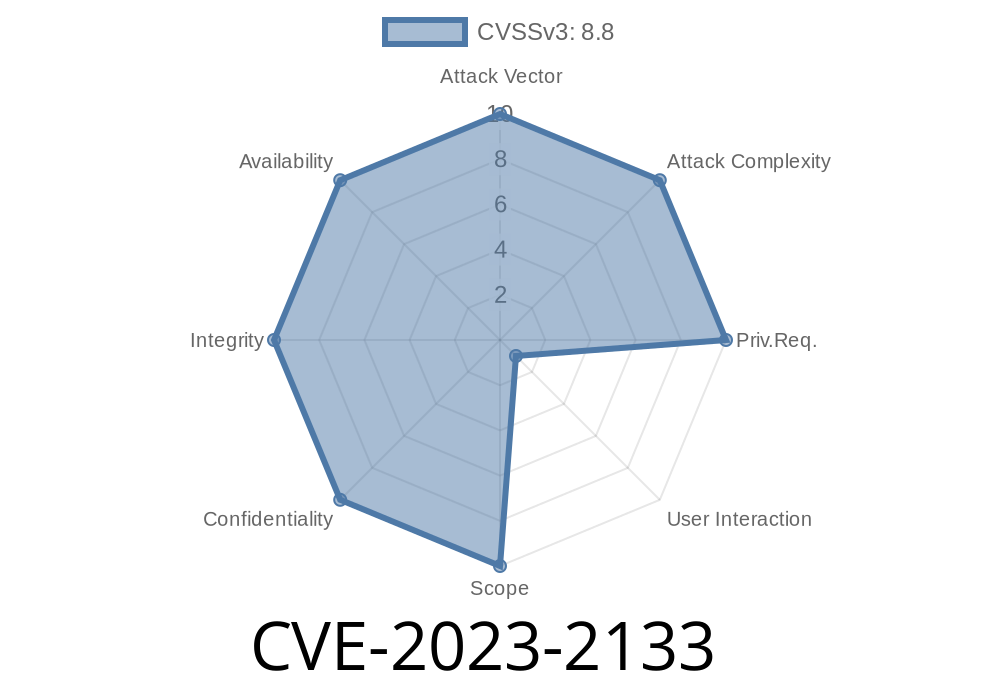
In April 2023, Google published details on a serious security flaw—CVE-2023-2133—affecting Chrome’s Service Worker API prior to version 112..5615.137. This vulnerability was marked with high severity because it permitted remote attackers to potentially corrupt heap memory using a specially crafted HTML page. In this post, we’ll break down what this flaw means, how it can be exploited, and what you need to do to stay safe. We’ll also provide a simplified proof-of-concept and reference links for further reading.
What Is the Service Worker API?
Service Workers are scripts that run in the background in modern browsers. They help webpages work offline, handle push notifications, and boost performance with features like background sync and resource caching.
What Went Wrong?
With CVE-2023-2133, Chrome’s implementation of the Service Worker API had a bug that let attackers create out-of-bounds memory access. In simpler words: By sending the browser unexpected input, an attacker could make Chrome read or write past the end of an intended memory region. This is especially dangerous with heap memory, as it’s where web browsers store objects like images, scripts, and webpage data.
Out-of-bounds access could lead to browser crashes (denial of service), or worse—attackers running their own code on your device.
A Look at the Bug
While Google restricts detailed exploit info to protect users, the essence of this vulnerability revolves around mishandling data types or object boundaries when processing certain Service Worker requests.
Let’s imagine a scenario like this (code is simplified for learning purposes and does not contain any -day exploit!):
// Suppose there's a bug handler in the old Chrome code
function createServiceWorker(arrayBuffer) {
let maxLength = 1024;
// Fails to check the real size of arrayBuffer!
let buf = new Uint8Array(maxLength);
buf.set(new Uint8Array(arrayBuffer)); // What if arrayBuffer > 1024?
}
Here, if arrayBuffer is larger than maxLength, the set() call will write past the buf array—an out-of-bounds write.
Attackers could trigger similar bugs by designing a malicious HTML page. If a user visits this page, their browser could process bad input and corrupt heap memory.
How an Attacker Could Exploit This
1. Prepare a Malicious Site: The attacker creates a webpage containing code that abuses the Service Worker registration or messaging API, sending oversized or malformed data.
Lure Victims: The attacker convinces users to open the URL (email, social media, phishing).
3. Trigger the Bug: When Chrome processes the crafted data, it writes outside the bounds of a memory buffer.
Bypass browser security features (sandboxing, etc.).
Here’s a pseudo-proof-of-concept of what malicious JS could look like (for illustrative purposes only!):
// Simulate overloading Service Worker registration
const bigBlob = new ArrayBuffer(20480); // Way larger than typical
navigator.serviceWorker.register(
URL.createObjectURL(new Blob([bigBlob]))
).catch(e => console.error('Crash attempt:', e));
Note: Actual exploitation requires detailed understanding of Chrome internals—which is not detailed here for safety reasons.
Google fixed the vulnerability in version 112..5615.137 and later. Upgrade immediately!
Official Chrome Release Notes:
https://chromereleases.googleblog.com/2023/04/stable-channel-update-for-desktop_25.html
Chromium Issue Tracker (limited info):
https://crbug.com/1437793
References
- Chrome Release Blog: Stable Channel Update for Desktop
- CVE Record: CVE-2023-2133
- Chromium Security FAQ
- Mitre CVE Listing
Conclusion
CVE-2023-2133 is a reminder that even modern, secure browsers can have subtle bugs with big consequences. Make sure your Chrome browser is up-to-date, and keep an eye on the latest security news. Most importantly, stay alert and browse safely!
Timeline
Published on: 04/19/2023 04:15:00 UTC
Last modified on: 05/02/2023 03:15:00 UTC