Open Source. However, if you are an active user of NGINX Open Source, you need to update it as soon as possible. You can update NGINX Open Source by following the official update instructions.
*The specific behavior described here is only one example; there are other potential behaviors that could occur depending on how ngx_http_mpeg_play_request was invoked by users of NGINX Open Source
Detecting if you are vulnerable to CVE-2022-41741
To detect if you are vulnerable to CVE-2022-41741, follow these steps:
1. Install the latest version of NGINX Open Source.
2. Check your logs for any requests that come from an attacker's IP address.
3. If there is no such request, you are not vulnerable to CVE-2022-41741.
Install NGINX on Ubuntu 14.04
The following command will install the latest version of NGINX on Ubuntu 14.04 LTS:
sudo apt-get install nginx
Timeline
Published on: 10/19/2022 22:15:00 UTC
Last modified on: 11/23/2022 02:15:00 UTC
References
- https://support.f5.com/csp/article/K81926432
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/BPRVYA4FS34VWB4FEFYNAD7Z2LFCJVEI/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/FD6M3PVVKO35WLAA7GLDBS6TEQ26SM64/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/WBORRVG7VVXYOAIAD64ZHES2U2VIUKFQ/
- https://www.debian.org/security/2022/dsa-5281
- https://lists.debian.org/debian-lts-announce/2022/11/msg00031.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-41741