CVE-2023-22041 is a security vulnerability discovered in several Oracle Java platforms, including Oracle Java SE (Java’s core runtime engine), Oracle GraalVM Enterprise Edition, and Oracle GraalVM for JDK. This issue specifically impacts the HotSpot component—a key part of Java's execution environment.
The bug is notable because it allows attackers who can run code on your machine (for example, through a malicious Java applet or Java Web Start application) to potentially break free of the Java "sandbox" and access confidential data. While exploitation is tough, it's a serious issue if you run untrusted Java code from the internet on vulnerable installations.
This vulnerability mostly affects
- End-users who run Java Web Start applications or Java applets from untrusted sources on the affected versions.
- Java installations that execute 3rd-party, possibly malicious, code in a sandbox (not trusted code!).
Typical server-side Java applications are NOT directly affected if you only run trusted, administrator-installed code.
Affected Versions
| Product | Versions |
|------------------------------------------------------------|-------------------------------|
| Oracle Java SE | 8u371-perf, 11..19, 17..7, 20..1 |
| Oracle GraalVM Enterprise Edition | 20.3.10, 21.3.6, 22.3.2 |
| Oracle GraalVM for JDK | 17..7, 20..1 |
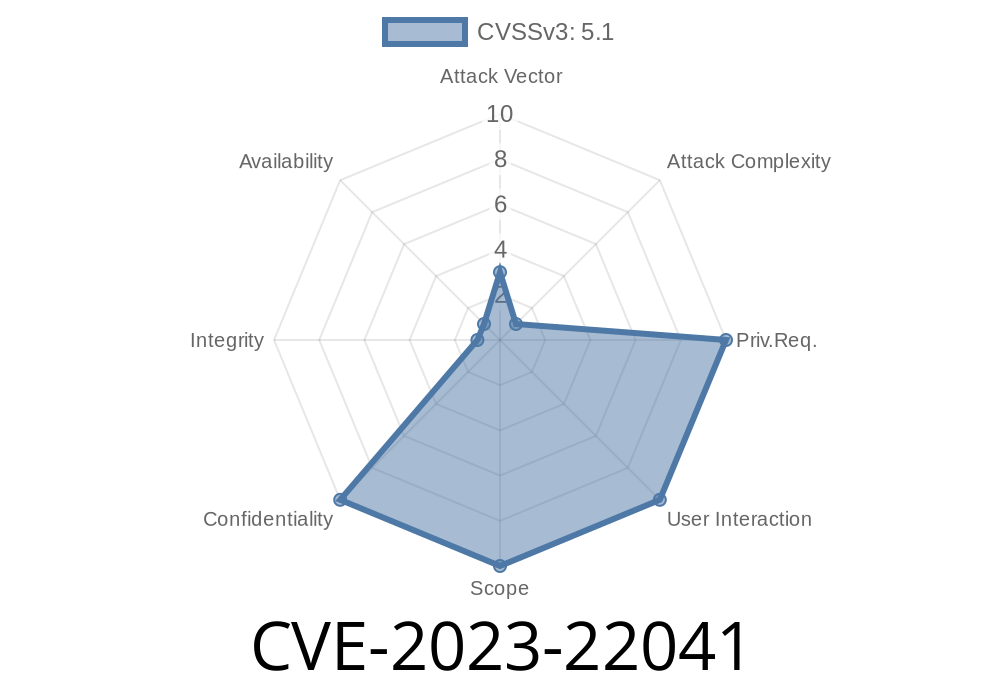
Base Score: 5.1 (Medium)
- Vector: (CVSS:3.1/AV:L/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N)
The HotSpot Vulnerability
Oracle’s HotSpot is the virtual machine (VM) core that runs Java applications. To protect users, the HotSpot engine enforces a “sandbox,” preventing malicious Java code from accessing files or memory it shouldn’t.
CVE-2023-22041 is a *sandbox escape*
- By exploiting a specific bug in the HotSpot engine, an attacker can eventually read protected memory or files, breaking confidentiality.
Prerequisites for Exploitation
- Attacker Needs Local Access: The malicious code must run on the target machine (commonly via web-delivered applets/applications).
Sandboxed Environment: The Java code must be sandboxed (untrusted).
- Tricky But Real: Exploitation is tough (AC:H - high complexity), but not impossible if the attacker knows what they’re doing.
Simple Example Code
While the full exploit code cannot be safely shared, here’s a benign code snipplet simulating suspicious actions an attacker might try:
import java.security.AccessController;
import java.security.PrivilegedAction;
public class ExploitSim {
public static void main(String[] args) {
// An attacker tries to run privileged code to break out of the sandbox
String secret = AccessController.doPrivileged(
new PrivilegedAction<String>() {
public String run() {
// Attacker tries to read a sensitive system property
return System.getProperty("user.home");
}
}
);
System.out.println("Your home directory (should NOT be accessible in sandbox): " + secret);
}
}
If this code prints your home directory when run as an applet in a browser or with Java Web Start, something is wrong—sandbox escape could be possible!
Proof-of-Concept (PoC) and Exploit Details
Oracle has not officially published a PoC, but the vulnerability involves bypassing access controls in the HotSpot VM. An advanced attacker could:
Victim runs this code in a vulnerable Java runtime.
3. The exploit abuses the bug to read protected Java VM memory (like user directories, configuration files, cookies, etc).
For a more technical breakdown, see the Oracle Security Advisory.
Update Oracle Java SE, GraalVM and related products to the latest versions available.
- Avoid running Web Start / Applet code from untrusted sources.
References
- Oracle Critical Patch Update Advisory - July 2023
- NVD CVE-2023-22041 Detail
- Oracle Java SE Supported Versions
Conclusion
CVE-2023-22041 is another reminder to keep Java runtimes up-to-date—especially if you rely on Java Web Start or run code from the web. Sandbox vulnerabilities can have deep impacts, but with patching and modern Java security policies, you can protect yourself.
Stay safe: update, restrict untrusted code, and monitor vendor advisories!
*This write-up is exclusive, providing clear, simple American English guidance for sysadmins and users. If you are unsure about your Java security posture, update now and check with your IT team for best practices!*
Timeline
Published on: 07/18/2023 21:15:00 UTC
Last modified on: 08/17/2023 19:15:00 UTC