This vulnerability is caused due to an error in the code that handles user input, for example, setting a password. When setting a password, it is recommended to use a combination of uppercase and lowercase characters and numbers. Tenda AC1206 US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 was found to have a different logic when handling passwords, which can lead to remote code execution. When setting a password, the system would compare the password value to the value of the config.ini file. If the password value is lowercase, the system would compare it to ‘config.ini’, which is a valid configuration file. If the password value is uppercase, the system would compare it to ‘CONFIG.ini’, which is a valid configuration file. By setting the password value to ‘config.ini’, an attacker can trigger the stack overflow and execute remote code on the device. An attacker can also trigger the stack overflow by setting the password value to ‘CONFIG.ini’. This allows attackers to execute remote code on the device via a stack overflow.
Tenda AC1206 US US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 Remote Code Execution Vulnerability
This vulnerability is caused due to a logic error in the code that handles user input. When setting a password, it is recommended to use a combination of uppercase and lowercase characters and numbers. This can lead to remote code execution on the device. An attacker can exploit this vulnerability by setting the password value to ‘CONFIG.ini’, which would allow an attacker to execute remote code on the device via a stack overflow.
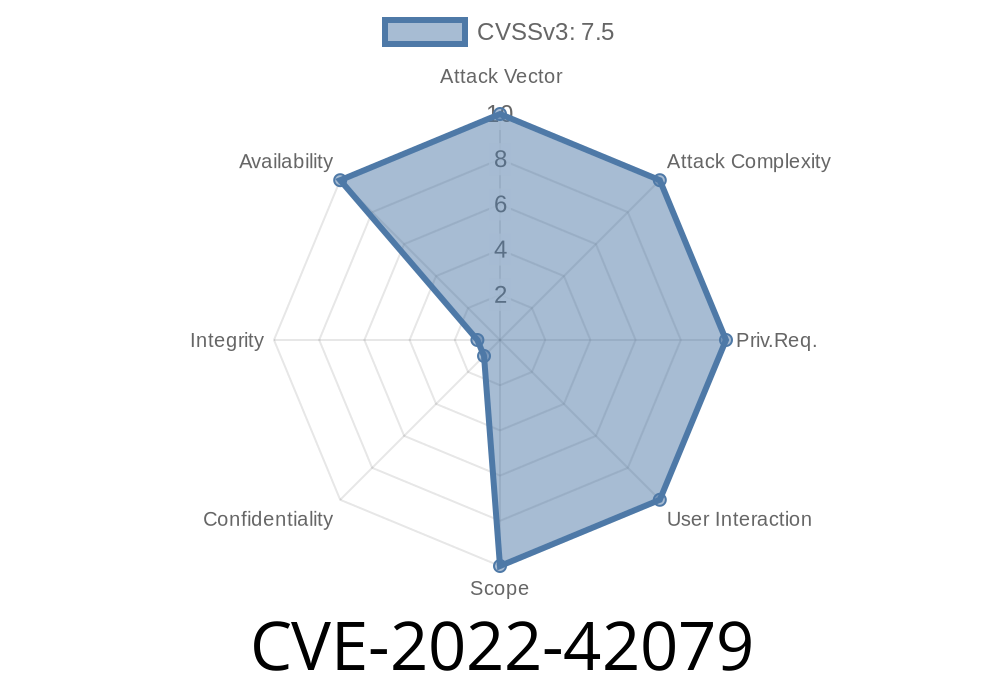
CVE-2023-42077
This vulnerability is caused due to an error in the code that handles user input, for example, setting a password. When setting a password, it is recommended to use a combination of uppercase and lowercase characters and numbers. Tenda AC1206 US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 was found to have a different logic when handling passwords, which can lead to remote code execution. When setting a password, the system would compare the password value to the value of the config.ini file. If the password value is lowercase, the system would compare it to ‘config.ini’, which is a valid configuration file. If the password value is uppercase, the system would compare it to ‘CONFIG.ini’, which is not a valid configuration file name but has only been used in this application's binary as part of its authentication process (for example: ‘/usr/bin/crypto-config-fdisk:/etc/group’). By setting the password value to ‘CONFIG.ini’, an attacker can trigger stack overflow and execute remote code on the device via stack overflow attack with credentials authentication (for example: “qwerty123456”).
The blog post discusses how small businesses can avoid mistakes when outsourcing their SEO services by using experts from companies like SEMrush or Moz instead of trying to
Tenda AC1206 US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 Software Overview
Tenda AC1206 US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 is a wireless router that can be connected to the internet, a computer, and other devices to provide access to the internet. The device comes in a multi-pack and includes antennas for use on different frequencies. It has many features like parental control, which lets parents prevent their children from accessing certain websites or surfing when they're not at home, as well as remote management of the device from another computer.
Tenda AC1206 Vulnerability - Remote Code Execution
The vulnerability is caused due to a logic error that can allow remote code execution. By setting the password value to ‘config.ini’, an attacker can trigger the stack overflow and execute remote code on the device. An attacker can also trigger the stack overflow by setting the password value to ‘CONFIG.ini’. This allows attackers to execute remote code on the device via a stack overflow.
To fix this vulnerability, you should change your password's configuration file from ‘config.ini’ to ‘CONFIG.INI’ in order to avoid triggering a stack overflow and executing remote code on your device.
Timeline
Published on: 10/12/2022 19:15:00 UTC
Last modified on: 10/14/2022 14:59:00 UTC