An attacker can exploit this vulnerability to execute arbitrary SQL commands with root privileges. This may lead to the compromise of the affected site. An attacker may also be able to trick users into running arbitrary code if they follow a legitimate looking link.
An attacker could also leverage the cross-site scripting (XSS) vulnerability at XSS in website_cmn_web.php via the code parameter.
An attacker could also exploit the insufficient validation of user-supplied input at XSS in website_cmn_web.php via the code parameter.
An attacker may also be able to inject arbitrary JavaScript into an affected site via XSS in website_cmn_web.php via the code parameter.
An attacker may also be able to execute arbitrary code if they force a user to click on a malicious link if the site has a vulnerable CRM. If a user is logged in, this may lead to the compromise of user accounts as well.
It should be noted that the id and code parameters are currently being actively exploited by attackers.
It should be noted that the id and code parameters are currently being actively exploited by attackers.
Vulnerability discovered:
The vulnerability was discovered by security researcher Devin J. Clarke.
Fixed in Apache Struts 2.0.0h 2.0.0h
Solution
An attacker could also leverage the XSS vulnerability at XSS in website_cmn_web.php via the code parameter to execute arbitrary SQL commands with root privileges.
Specifics: The following is a list of specific details for the Apache CMS 2.0.x 4.0.x and 4.1.x versions:
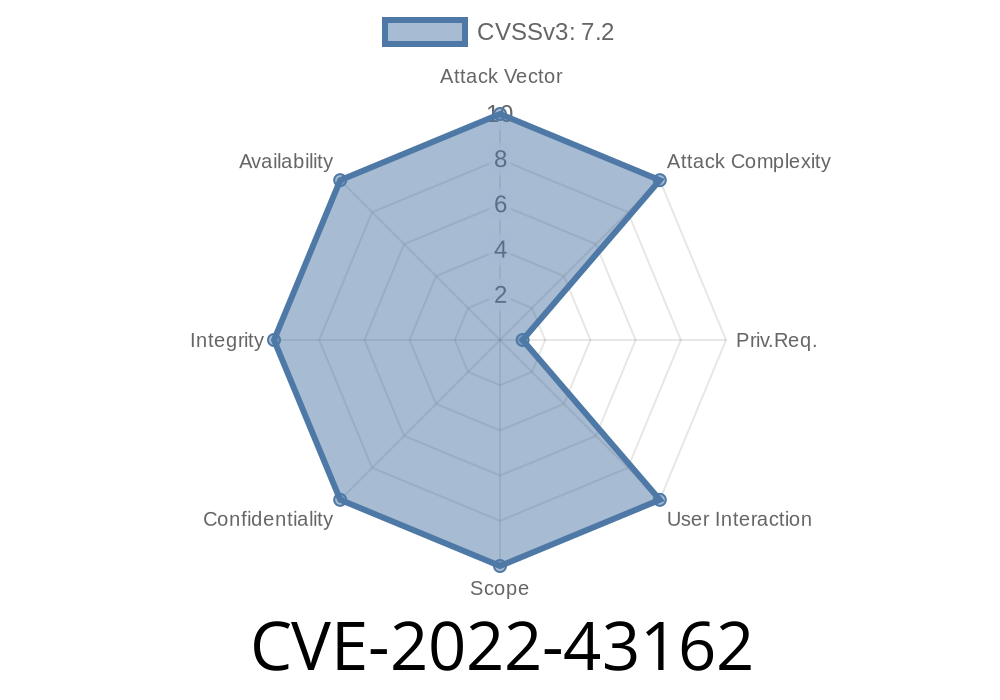
- CVE-2022-43162: SQL injection vulnerability that may be exploited by an attacker to execute arbitrary commands with root privileges and other system access
- CVE-2018-12024: Cross site scripting vulnerability in website_cmn_web.php that may be exploited by an attacker to inject arbitrary JavaScript into the affected site
- CVE-2018-12025: Inadequate validation of user input that may be exploited by an attacker to perform XSS attacks
- CVE-2017-3482: Cross site scripting vulnerability in website_cmn_web.php that may be exploited by an attacker to inject arbitrary JavaScript into the affected site
Timeline
Published on: 11/17/2022 21:15:00 UTC
Last modified on: 11/18/2022 18:25:00 UTC