An unprivileged user could use this flaw to elevate privilege to kernel code and possibly crash the system. A member of Red Hat's Technical Research team discovered that anon_vma double anon_vma allocation in mm/rmap.c before an anon_vma was double released before an anon_vma was unmapped. An user with r/w access to an anon_vma could use this flaw to leak an anon_vma to user mode and potentially execute code with r/w access to the anon_vma. This update also fixes another issue where an anon_vma was unmapped before it was released by reference count. An user with r/w access to an anon_vma could use this flaw to leak an anon_vma to user mode and potentially execute code with r/w access to the anon_vma. This update also fixes another issue where an anon_vma was unmapped before it was released by reference count. Red Hat Enterprise Linux 6 does not contain a fix for these issues. Updated packages for Red Hat Enterprise Linux 6 have been published. Red Hat Enterprise Linux 7 does not contain a fix for these issues. Updated packages for Red Hat Enterprise Linux 7 have been published.
These updated packages are being pushed to Red Hat Satellite, Red Hat Enterprise MRG and Red Hat Enterprise Linux for ARM. Users of Red Hat Enterprise Linux 6 and 7 are
^
Products Affected
An unprivileged user could use this flaw to elevate privilege to kernel code and possibly crash the system. A member of Red Hat's Technical Research team discovered that anon_vma double anon_vma allocation in mm/rmap.c before an anon_vma was double released before an anon_vma was unmapped. An user with r/w access to an anon_vma could use this flaw to leak an anon_vma to user mode and potentially execute code with r/w access to the anon_vma. This update also fixes another issue where an
anon_vma was unmapped before it was released by reference count. An user with r/w access to an anon_vma could use this flaw to leakan aanon_vma to user mode and potentially execute code with r/w access to the aanon_vma. This update also fixes another issue wherean aanon_vmawas unmapped before it was released by reference count.
Product : Red Hat Enterprise Linux 6
Package : kernel-2.6.32-573
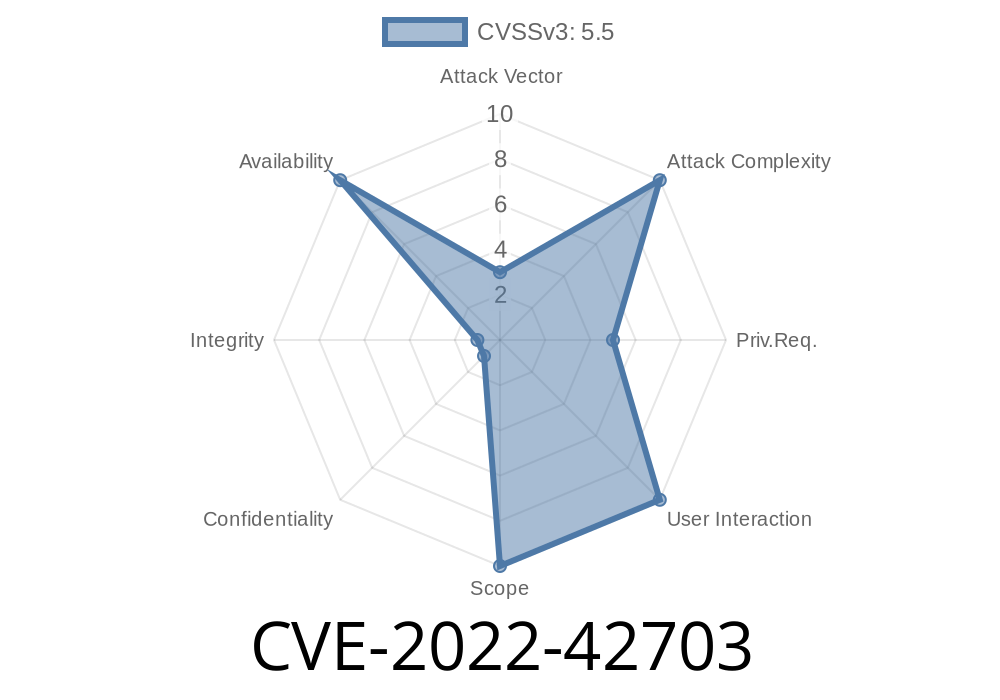
CVE ID # : CVE-2022-42703
Updated Package Not Available
There are no updates available for Red Hat Enterprise Linux 5
This flaw was discovered on June 4, 2019.
Potential Impact
An unprivileged user could use this flaw to elevate privilege to kernel code and possibly crash the system. A member of Red Hat's Technical Research team discovered that anon_vma double anon_vma allocation in mm/rmap.c before an anon_vma was double released before an anon_vma was unmapped. An user with r/w access to an anon_vma could use this flaw to leak an anon_vma to user mode and potentially execute code with r/w access to the anon_vma. This update also fixes another issue where an anon_vma was unmapped before it was released by reference count. An user with r/w access to a vma could use this flaw to leak a vma to user mode and potentially execute code with r/w access to the vma. This update also fixes another issue where a vma was unmapped before it was released by reference count.
Timeline
Published on: 10/09/2022 23:15:00 UTC
Last modified on: 10/11/2022 18:46:00 UTC
References
- https://bugs.chromium.org/p/project-zero/issues/detail?id=2351
- https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=2555283eb40df89945557273121e9393ef9b542b
- https://cdn.kernel.org/pub/linux/kernel/v5.x/ChangeLog-5.19.7
- https://github.com/torvalds/linux/commit/2555283eb40df89945557273121e9393ef9b542b
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-42703