This vulnerability allows attackers to steal users’ information by tricking them into visiting a malicious website or email. When you update your WP app book plugin, make sure to disable the email confirmation setting or enable the setting for the email address that is receiving the plugin update notification. This will prevent attackers from being able to use the information obtained by this vulnerability to steal users’ login credentials. To stay up-to-date with the latest information regarding this issue, make sure to visit the Appointment Booking Calendar plugin security release page on every update.
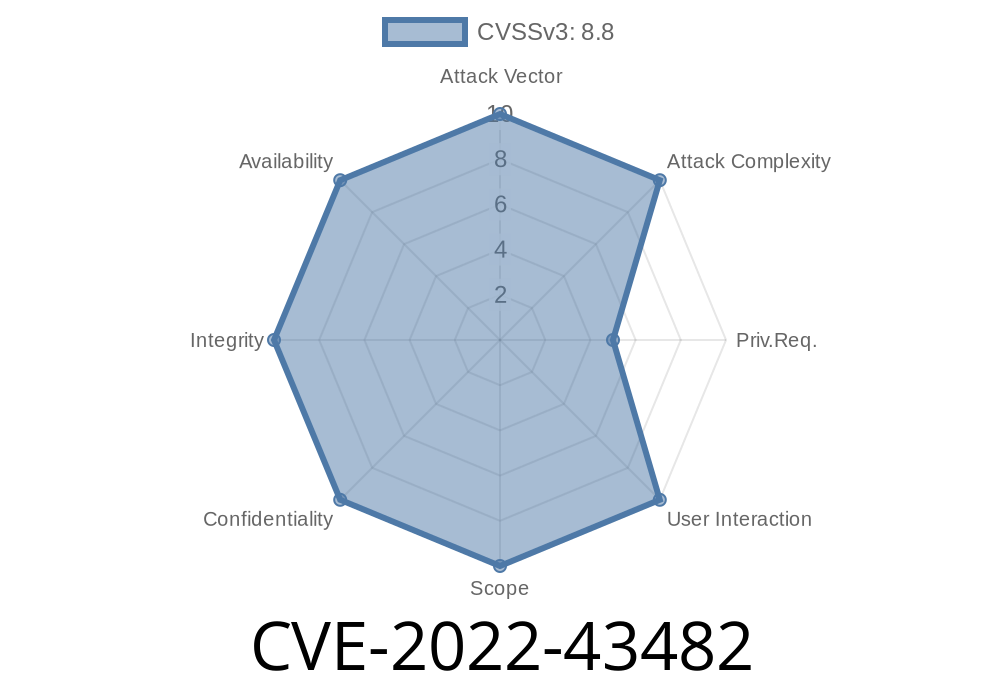
Summary of CVE-2022-43482
This vulnerability allows attackers to steal users’ information by tricking them into visiting a malicious website or email. When you update your WP app book plugin, make sure to disable the email confirmation setting or enable the setting for the email address that is receiving the plugin update notification. This will prevent attackers from being able to use the information obtained by this vulnerability to steal users’ login credentials. To stay up-to-date with the latest information regarding this issue, make sure to visit the Appointment Booking Calendar plugin security release page on every update.
Vulnerability Details: CVE-2022-43482
This vulnerability allows attackers to steal users’ information by tricking them into visiting a malicious website or email. This can be used in conjunction with the CVE-2018-10110 vulnerability which was fixed in the WP App Book plugin version 2.9.4, to steal users’ login credentials. The following describes how this vulnerability works:
1) A user creates a book appointment on their calendar for a specific date and time slot.
2) A malicious website or email comes along and tries to persuade the user to change their appointment from the day before to another date or time slot that is less attractive because they don’t want anyone else to have it.
3) When an attacker persuades the user, they are then redirected back to the original calendar item where their new appointment is now set for their desired time slot.
4) The attacker now has access to all of the private information associated with this booked appointment and can not only change it but also delete it completely if they so choose.
Description of The WordPress Plugin - Appointment Booking Calendar Vulnerability
A vulnerability in the WP Appointment Booking Calendar plugin that allows attackers to steal users' information by tricking them into visiting a malicious website or email. When you update your WP app book plugin, make sure to disable the email confirmation setting or enable the setting for the email address that is receiving the plugin update notification. This will prevent attackers from being able to use the information obtained by this vulnerability to steal users' login credentials. To stay up-to-date with the latest information regarding this issue, make sure to visit the Appointment Booking Calendar plugin security release page on every update.
Vulnerability overview
This vulnerability allows attackers to steal users’ information by tricking them into visiting a malicious website or email. It consists of two parts:
1. A vulnerability found in the WP app book plugin that allows attackers to steal users’ login credentials, if they accept email confirmation from the plugin update notification and then visit a malicious website or email.
2. An email confirmation setting in Settings -> Appointment Booking Calendar -> Options that can be changed to prevent attackers from being able to use the information obtained by this vulnerability to steal users’ login credentials.
Timeline
Published on: 11/18/2022 20:15:00 UTC
Last modified on: 11/21/2022 17:04:00 UTC