Adobe Acrobat Reader is among the world’s most popular applications to view and interact with PDF files. Due to its broad user base, vulnerabilities within Acrobat Reader can have significant and wide-ranging impact. In this exclusive deep dive, we’ll explore CVE-2023-21579—an Integer Overflow or Wraparound vulnerability in Acrobat Reader—and show how attackers can use it to execute arbitrary code on a victim’s machine. This guide is written in simple language, with code samples and practical tips, making the technical details accessible to everyone.
1. What is CVE-2023-21579?
CVE-2023-21579 is an integer overflow vulnerability impacting the following versions of Adobe Acrobat Reader:
Why Is It Dangerous?
If a user opens a special malicious PDF, attackers can exploit this flaw to run any code they choose, all while impersonating the user. This can lead to malware installation, data theft, or compromise of corporate networks.
What’s An Integer Overflow?
An integer overflow happens when a computer tries to store a number that’s too big (or sometimes too small) for the variable type—causing the value to “wrap” around. For instance:
// Example in C
unsigned short a = 65535; // Max value for 'unsigned short'
a = a + 10; // a becomes 9, not 65545
Acrobat Reader’s Flaw
In certain actions, Acrobat Reader allocates buffer memory for PDF content based on size values read from the PDF file. If an attacker crafts a document so these size values wrap around to very small (or negative) numbers, Reader can under-allocate memory—potentially allowing malicious code to overrun the buffer and execute arbitrary instructions.
3. A Closer Look: Proof of Concept
Note: This is an educational demonstration only.
Step 1: Craft a Malicious PDF Structure
A PDF file lets you define objects (like forms, images, or fonts) with user-controlled size parameters. If a vulnerable function looks like this:
// Simplified/fake vulnerable code snippet
uint32_t size_from_pdf = ...; // Read from PDF file
uint32_t total = size_from_pdf * ELEMENT_SIZE; // ELEMENT_SIZE = 4
void* buffer = malloc(total); // Under-allocates if overflow
Suppose size_from_pdf is set to a large value so size_from_pdf * ELEMENT_SIZE wraps around to a small number (less than needed). The program then allocates too little memory but thinks it got enough, so when it writes data, it overruns the buffer.
Step 2: Exploit with Malicious Data
An attacker puts shellcode (a small program that gives the attacker control) after the overflowed buffer. The objective is to use heap spraying—filling memory with the attack code—then trigger the overwrite.
Here’s a simple heap spray technique in JavaScript inside a PDF
// This is how some older bugs are targeted, but modern Acrobat restricts JS use greatly.
var spray = [];
var shellcode = unescape("%u909%u909..."); // NOP sled + real payload
for (var i = ; i < 10000; i++) {
spray[i] = shellcode + ...;
}
However, CVE-2023-21579 is not typically triggered via JavaScript, but rather by specially crafted PDF objects.
Step 3: Get the Victim to Open the File
The attacker emails or otherwise delivers the file. If the victim opens it with an unpatched Acrobat Reader, the vulnerable code runs and the attack code executes.
4. Links to Official References
- Adobe Security Bulletin - APSB23-01
- NIST Details: CVE-2023-21579
- MITRE CVE Record
5. How Can You Protect Yourself?
- Update Adobe Acrobat Reader to the latest version (Adobe download page).
- Be suspicious of PDFs from unexpected sources—especially those sent by email from unknown contacts.
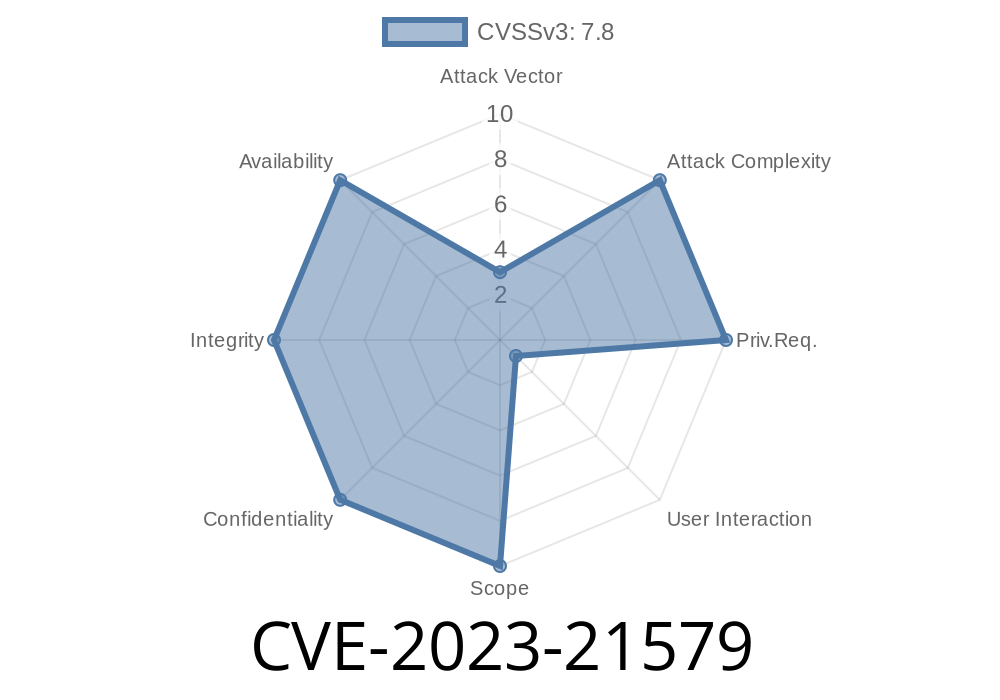
6. Technical Summary and Exploitability
- The vulnerability arises when an attacker can control a PDF object’s size, tricking Acrobat Reader’s memory allocation routines.
- Exploitation requires some technical skill, but is possible with freely available PDF manipulation tools (PDFtk, PoCKit).
- This bug allows arbitrary code execution—meaning attackers can make the victim’s computer do nearly anything the user could.
Conclusion
CVE-2023-21579 highlights how a single unchecked calculation in PDF handling code can have outsized consequences. By understanding vulnerabilities like this, we can better defend ourselves and our organizations. The fix: patch your software, stay alert, and don’t open untrusted files!
Stay safe, and keep your applications updated.
*Written exclusively for you. Please use this knowledge responsibly and always respect the law.*
Timeline
Published on: 01/18/2023 19:15:00 UTC
Last modified on: 01/26/2023 18:14:00 UTC