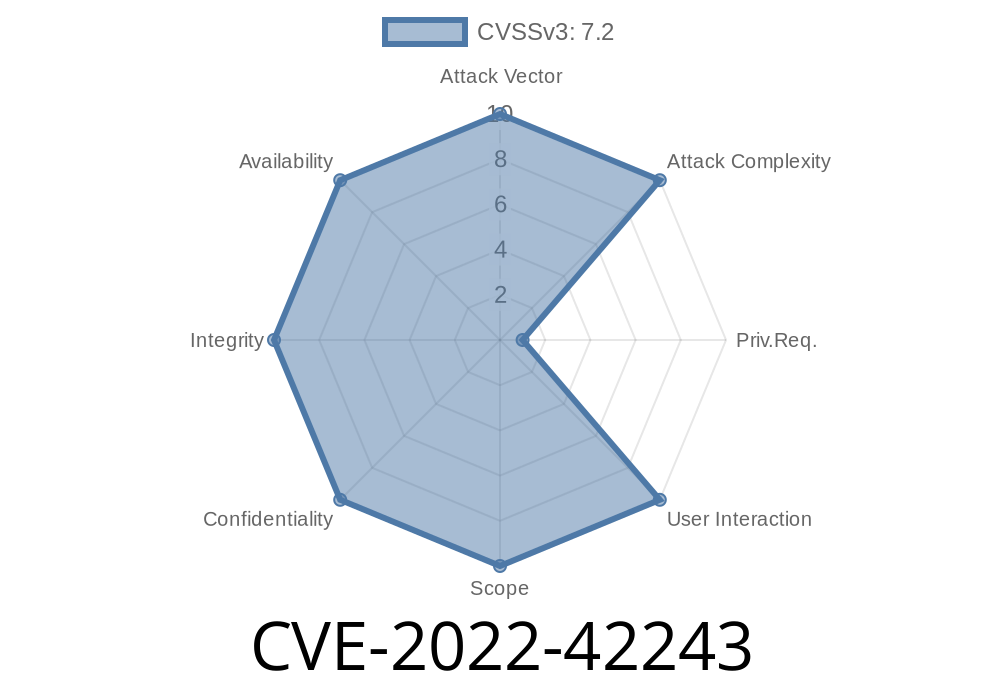
This can be exploited to execute arbitrary SQL commands. It is common practice to sanitize application input to reduce the risk of SQL injection. However, input validation should be performed as late as possible in the application flow, not at the point where data is being received. An attacker can inject specially crafted requests to a target application and exploit the weakness by saving malicious data into the application database. By default, the /csms/admin/storages/ management page enables the storage of up to 100 items. Therefore, an attacker only needs to send a small amount of carefully crafted requests to the management page to be able to exploit this vulnerability. Impact of vulnerability The attacker can save data into the application database to gain access to its functionality, obtain sensitive information, or even completely take over the application. Solutions Upgrade to version 1.0.8 or higher To prevent SQL injection attacks, we recommend not using direct user input for the database tables where data is stored. Depending on the type of application and the data concerned, applications may use data integrity checks, data encryption, or both.
SQL Injection
SQL injection is a class of attacks that involve exploiting SQL statements to inject or manipulate data. The goal of these attacks are to gain unauthorized access to data by changing it or adding new data into an application's database.
A classic example of SQL injection is when an attacker enters a command in the URL bar of a web page and the web page executes that command by inserting it into the database. This can be accomplished through input validation, which is done too late in the application flow. An attacker can enter crafted requests and exploit this vulnerability by saving malicious data into the application database. By default, the /csms/admin/storages/ management page enables the storage of up to 100 items. Therefore, an attacker only needs to send a small amount of carefully crafted requests to the management page to be able to exploit this vulnerability.
3.8
.1.2: SQL Command Injection
The GET parameters can be modified by an attacker in order to inject SQL commands. Solution Upgrade to version 1.0.8 or higher To prevent SQL injection attacks, we recommend not using direct user input for the database tables where data is stored. Depending on the type of application and the data concerned, applications may use data integrity checks, data encryption, or both.
Timeline
Published on: 10/06/2022 18:18:00 UTC
Last modified on: 10/06/2022 19:17:00 UTC