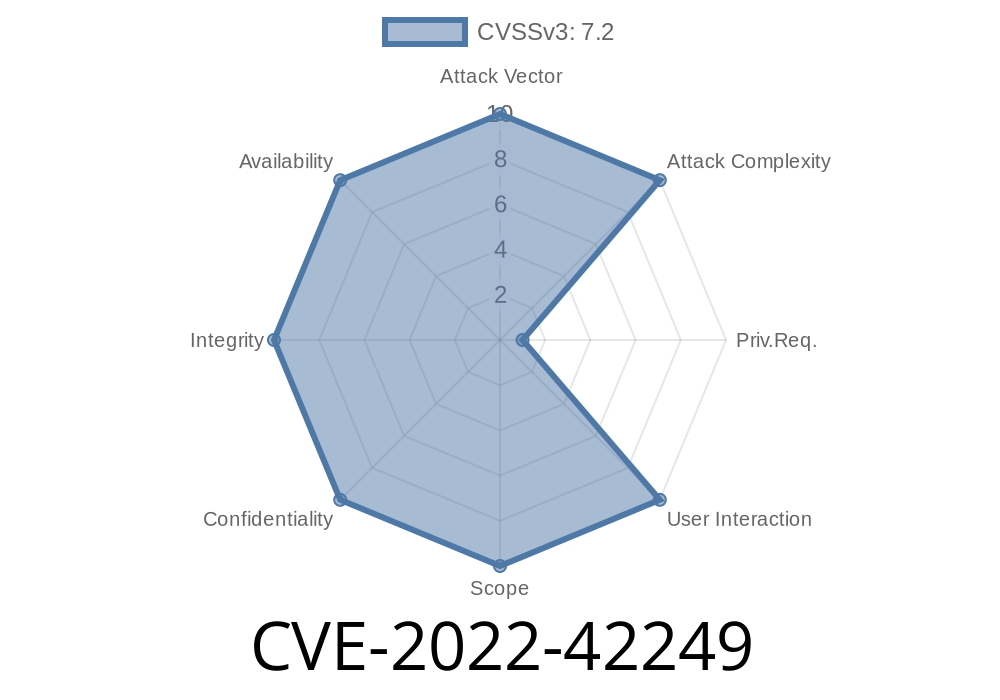
An attacker can inject malicious script code via the value of the storage_id parameter to execute arbitrary SQL commands. In addition, the /csms/admin/storages/view_storage.php?id= URI allows remote attackers to conduct XSS attacks via the code_entities parameter. These vulnerabilities can be exploited by remote attackers via the management interface or in the remote downloading of arbitrary files. Cold Storage Management System v1.0 is vulnerable to multiple cross-site request forgery (CSRF) vulnerabilities, allowing an attacker to hijack the authenticated session of an authenticated user and perform actions as that user, such as changing settings or downloading files. These vulnerabilities can be exploited by remote attackers via the management interface or in the remote downloading of arbitrary files. Cold Storage Management System v1.0 is vulnerable to SQL injection attacks. An attacker can exploit this vulnerability by injecting malicious script code into the value of the storage_id parameter via CSMS API. An attacker can also exploit this vulnerability by remote attackers via the management interface or in the remote downloading of arbitrary files. Cold Storage Management System v1.0 is vulnerable to XSS attacks. An attacker can exploit this vulnerability by injecting malicious script code via CSMS API. In addition, Cold Storage Management System v1.0 is vulnerable to stored XSS attacks
Products and Services Affected
Cold Storage Management System v1.0 is vulnerable to multiple cross-site request forgery (CSRF) vulnerabilities, allowing an attacker to hijack the authenticated session of an authenticated user and perform actions as that user, such as changing settings or downloading files. These vulnerabilities can be exploited by remote attackers via the management interface or in the remote downloading of arbitrary files. Cold Storage Management System v1.0 is vulnerable to SQL injection attacks. An attacker can exploit this vulnerability by injecting malicious script code into the value of the storage_id parameter via CSMS API. In addition, Cold Storage Management System v1.0 is vulnerable to stored XSS attacks and XSS attacks via CSMS API.
Products and Technologies Impacted
Cold Storage Management System v1.0 is vulnerable to multiple cross-site request forgery (CSRF) vulnerabilities, allowing an attacker to hijack the authenticated session of an authenticated user and perform actions as that user, such as changing settings or downloading files. These vulnerabilities can be exploited by remote attackers via the management interface or in the remote downloading of arbitrary files. Cold Storage Management System v1.0 is vulnerable to SQL injection attacks. An attacker can exploit this vulnerability by injecting malicious script code into the value of the storage_id parameter via CSMS API.
Stored XSS Attacks
A stored XSS vulnerability occurs when an error message that is displayed to a user is sent to the client's browser in the request, which allows an attacker to inject script code into it and execute arbitrary commands. Cold Storage Management System v1.0 is vulnerable to stored XSS attacks because of its interface where attackers can send malicious script code via the value of the storage_id parameter.
CWE-789: Improper Neutralization of Untrusted Input ('Stored XSS')
Cold Storage Management System v1.0 is vulnerable to stored XSS attacks. An attacker can exploit this vulnerability by injecting malicious script code via CSMS API. Cold Storage Management System v1.0 is vulnerable to SQL injection attacks. An attacker can exploit this vulnerability by injecting malicious script code into the value of the storage_id parameter via CSMS API. In addition, Cold Storage Management System v1.0 is vulnerable to XSS attacks. An attacker can exploit this vulnerability by injecting malicious script code via CSMS API. Cold Storage Management System v1.0 is not properly escapes user input before passing it to a SQL query in a POST request, which allows remote attackers to inject arbitrary HTML or JavaScript via a crafted request to execute arbitrary SQL commands
Timeline
Published on: 10/06/2022 18:18:00 UTC
Last modified on: 10/06/2022 19:20:00 UTC