If a user has write access to the folder, this user could insert malicious code in the application and execute it with the rights of the web application user. This vulnerability could be exploited by taking advantage of the fact that the syngo Dynamics web application is running on the application server. The application server account assigned to the website’s application pool has the necessary rights to access data in any folders.
The vulnerability exists in the operation of write of the syngo Dynamics’ web service. The operation allows the user to write any data in the server.
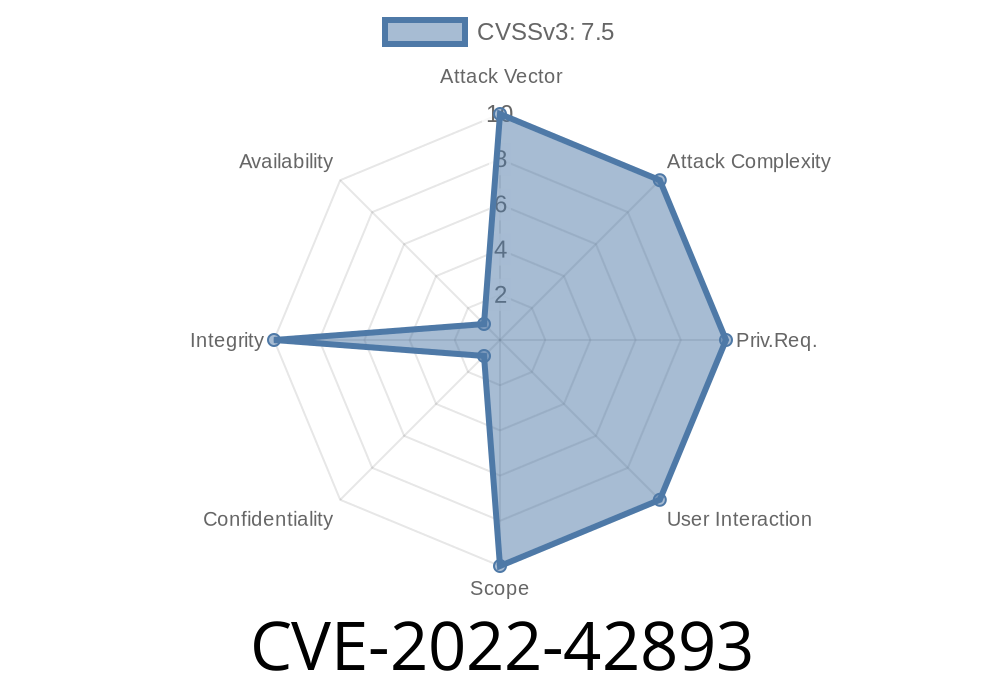
The vulnerability (CVE-2019-0891) has been assigned to this issue and it has been published on the MITRE CVE list.
SOLUTION To prevent the exploitation of this vulnerability, you must update syngo Dynamics to the latest version. Currently, the syngo Dynamics version available on the market is syngo Dynamics Version 9.1.1.
Where can I get the latest version? -> syngo dynamics website
What are the system requirements for updating syngo Dynamics? -> syngo dynamics website
Syngo Dynamics – The web application vulnerable to compromise
The web application is vulnerable to compromise.
If a user has write access to the folder, this user could insert malicious code in the application and execute it with the rights of the web application user. This vulnerability could be exploited by taking advantage of the fact that the syngo Dynamics web application is running on an application server.
The vulnerability (CVE-2019-0891) has been assigned to this issue and it has been published on the MITRE CVE list.
Timeline
Published on: 11/17/2022 17:15:00 UTC
Last modified on: 11/21/2022 18:24:00 UTC