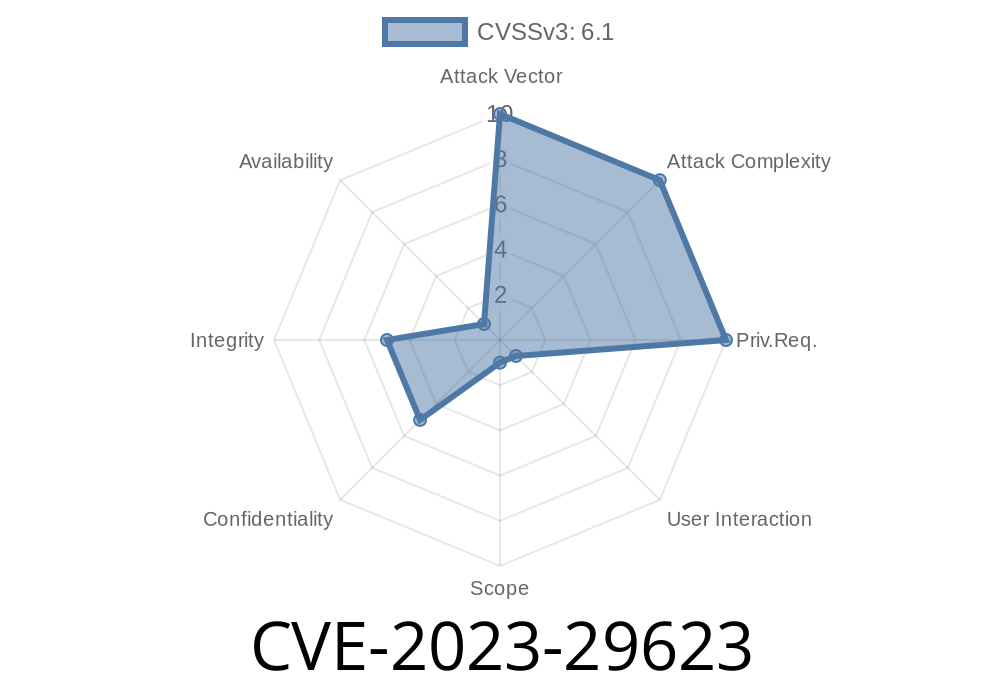
CVE-2023-29623 is a recently identified vulnerability affecting Purchase Order Management v1., a popular open-source PHP application used by small and medium businesses to manage purchase orders. The flaw traces back to a security weakness—a *reflected Cross-Site Scripting (XSS)*—in the login process. In this deep dive, we’ll break down how this vulnerability works, how dangerous it can be, and how you can test for and fix it.
What’s the Vulnerability?
Attackers discovered that the password parameter in the file /purchase_order/classes/login.php does not properly filter user-supplied input. This oversight allows malicious scripts to be injected into responses, opening the door to XSS attacks.
In plain terms: If an attacker can trick an admin or user into clicking a specially crafted link, their browser will run the attacker's code.
What is Reflected XSS?
Reflected XSS is when user input sent to a web application (like URLs or form fields) gets echoed (reflected) back in the web page without being sanitized or filtered. This lets attackers inject and execute code in the victim's browser.
How Does CVE-2023-29623 Work?
The issue arises because the login handler (/purchase_order/classes/login.php) takes whatever you enter into the password field and reflects it back in the response, unsanitized.
Here’s the vulnerable PHP code snippet:
// This is a simplified excerpt representing the vulnerable behavior
$password = $_POST['password'];
if ($password != $db_password) {
echo "Password '$password' is incorrect!";
}
Without escaping HTML, any input in the password field ends up inside the page output.
`
http://example.com/purchase_order/classes/login.php?password=%3Cscript%3Ealert('XSS')%3C/script%3E
`
The value for password here is <script>alert('XSS')</script> but URL-encoded.
2. Victim clicks the link. The server processes the request and echoes back the unsanitized password parameter:
`html
Password 'alert('XSS')' is incorrect!
Here’s a one-liner *curl* command to demonstrate the XSS payload
curl -X POST "http://example.com/purchase_order/classes/login.php"; -d "username=admin&password=<script>alert('CVE-2023-29623')</script>"
Or, just open in your browser (replace with your deployment URL)
http://example.com/purchase_order/classes/login.php?password=%3Cscript%3Ealert('CVE-2023-29623')%3C/script%3E
Phishing: Displaying fake forms and harvesting credentials.
Anyone with a valid user account could become a victim if they click a poisoned link.
Look for suspicious login attempts and unusual parameters in your access logs.
- Use tools like XSS Hunter or OWASP ZAP for testing.
References
- Original CVE: CVE-2023-29623 at NVD
- Purchase Order Management Project: SourceCodester
- OWASP XSS Prevention Cheat Sheet: Link
Summary
CVE-2023-29623 demonstrates how a simple oversight in handling user input—especially in login routines—can lead to severe security risks like XSS. If you use Purchase Order Management v1., update as soon as a fix is released, and always sanitize user input in your own projects.
Timeline
Published on: 04/14/2023 02:15:00 UTC
Last modified on: 04/20/2023 19:16:00 UTC