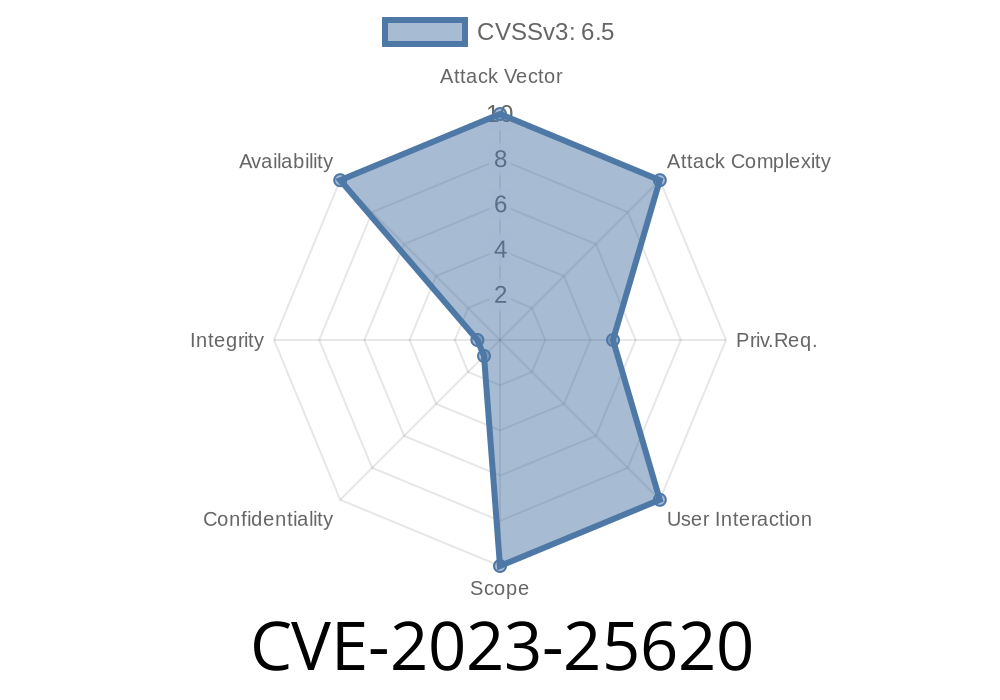
On February 2023, a serious vulnerability was disclosed under the identifier CVE-2023-25620. This flaw falls under the category CWE-754: Improper Check for Unusual or Exceptional Conditions. Attackers can exploit it to crash or disable industrial controllers by loading a specially-crafted project file—if they have legitimate user access.
This vulnerability affects critical industrial infrastructure and highlights why rigorous input validation and error handling are so important in controller software.
What is CVE-2023-25620?
In simple terms, the flaw lives in the way some industrial controllers—commonly used in factories and critical systems—check project files when a user uploads one. Specifically, the controller software doesn't properly check for unusual or unexpected file conditions. If a user (with valid authentication) uploads a maliciously-crafted project file, they can make the controller crash or become unresponsive. This is a classic Denial of Service (DoS) scenario.
Why Is This Dangerous?
- Interrupts operations: A controller going down can stop entire factory lines or critical processes.
- Requires valid login: Only authenticated users can trigger it, but many systems have shared or weak credentials.
- No code execution: It's not a remote code execution vulnerability, but stopping a controller can be just as damaging in industrial settings.
How Does the Vulnerability Work?
When a project file is uploaded, the controller's firmware/software reads the file. It expects certain data to be valid and within normal ranges. But the software does not properly check for corrupted or abnormal data fields. If these fields are malformed in a certain way, the controller hits an unexpected error and either:
A simplified pseudo-code example (not the real source code!) to illustrate the problem
// Pseudo-code
function importProject(file):
data = readFile(file)
if (data.projectID < || data.projectID > MAX_PROJECT_ID):
throw Error("Invalid project ID!") // Proper check
// But what actually happens:
// (missing error check)
processProjectData(data) // If data is invalid, can crash here
Missing bounds checking or not handling unusual file contents leads to denial of service when unexpected data is encountered.
Requirements
- Attacker must have valid login to the controller (e.g., local network or stolen/found credentials)
Steps
1. Attacker crafts a project file with invalid or unexpected values where the controller does not expect them.
Controller process crashes or enters a fault state
- Operations halt until physical/manual reset
For confidentiality reasons, real formats can't be shared, but imagine this pattern
// Pseudo project file structure
PROJECT_ID: -1
SIGNATURE: 'FAKE'
DATA: [corrupted or extremely large/random data]
Upload this file. When the controller sees PROJECT_ID: -1 (in a field expecting positive numbers), bad things happen because the software isn't programmed to say "that's not okay."
Affected Devices
This vulnerability is most relevant for certain industrial controllers and PLCs (Programmable Logic Controllers). Specific vendors and product lines are listed in the official advisories (see links below). Generally affected are controllers where authenticated users can upload and apply project files.
Real References
- MITRE CVE Record for CVE-2023-25620
- CISA Advisory ICSA-23-047-02
- Siemens ProductCERT Advisory
*(Check the above for vendor statements, patches, and further technical details.)*
Conclusion
CVE-2023-25620 is a powerful reminder: just because a user is authenticated doesn't mean uploaded files can be trusted blindly. Industrial systems must expect the unexpected, always validate imported files, and handle exceptional conditions gracefully.
If you run industrial controllers, take this vulnerability seriously. Patch your systems, harden access controls, and talk with your vendors if you’re unsure about your exposure!
Stay secure—and remember: always verify, never just trust.
If you have affected devices, check the references above for detailed vendor instructions.
Timeline
Published on: 04/19/2023 09:15:00 UTC
Last modified on: 04/27/2023 01:22:00 UTC