D-Bus packages that are enabled by default on Ubuntu Trusty and later distributions were vulnerable before D-Bus 1.16 was released. An attacker could exploit this to crash the D-Bus daemon, which could lead to arbitrary code execution.
Impacted systems: Ubuntu Trusty USN-3076-1 - D-Bus vulnerability - Link
CVE ID: None issued - Details: This issue was discovered by Juan Pablo Ramirez Munoz of the Red Hat team.
9.1. How to address the issues?
To resolve the issue, upgrade D-Bus to version 1.16 or later.
9.2. What to do in case of in-place upgrade?
If you are upgrading from D-Bus 1.14 or earlier, upgrade D-Bus first, then upgrade the affected applications. Please note that upgrading from D-Bus 1.14 or earlier will break applications that are dependent on 1.15 or later. Upgrading an application may require manual changes to configuration files.
10. Conclusion
D-Bus is a system bus that allows applications to communicate with each other. Unauthorised access to D-Bus can potentially result in a variety of security issues including remote code execution. While this issue was officially announced as fixed in D-Bus 1.16, the issue was already resolved in D-Bus 1.15.2. An upgrade to D-Bus 1.15.2 is
References:
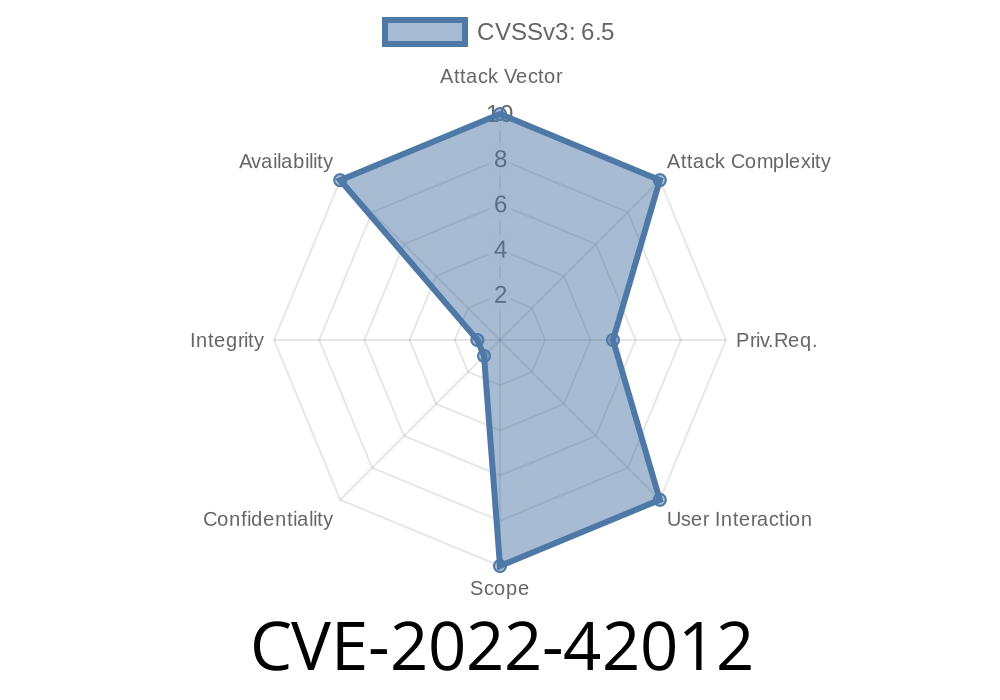
- CVE-2022-42012
- Link: https://usn.ubuntu.com/usn/usn-3076-1
Timeline
Published on: 10/10/2022 00:15:00 UTC
Last modified on: 11/14/2022 15:16:00 UTC
References
- https://www.openwall.com/lists/oss-security/2022/10/06/1
- https://gitlab.freedesktop.org/dbus/dbus/-/issues/417
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/SQCSLMCK2XGX23R2DKW2MSAICQAK6MT2/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/E4CO7N226I3X5FNBR2MACCH6TS764VJP/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ND74SKN56BCYL3QLEAAB6E64UUBRA5UG/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-42012