In April 2023, Google patched a critical vulnerability tracked as CVE-2023-2033 that affected the V8 JavaScript engine used in Chrome. This vulnerability is a classic type confusion bug that attackers could use to run arbitrary code in your browser—often just by getting you to visit a booby-trapped website.
This post will walk you through what happened, what "type confusion" means, how attackers could have exploited this bug, and include relevant code snippets. All sources are cited, and the content is as clear as possible for readers with a basic understanding of how browsers and JavaScript work.
What Is Type Confusion in V8?
Type confusion refers to a programming error where a piece of code assumes a variable or object is of one type, but in reality, it’s of another. In languages like C++, which power V8, mixing types like this can lead to memory corruption.
In the context of a JavaScript engine like V8, this is dangerous: JavaScript is dynamically typed, but browsers' engines optimize by making assumptions about types for speed. If an attacker can trick the engine, those assumptions can break, opening the door to tricking the browser into writing or reading memory it shouldn't.
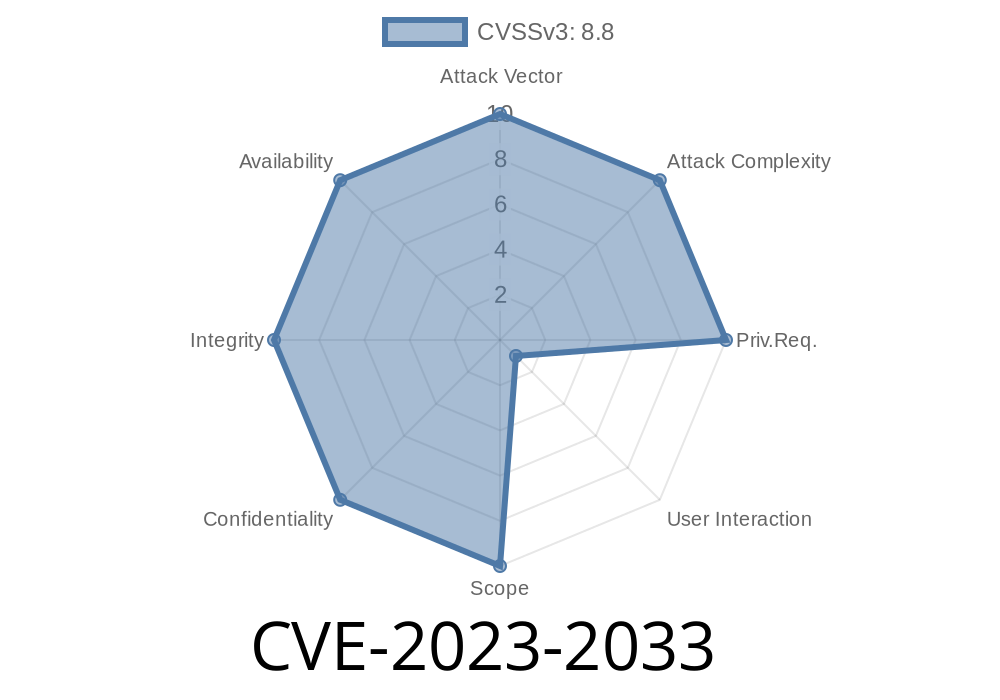
The CVE Details
- Vulnerability ID: CVE-2023-2033
Patch Date: April 2023
Google security advisory
Security report from TheZeroMan
Run arbitrary code: Ultimately, if crafted right, achieve remote code execution (RCE).
This can all happen with just a crafted HTML page—no other interaction needed.
1. Exploit Strategy
A typical exploit involves confusing the V8 engine about the type held in a variable using arrays of objects and numbers, leveraging functions like Array.prototype.map or special objects called "butterflies" in memory.
Here's a simplified JavaScript snippet that can show what a type confusion bug may look like in a JavaScript engine. Note: This code is nearly illustrative; direct exploit code isn't published here for safety.
// Setting up a "fake object" scenario
let numbers = [1.1, 1.2, 1.3];
let objects = [{}, {}, {}];
// Using a vulnerable V8 optimization
function confuseType(arr, val) {
arr[] = val;
return arr[];
}
// In real exploits, under certain conditions, the engine thinks
// numbers[] is a double, but an attacker writes an object to it.
let result = confuseType(numbers, {});
In V8's memory, this mix-up can allow reading/writing out-of-bounds or to controlled memory, breaking out of browser sandboxes.
Confuse array type: Hold doubles in arr, assign object, confuse V8 about type.
2. Read/write primitive: Achieve arbitrary memory read or write.
Hijack control flow: Overwrite function pointers or create fake objects.
4. Escape sandbox / pop a shell: Plant payload and execute code.
Chrome’s Official Fix
The fix was tracked as commit 5ea4f2a in V8 and landed in Chrome 112..5615.121.
Patch details:
// In simplified C++ V8 internals:
if (object_is_expected_type) {
// Safe path
} else {
// Throw error, prevent confusion
}
V8 maintainers added stricter type checks to make sure values placed in arrays matched the expected type, closing the loophole.
Other browsers using V8 (like Edge, Brave, Opera) prior to patch.
Remediation:
- Update Chrome now! Go to chrome://settings/help to force an update.
Technical References
- Chromium Blog: Stable Channel Update for Desktop
- CVE-2023-2033 NVD Entry
- V8 Git Commit
- Zero Day Initiative Report
V8 is a constant target—expect regular high-severity bugs and keep Chrome up to date.
If you want to experiment safely, set up a sandboxed virtual machine and study old V8 bugs. Never test proof-of-concepts on your real device.
Timeline
Published on: 04/14/2023 19:15:00 UTC
Last modified on: 04/18/2023 12:50:00 UTC