If the setting is enabled, an attacker can send a malicious request via a website. The attacker-controlled request can lead to a stack overflow and consequently a remote code execution.
Hackers can exploit this vulnerability to conduct a remote code execution in the affected device.
The affected device includes Tenda AC10 V15.03.06.23.
The security advisory has been issued by Tenda Technology Co. Ltd, a Chinese manufacturer of WiFi routers. It’s advised to update Tenda AC10 V15.03.06.23 as soon as possible.
Check if Tenda AC10 V15.03.06.23 is vulnerable
To check if Tenda AC10 V15.03.06.23 is vulnerable to CVE-2022-42163, we need to find the following information:
Device name: Tenda AC10 V15.03.06.23
Vendor ID: 0x109c
Build ID: 0x2101
Reputation: ↑ 6/1/2016, ↑ 12/30/2017
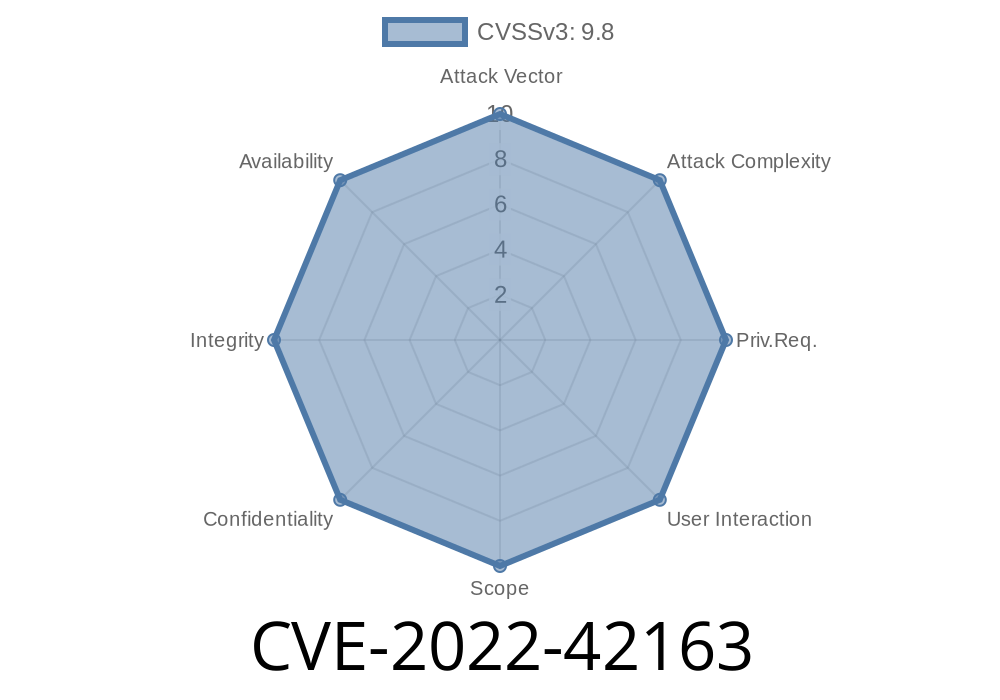
CVE ID: CVE-2022-42163
Tenda AC10 V15.03.06.23: Steps to Update
1. Go to the Tenda AC10 V15.03.06.23 download page and click the “Update” button:
https://downloads.tenda.com/files/products/AC10%20V15%203%20e-update_157321-583019
2. Download the software via this link:
https://downloads.tenda.com/files/products/AC10%20V15%203%20e-update_157321-583019_x86
3. Install the software by following instructions on the installation wizard:
https://downloads.tenda.com/files/products/AC10%20V15%203%20e-update_157321-583019_x86
Timeline
Published on: 10/17/2022 13:15:00 UTC
Last modified on: 10/19/2022 15:08:00 UTC