This issue does not affect Red Hat Enterprise Linux 6. Red Hat recommends upgrading D-Bus to version 1.15.3 or later. A bug was discovered in D-Bus before 1.12.24, 1.13.x and 1.14.x before 1.14.4, and 1.15.x before 1.15.2. A maliciously crafted D-Bus message can cause dbus-daemon and other programs that use libdbus to crash when receiving a message where an array length is inconsistent with the size of the element type. This issue does not affect Red Hat Enterprise Linux 6. Red Hat recommends upgrading D-Bus to version 1.15.3 or later. An issue was discovered in D-Bus before 1.12.24, 1.13.x and 1.14.x before 1.14.4, and 1.15.x before 1.15.2. An attacker can cause dbus-daemon and other programs that use libdbus to crash when receiving a message where an invalid pointer is passed to a function that expects a buffer. This issue does not affect Red Hat Enterprise Linux 6. Red Hat recommends upgrading D-Bus to version 1.15.3 or later. Red Hat Enterprise Linux 6 does not support the sddm display manager. It is recommended to upgrade d-feet to version 3.10 or later to avoid potential issues. An issue was discovered in D-Bus before
References:
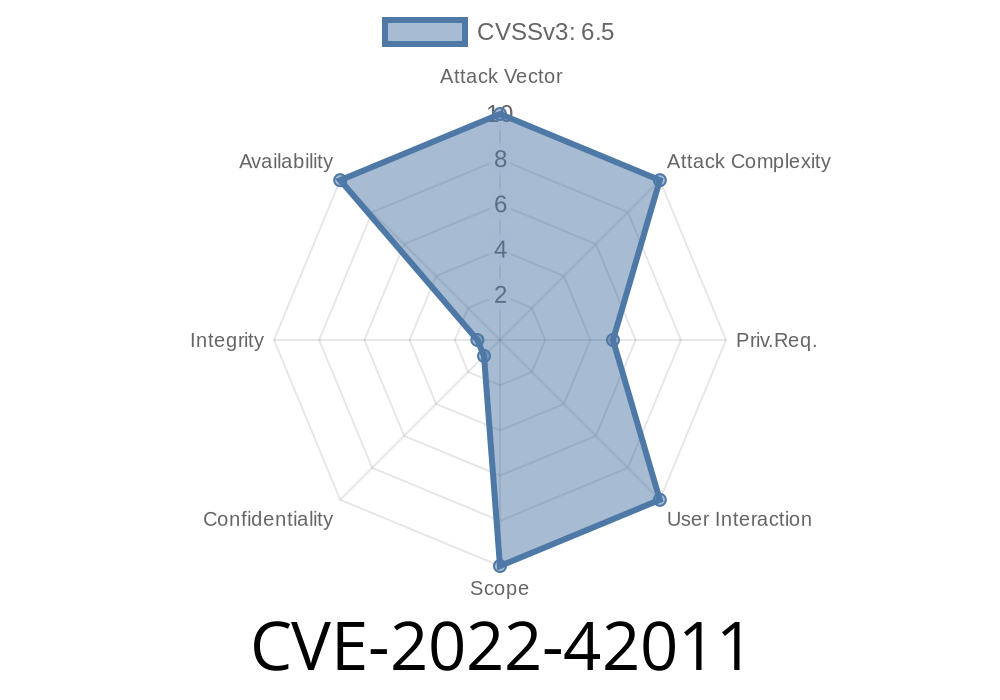
- CVE-2022-42011
- D-Bus 1.10, 1.11, 1.12, 1.13, 1.14 and 1.15 security advisories
- D-feet 3.10 security advisory
D-Bus before 1.12.24 and 1.13.x and 1.14.x before 1:
14.4, and 1.15.x before 1.15.2
An issue was discovered in D-Bus before 1.12.24, 1.13.x and 1.14.x before 1:14.4, and 1.15.x before 1.15.2 that allows a malicious server to cause dbus-daemon and other programs that use libdbus to crash when sending a message with invalid data to the client where dbus_log_message() is called later in the message handler than it is registered with the bus system bus_type object which may allow remote attackers to cause a denial of service (application crash).
Timeline
Published on: 10/10/2022 00:15:00 UTC
Last modified on: 11/14/2022 15:16:00 UTC
References
- https://www.openwall.com/lists/oss-security/2022/10/06/1
- https://gitlab.freedesktop.org/dbus/dbus/-/issues/413
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/SQCSLMCK2XGX23R2DKW2MSAICQAK6MT2/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/E4CO7N226I3X5FNBR2MACCH6TS764VJP/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ND74SKN56BCYL3QLEAAB6E64UUBRA5UG/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-42011