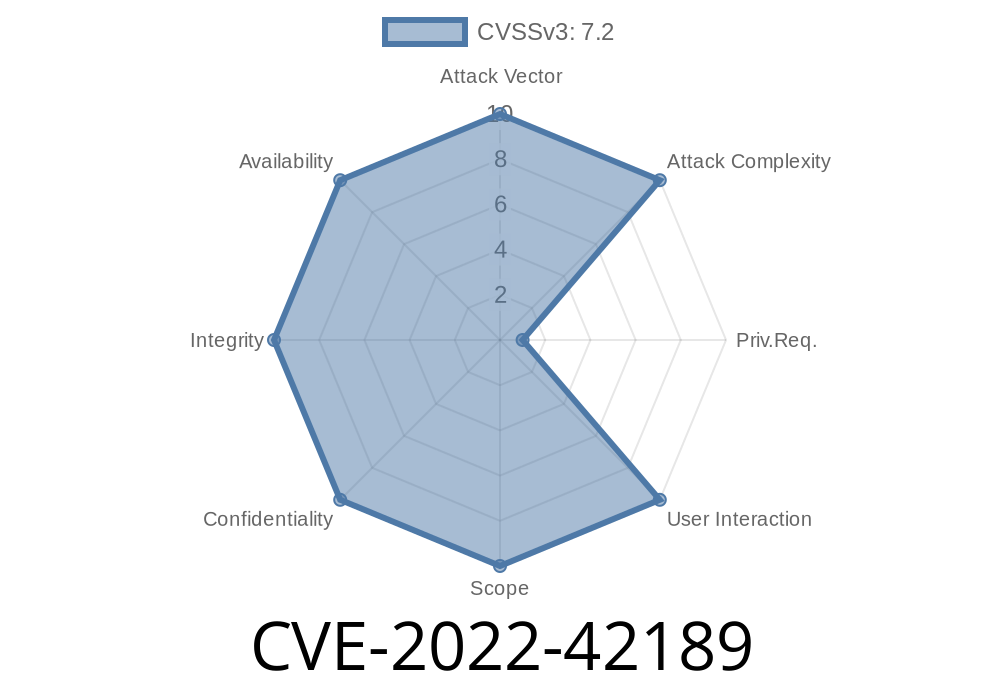
Emlog Pro is a web log analyser, which can be used to view, filter and search log data like Hacker News. Emlog Pro has a native plugin architecture, which allows users to extend the application with their own customised plugins. In order to install a customised plugin, the user needs to have administrative privileges on their WordPress website. Due to the nature of the native plugin architecture, installing a customised plugin on a non-administrative WordPress site might put the entire website at risk of being compromised. This is because an attacker could use a specially crafted plugin to perform a remote code execution on the website. Due to this plugin vulnerability, an attacker could take over a WordPress site and use it to host and spread malware or phishing pages. Since this plugin vulnerability allows remote code execution on WordPress sites, any WordPress site using this plugin version needs to be updated immediately.
Emlog Pro Remote Code Execution Vulnerability
The remote code execution vulnerability occurs due to a flaw in the plugin's installation process, which can allow an attacker to gain administrative privileges on a WordPress website. The vulnerability exists because Emlog Pro allows users with non-administrative privileges to install plugins without going through the standard installation process, with the current plugin version. This could put the entire website at risk of being compromised, as an attacker could use a specially crafted plugin to perform remote code execution on the website.
Update Emlog Pro v2.0.7 and v2.1.2 to prevent exploitation of remote code execution vulnerability
The plugin is vulnerable to remote code execution, which allows attackers to take over a WordPress site using the plugin and use it to infect visitors with malware or phishing pages. It is recommended that users update their Emlog Pro plugins to v2.0.7 and v2.1.2, which addresses this vulnerability.
Emlog Pro Plugin
Emlog Pro is a popular WordPress plugin, which provides users with the ability to search log data like Hacker News. The plugin has a native plugin architecture, which allows users to extend the application with their own customised plugins. In order to install a customised plugin on a non-administrative WordPress site, the user needs to have administrative privileges on their WordPress website.
However, due to the nature of the native plugin architecture, installing a customised plugin on a non-administrative WordPress site might put the entire website at risk of being compromised. This is because an attacker could use a specially crafted plugin to perform remote code execution on the website. Since this vulnerability gives an attacker remote control over a WordPress site, any WordPress site using this plugin version needs to be updated immediately.
Timeline
Published on: 10/21/2022 12:15:00 UTC
Last modified on: 10/22/2022 02:44:00 UTC