A file with a directory structure can be created under arbitrary location as long as it exists on the system.
An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can overwrite arbitrary files by leveraging a path traversal in the pbx_extract_archive code.
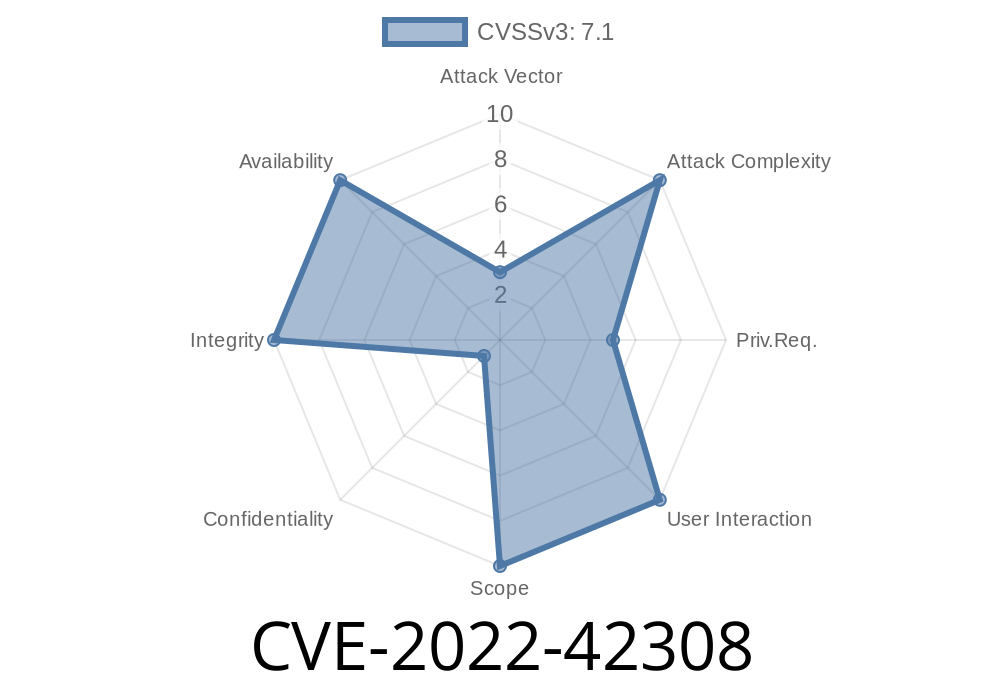
An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code.
An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code. An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code. An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code. An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the p
Solution
One solution for this is to limit the amount of users that have access to the file. Another option is to use ACLs to restrict access on a per-file or per-directory basis.
An issue was discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code. One solution for this is to limit the amount of users that have access to the file. Another option is to use ACLs to restrict access on a per-file or per-directory basis.
Veeam Backup 9.5 Update 1 - CVE-2107, 2109 and 2110
A vulnerability has been discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can overwrite arbitrary files by leveraging a path traversal in the pbx_extract_archive code.
A vulnerability has been discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code.
A vulnerability has been discovered in Veritas NetBackup through 8.2 and related Veritas products. An attacker with local access can create arbitrary files by leveraging a path traversal in the pbx_extract_archive code.
Timeline
Published on: 10/03/2022 15:15:00 UTC
Last modified on: 10/04/2022 21:09:00 UTC